
This post is written by Cal Jewell, a Senior Technical Trainer at ExtraHop.
In June, Microsoft announced that it would release an update blocking the use of RSA keys using less than 1024-bit encryption. While the update has been available for testing, the October 9 "Patch Tuesday" will make the update widely available via Windows Update. The update effects all supported versions of Windows, going back to Windows XP SP3. If servers or clients continue to use sub-standard key encryption after October 9, then a range of potential problems could result, including blocked access to SSL-encrypted websites from Internet Explorer, problems installing ActiveX controls and Windows-based applications, and the inability to encrypt or digitally sign e-mail using Microsoft Exchange and Microsoft Outlook. As security experts at the SANS Internet Storm Center point out, this update will not only affect certificates from Microsoft and other well-known authorities, but internal certificate authorities, too.
Find All the Certs … Before Patch Tuesday
System administrators have one month to find all the servers and clients using too-small cryptographic key sizes and update the certificates. To discover the use of RSA keys under 1024 bits, Microsoft recommends turning on verbose (CAPI2) logging on the relevant computers and then checking back after a period of time. They also recommend checking certificates manually(!). Sound like a pain? It is.
To find sub-standard certificates, Microsoft recommends turning on verbose logging on relevant computers.
Thankfully, the ExtraHop system offers an easy way to track the usage of all SSL certificates used in your environment in just a few clicks. First, go to the SSL Server or SSL Client Activity Group and adjust the time interval to something reasonable, say the last seven days. Now click Certificates at the top to view all the SSL certificates used. Filter the results by entering "512" and you have a list of sub-1024-bit certificates for the time interval.
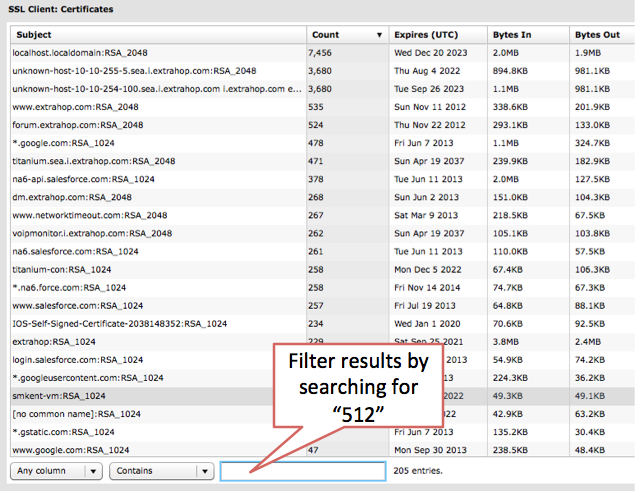
The ExtraHop system automatically analyzes the SSL envelope for all network traffic, including key sizes.
Alleviating the Compliance Burden
The SSL-envelope analysis capability in the ExtraHop system also tracks expiration dates for SSL certificates and protocol versions for both servers and clients. This is helpful for administrators that must accommodate government or industry regulations. For example, the U.S. National Institute of Standards and Technology (NIST) is drafting new guidelines for federal agencies to stop using TLSv1. The ExtraHop system gathers this information passively off the wire, as shown in the screen capture below.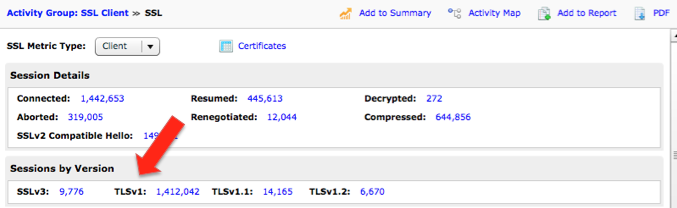
The ExtraHop system tracks the versions of cryptographic protocols used in enterprise networks.
Another strong example is federal agencies that must transition internal client applications and enterprise networks to operationally native IPv6 and then prove compliance. The DNS Client and DNS Server Activity Groups in the ExtraHop system track all hosts (and IPs) that have made or answered IPv6 DNS lookups. Federal IT managers responsible for IPv6 transition can schedule automatically generated PDF reports based on these lists to show compliance. And, with the Splunk App for ExtraHop, they can also forward every IPv6 DNS lookup and response to Splunk for historical analysis and storage.
ExtraHop Helps Make IT Management Easier
Certificate management and standards compliance are two examples of the mundane but necessary burdens weighing on the shoulders of today's IT organizations. And yes, these issues can affect application performance as experienced by users—the Microsoft update amply demonstrates that. Agent-based application performance management (APM) tools offer no answer for these types of systemic application performance problems, but a network-based view of application health and performance does. This is one more reason why network-based APM is a must-have for today's IT Operations teams.You can try out the ExtraHop system for yourself with a free, 60-day trial download. This version does not include SSL-envelope analysis, but our paid offering supporting up to 50 servers starts at just under $7,500—roughly one-tenth of what you would pay for the first year with an agent-based solution.
