ExtraHop Reveal(x)
Defending The Cloud
As you migrate more business-critical workloads to the cloud, there's pressure to move security with them. However, many organizations find their existing security processes leave visibility gaps, making it difficult to defend those workloads.
ExtraHop Reveal(x) 360 network detection and response (NDR) is tailored to combat advanced attacks in the cloud with unified visibility, threat detection, and response capabilities available in a single management pane.
ExtraHop Reveal(x)
Defending The Cloud
Here we'll show you a sophisticated attack that exfiltrates data to an AWS S3 bucket. The attack will run to completion in this scenario, but in reality, someone using Reveal(x) 360 would be able to stop the attack at any stage.
Note: This is a slideshow adaption of a scenario found on ExtraHop's live, interactive cloud demo. To experience the fully functional demo, visit extrahop.com/demo/ on any laptop or desktop device and choose Secure the Cloud.
Detection

Blue Team
Detection
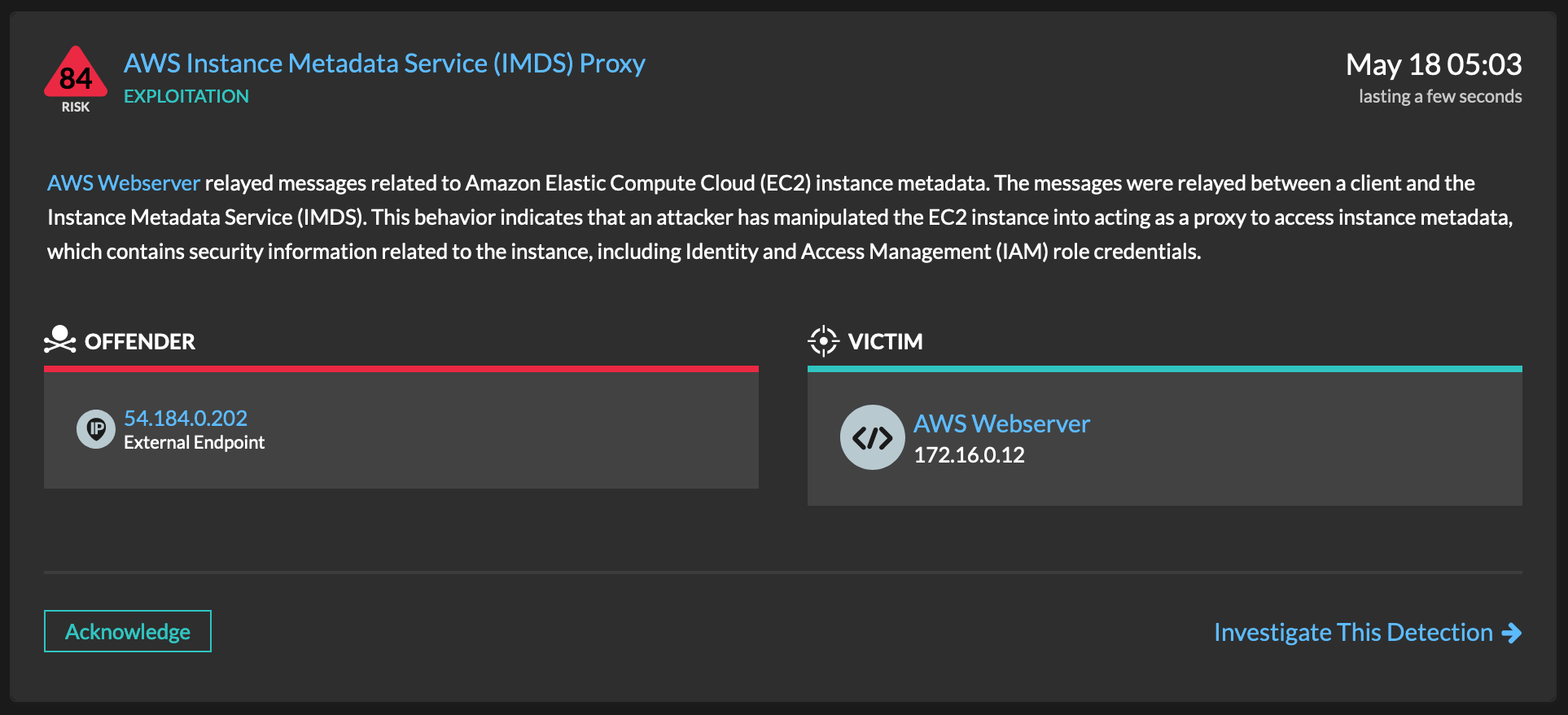
This detection catches a server-side request forgery (SSRF) technique.
The IMDS is an internal AWS service that provides sensitive data and credentials to most EC2 instances.
The SSRF technique enables the attacker to gain access to an environment with credentials obtained from IMDS.
The Attack Begins
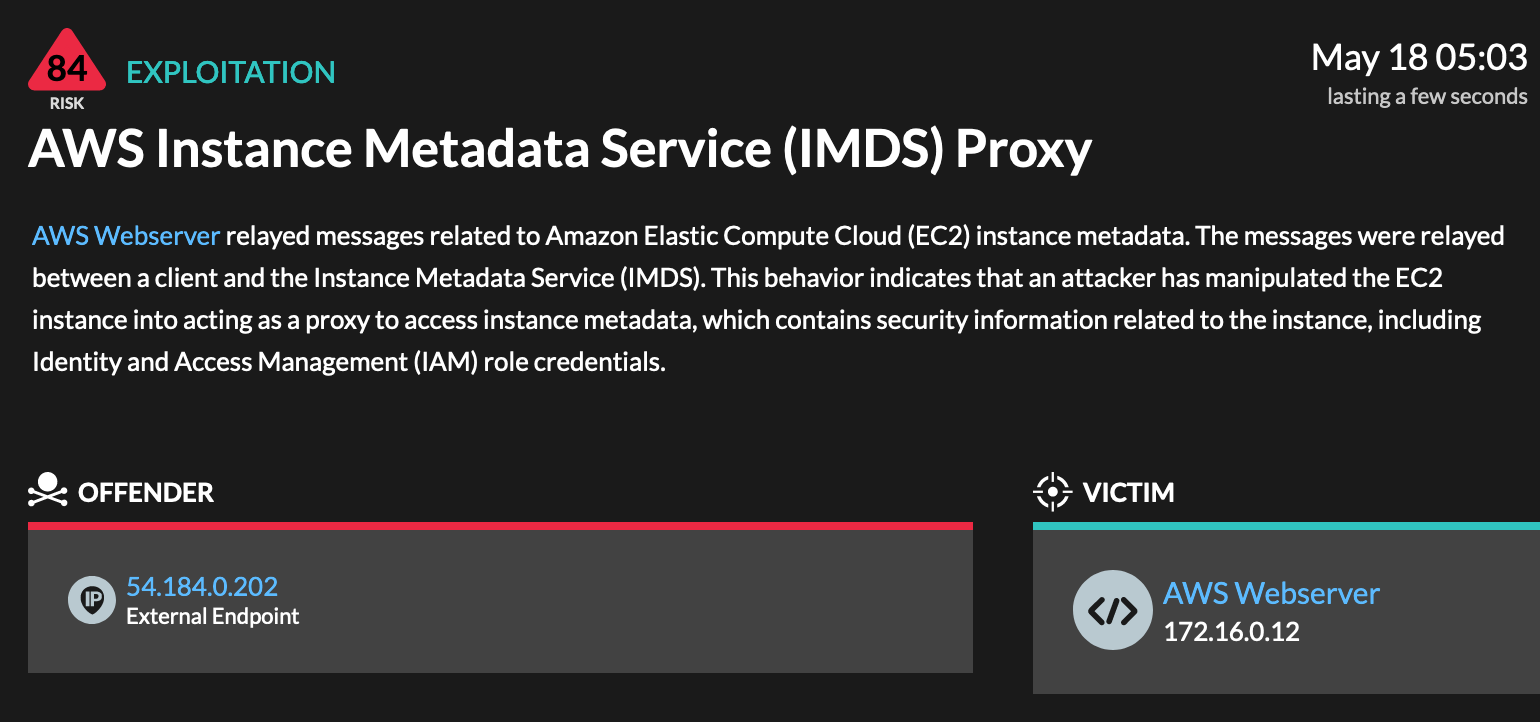

This detection catches a server-side request forgery (SSRF) technique.
The IMDS is an internal AWS service that provides sensitive data and credentials to most EC2 instances.
The SSRF technique enables the attacker to gain access to an environment with credentials obtained from IMDS.
Blue Team
The Attack Begins
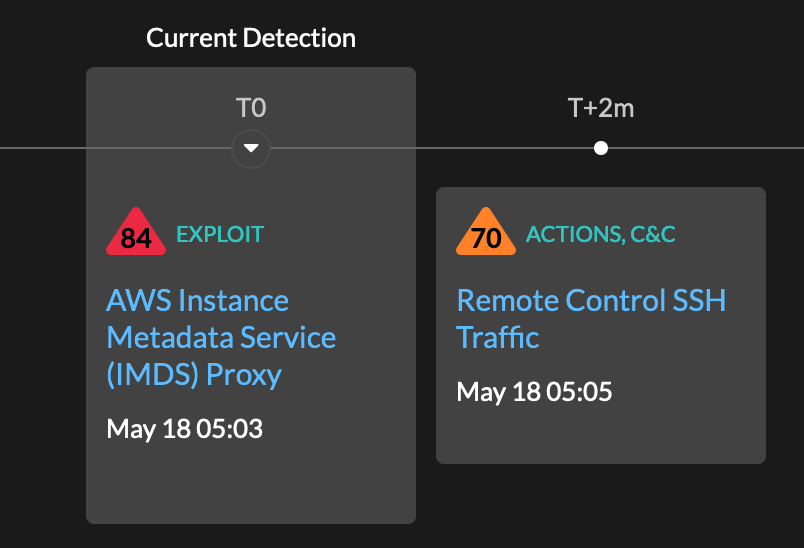
The attacker was successful and ambitious. The timeline shows that with the first set of stolen credentials, the attacker was able to gain additional credentials for access through a remote SSH session.
To learn more about the scale and scope of the attack, analysts can click into related detections. In this instance, we'll investigate the Remote Control SSH Traffic detection.
Check the Timeline

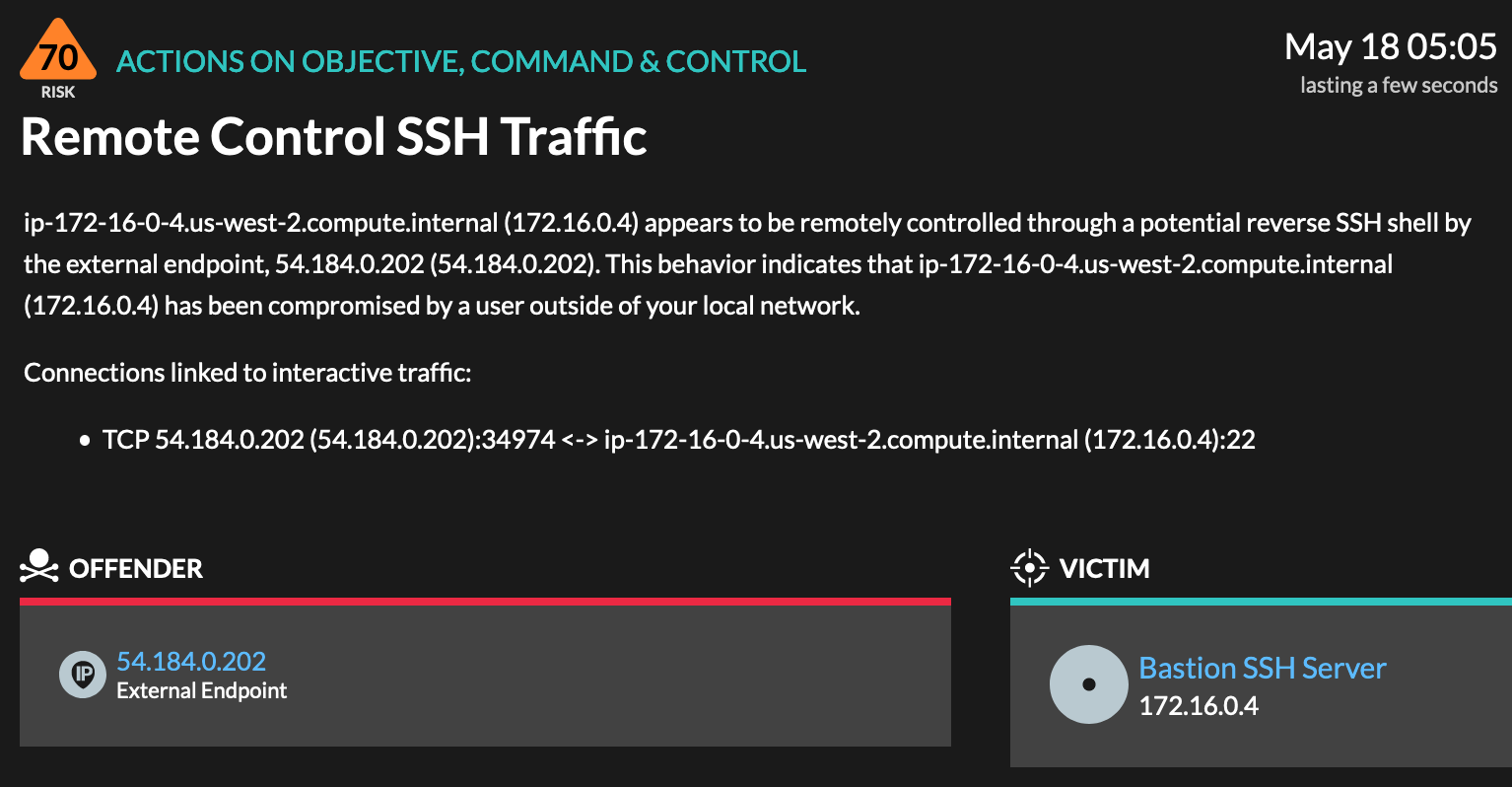
The attacker was successful and ambitious. The timeline shows that with the first set of stolen credentials, the attacker was able to gain additional credentials for access through a remote SSH session.
To learn more about the scale and scope of the attack, analysts can click into related detections. In this instance, we'll investigate the Remote Control SSH Traffic detection.
Blue Team
Check the Timeline
Attacker in Control

Blue Team
Attacker in Control
The bastion server becomes the offender in the next detection as the attacker moves laterally through the network.
By clicking on the AWS Cloud Service Enumeration detection, analysts can quickly investigate that aspect of the attack.
Role Reversed
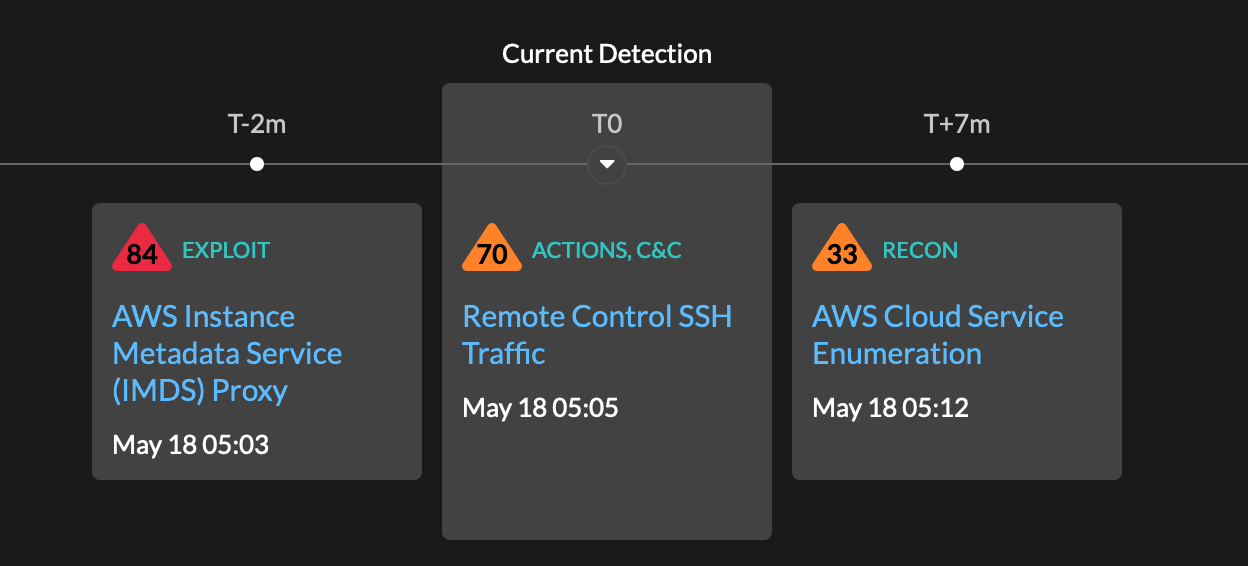

The bastion server becomes the offender in the next detection as the attacker moves laterally through the network.
By clicking on the AWS Cloud Service Enumeration detection, analysts can quickly investigate that aspect of the attack.
Blue Team
Role Reversed
Lateral Movement
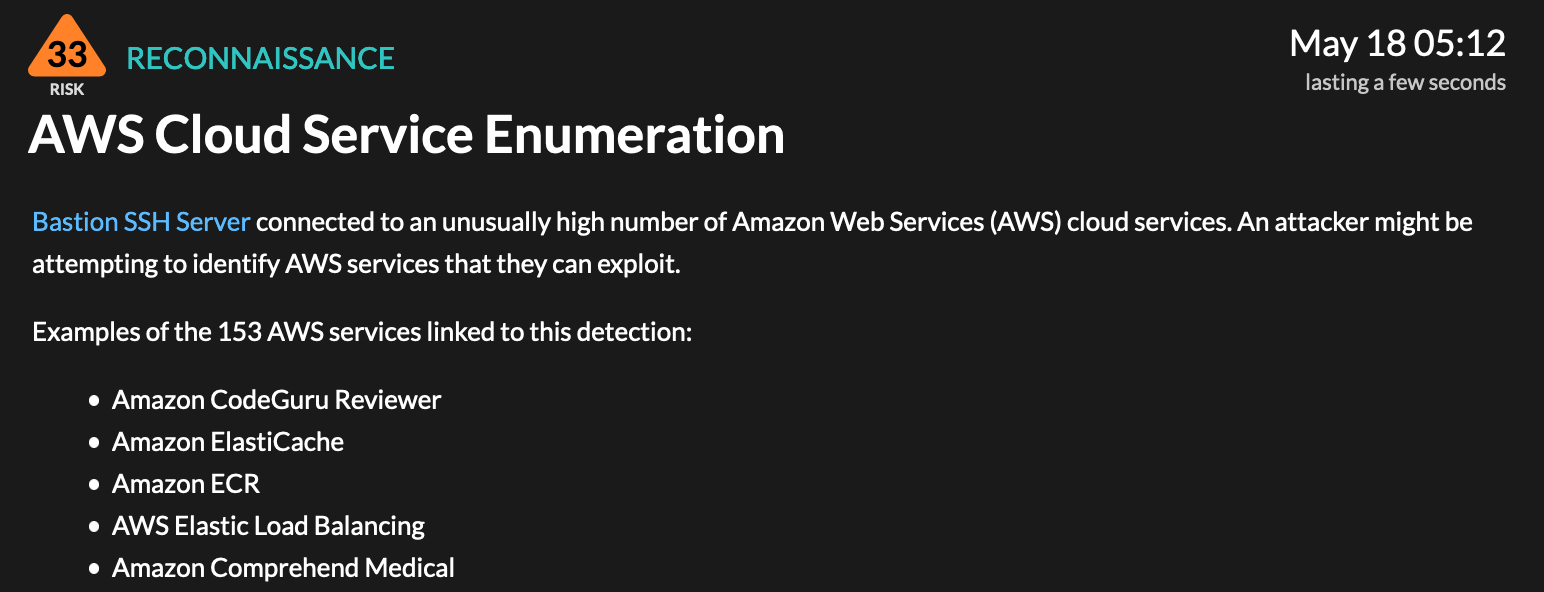

Blue Team
Lateral Movement
The attacker found a potentially valuable asset: an RDS instance. The attacker then pivots to a separate EC2 instance to get around the security policies.
By investigating the detection, an analyst can quickly determine what the attacker is up to in real time.
Target Acquired
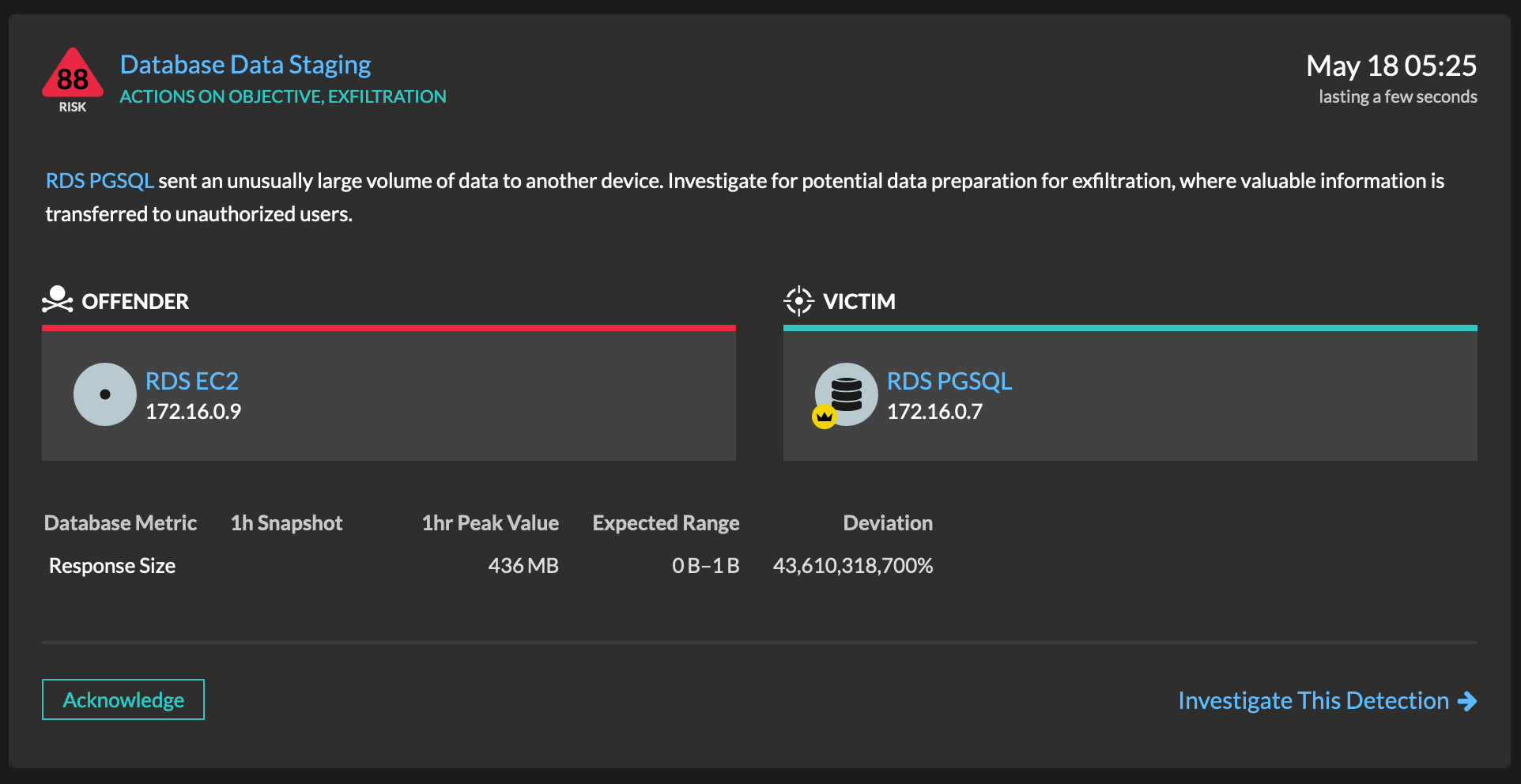

The attacker found a potentially valuable asset: an RDS instance. The attacker then pivots to a separate EC2 instance to get around the security policies.
By investigating the detection, an analyst can quickly determine what the attacker is up to in real time.
Blue Team
Target Acquired
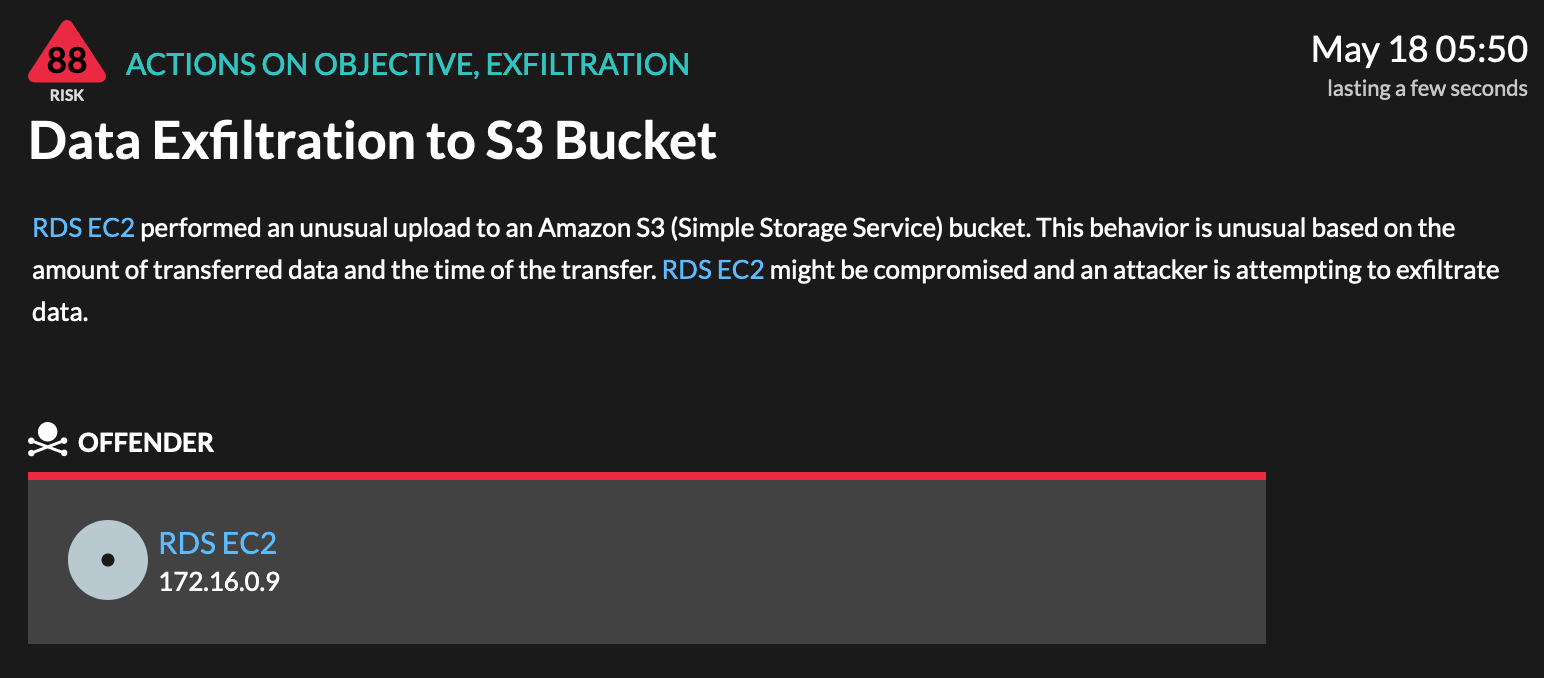
The writing is on the wall: The data is being moved to the attacker's S3 bucket.
By clicking into the Data Exfiltration to S3 Bucket detection, an analyst can continue gathering information about the attack.
Back to the Timeline
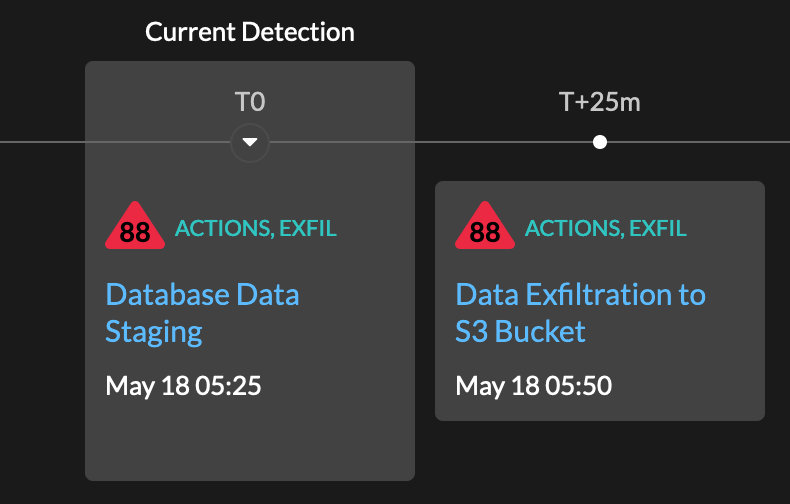

The writing is on the wall: The data is being moved to the attacker's S3 bucket.
By clicking into the Data Exfiltration to S3 Bucket detection, an analyst can continue gathering information about the attack.
Blue Team
Back to the Timeline
Attack Complete

Blue Team
Attack Complete
Explore the Reveal(x) 360
Fully Functional Demo
Now that you've seen how Reveal(x) 360 helps you detect and respond to threats in real time, use the link we sent to your inbox to explore the fully working product demo from your desktop or laptop. Or take it a step further and request a free 15-day trial of Reveal(x) 360, SaaS-based NDR.
Introduction
The Attack Begins
Attacker Gains Access
Target Acquired
Exfiltration

Defending the Cloud
