There's a better way.
[Update: ExtraHop's plug-and-play Ransomware Bundle won Best of Citrix Synergy 2016, plus Best in Application, Network, and Data Security!
So by now, you've no doubt heard about one form or another of ransomware. It is the big topic of 2016 on the minds of all CIOs, CISOs, and many other IT practitioners.
As the trend of attacks continued to escalate throughout 2015 (as well as into 2016), many of us ExtraHoppers began working with our respective clients to provide insight here. As a result, we've developed an add-on ransomware bundle for the ExtraHop platform oriented around providing:
- Real-time detection of ransomware attacks, as they happen.
- An easy-to-use forensic trail for understanding the origin of these attacks.
Within the sphere of available Information Security products on the market, thus far it has proved to be exceedingly difficult to detect and block ransomware attacks. Most of the traditional approaches to stopping ransomware focus on protecting the perimeter and screening for known, bad IP addresses, URLs, emails, and DNS queries. The problem with this approach is that these origination vectors change constantly, even throughout the course of a single day. So blocking an individual DNS request, or a particular Internet IP has proven to be fairly unreliable in stopping new variants of (crypto) ransomware.
The ExtraHop Ransomware Bundle was designed from the ground up to focus its analysis exclusively on the behavior of storage READ and WRITE operations (for SMB/CIFS in particular) within the enterprise. And although the ExtraHop platform is not an in-line device, capable of blocking traffic, our Ransomware Bundle has been met with rave reviews from numerous existing customers. Via behavioral analysis of SMB/CIFS activity, we can provide real-time early detection of ransomware attacks in progress. And with this early detection, you can quickly stop ransomware attacks in flight, before serious damage is done to corporate data or applications.
So how does the ransomware bundle work, you might ask? Well, without going into too much of the secret sauce, I can point out a handful of techniques that we are employing today. ExtraHop can detect and alert on the following anomalous behavior in real time:
- Are storage traffic volumes increasing abnormally for specific client devices?
- Are there particular SMB/CIFS operations (e.g. WRITES, RENAMES, DELETES) that show abnormal behavior?
- Does your storage activity involve valid data types (e.g. Word/Excel documents) or invalid data types?
- Are the tell-tale signs of ransomware (e.g. ransom notes) left behind?
- Any combination of the above
These are just a few of the behaviors the ExtraHop product can use for real-time detection of ransomware attacks. So long as you are dealing with a "crypto-ransomware" variant (i.e. a ransomware malware that encrypts files) and that variant attempts to encrypt files on Network Attached Storage (i.e. your shared network drives), then the ExtraHop platform can do a fantastic job of detecting this abnormal behavior.
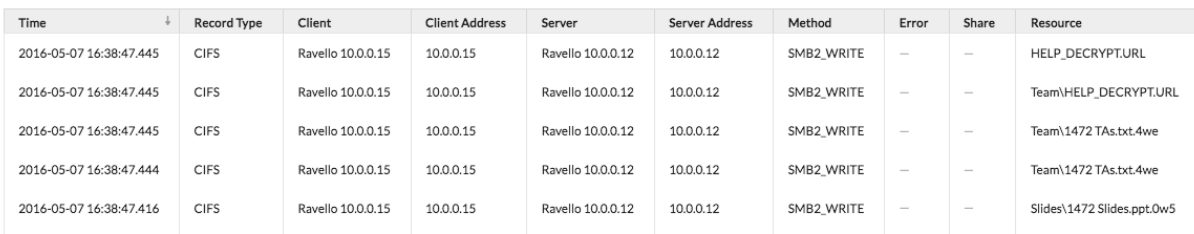
In the process of building the ransomware bundle, we've had quite a bit of "fun" purposefully infecting some test machines with variant ransomware types. Let's take Cryptowall v3.0 for example: Our ransomware bundle successfully detected the anomalous behavior of this well-known (and quite destructive) variant of ransomware, which encrypts files and ultimately rewrites file extensions using completely random character patterns (e.g. tompresentation.ppt was renamed to tompresentation.ppt.0we). After encrypting the files, it also leaves behind "ransom notes" (typically a text file or equivalent) in each directory that was encrypted.
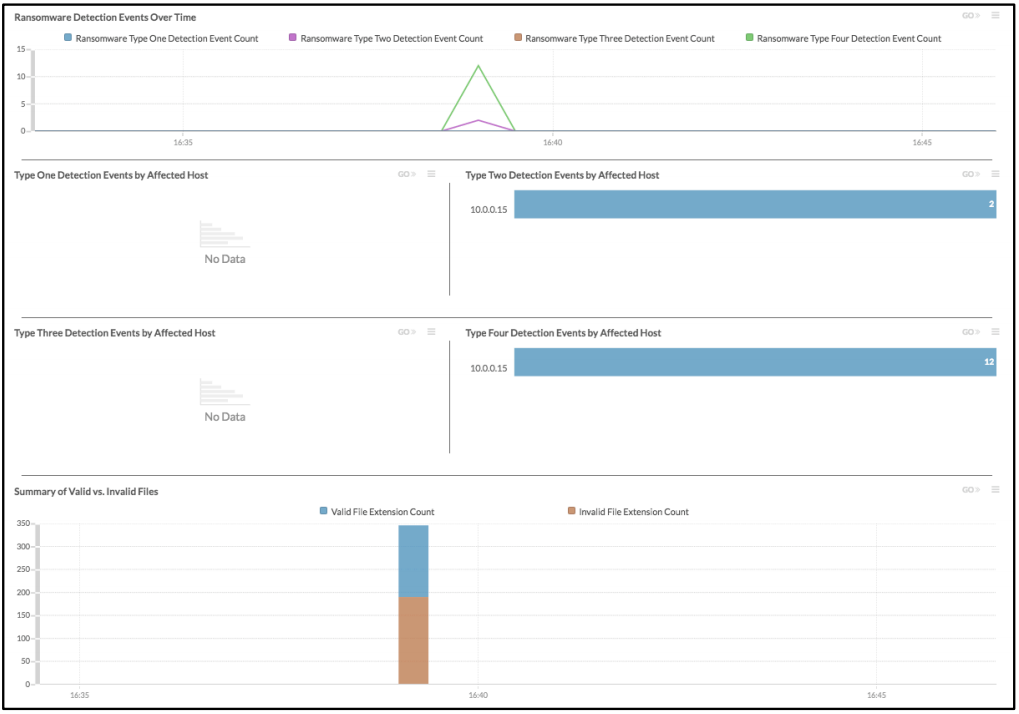
In this situation, ExtraHop successfully detected the presence of abnormal file extensions, the presence of the ransom notes, and the abnormal spike in CIFS WRITE activity. With ExtraHop's automated detection here, we can display and alert you to this type of unusual activity very quickly, which can make all the difference in the world. With early detection, you can likely avoid having to pay the ransom, and you can perhaps prevent key applications (such as Electronic Medical Record and ERP systems) from cratering.
Ransomware detection dashboard.
CIFS activity details for a Cryptowall v3.0 attack in progress.
After we successfully detected the Cryptowall v3.0 attack and stopped it, we then went back into ExtraHop and quickly searched through all transaction/flow history for the infected workstation. We then identified the origination point of the malware (a particular web site), accompanied by various C&C (Command and Control) traffic, and we were able to deploy firewall rules to prevent further drive-by infections from that malicious web site.
To date, we've had a number of existing customers stop ransomware infections COLD ... in their tracks. You can too, and we'd love the opportunity to show it to you. Drop us a note to schedule a demonstration today!
I'll go into more technical details involving usage and configuration of the ransomware bundle in a future post. If you're an existing ExtraHop customer, you can download the ransomware bundle on our Bundles Gallery.
Next up, read a true story of how we helped a healthcare coverage provider stop a ransomware attack in progress.
Good luck hunting!