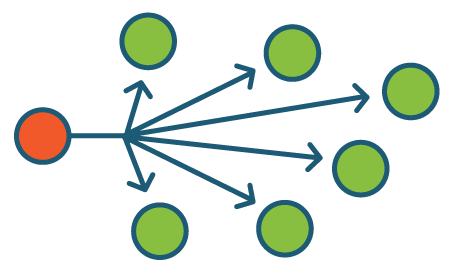
Unicast flooding occurs when a switch receives a packet whose destination address it doesn't know, so it broadcasts the packet to every possible destination.
Successful unicasting is a lot less work for the network than a unicast flood.
The term unicast refers to the network distribution method of sending messages from a sender to a single destination. For this to happen, the sender - in this case, a switch - needs to have an entry in its forwarding table that maps the MAC address of destination device to the port where it resides. When a switch receives a packet whose destination MAC address is not present in its forwarding table, its solution is to "flood" the packet out of all of its ports that belong to that layer 2 broadcast domain (VLAN). In addition to being a potential security risk, this can significantly reduce network efficiency if it occurs frequently. Unicast flooding can also be a sign of a MAC flooding attack.
Monitoring your network for unicast flooding can help you pinpoint network problems as soon as they occur and protect the security of your system and users.
When Is Unicast Flooding a Problem?
Unicast flooding, while usually an innocuous and expected behavior, can indicate problems in your network configuration if it occurs in excess. High levels of flooding can degrade network performance in terms of latency and packet loss, especially for low-bandwidth systems. Here are a few of the most common causes of unicast flooding:
1. Asymmetric Routing
If there are two paths through the network connecting hosts 1 and 2, and packets sent from each host take different paths, unicast flooding would occur when either host sends a packet to the other. Specifically, if host 1 connects to switch A via, VLAN1, and host 2 connects to switch B via VLAN2, when host 2 sends a packet to host 1, that packet will be flooded to VLAN1, because switch B doesn't know which port to use to reach host 1. The same situation would occur for packets sent in the opposite direction.
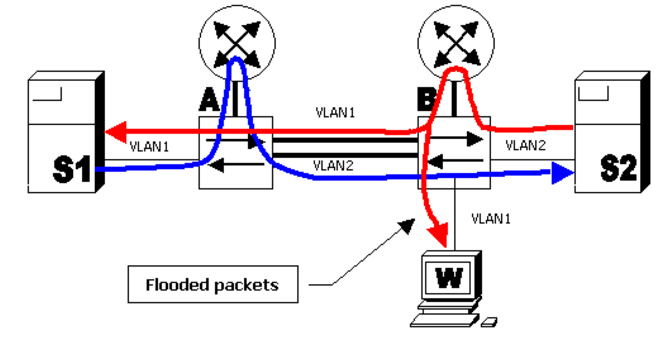
Unicast flooding can be caused by asymmetric routing.
To limit unicast flooding in this situation, set your router's ARP timeout slightly shorter than the timeout for the switch's address table so that most entries are relearned before the switch ages them out.
2. Forwarding Table Overflow
If a switch's address table is full and it receives a packets destined for any host whose MAC address isn't in its table, it is forced to flood the packets until there is space in the address table to store the new address associations.
This can also be caused by a type of network attack called a MAC flooding attack. This attack involves a malicious host flooding the switch with frames that have fake MAC addresses to completely fill the address table so that all other traffic will be flooded from all ports and can be observed by the attacker.
Methods of preventing MAC flooding attacks include enabling port security on a switch to limit the number of MAC addresses learned on certain ports and increase the timeout period of known addresses in the table, as well as verifying MAC addresses against an AAA server.
3. Network Topology Changes
If a link on a network goes down or if a new port opens for forwarding, address tables need to be updated since paths to some destinations may have changed. Since the length of time that entries in the table normally take to age out is longer than would be ideal for these events, a Topology Change Notification (TCN) is triggered on networks using the Spanning Tree Protocol (STP) to age out table entries more quickly so the forwarding table stays up to date. A side effect of aging out entries is increased unicast flooding until addresses are relearned.
Unicast flooding due to TCNs doesn't usually last long. However, it can be problematic if multiple TCNs are occurring over a short period of time. On Cisco switches, you can use the PortFast command for ports that are only connected to end stations which go up and down often. This causes the port to go directly to forwarding mode, bypassing the learning and listening states and preventing a TCN when the port goes up or down.
For a more detailed explanation of topology changes, check out this article on the topic.
4. Unidirectional Protocols
Unidirectional or connectionless networking protocols such as the User Datagram Protocol (UDP) can also lead to unicast flooding since they don't require acknowledgements or responses from the destination application. In a situation where one system sends packets to another over a long period of time without getting any packets in return from the receiver, the switch connecting the two systems will eventually age out its entry for the destination, so any further packets from the source to that destination will result in unicast flooding.
The Transmission Control Protocol (TCP), a connection-oriented protocol, avoids this potential pitfall by requiring acknowledgements to be sent back to the source for data that the destination receives successfully.
How You Can Monitor Unicast Flooding
If you're not an ExtraHop user yet, check out our interactive online demo and see its capabilities for yourself.
