Cisco's Tetration announcement just over a year ago emphasized the powerful role analytics will play in IT Operations. The network is the common denominator of our digital, interconnected world, containing a wealth of insight into data flows as well as the health of clients, servers, and applications. As the common denominator, and with more frequent news of security breaches and ransomware attacks, the network has become increasingly critical when it comes to quickly preventing and minimizing these attacks. Combining ExtraHop's real-time wire data analysis and Cisco Tetration's security policy enforcement allows you to detect and take rapid action on these security threats.
How Does It Work?
Tetration's visibility into traffic flows provides a view into data center clients, servers, and applications that results in extensive application mapping. This allows you to analyze your data center traffic in order to develop your security policies and micro-segmentation plans—such as segmenting your application servers from your database servers and external clients, or applying appropriate firewall policies at your endpoints immediately and automatically.
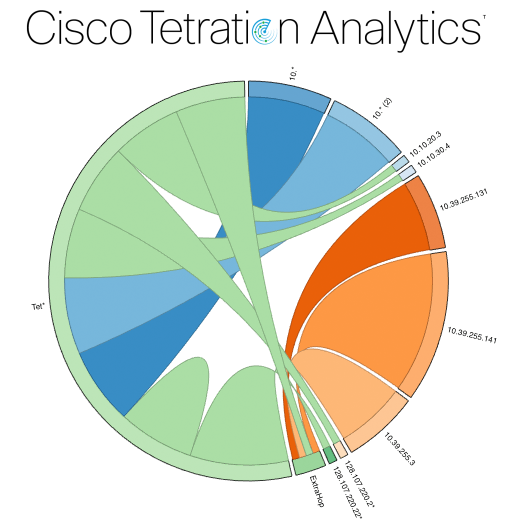
ExtraHop's unique real-time application layer visibility and deep analysis of the data in flight allows us to detect security issues as they happen. A perfect example of this is our industry-leading and award-winning ransomware detection bundle. The ExtraHop Tetration integration leverages the ransomware detection bundle to detect ransomware activity as it happens.
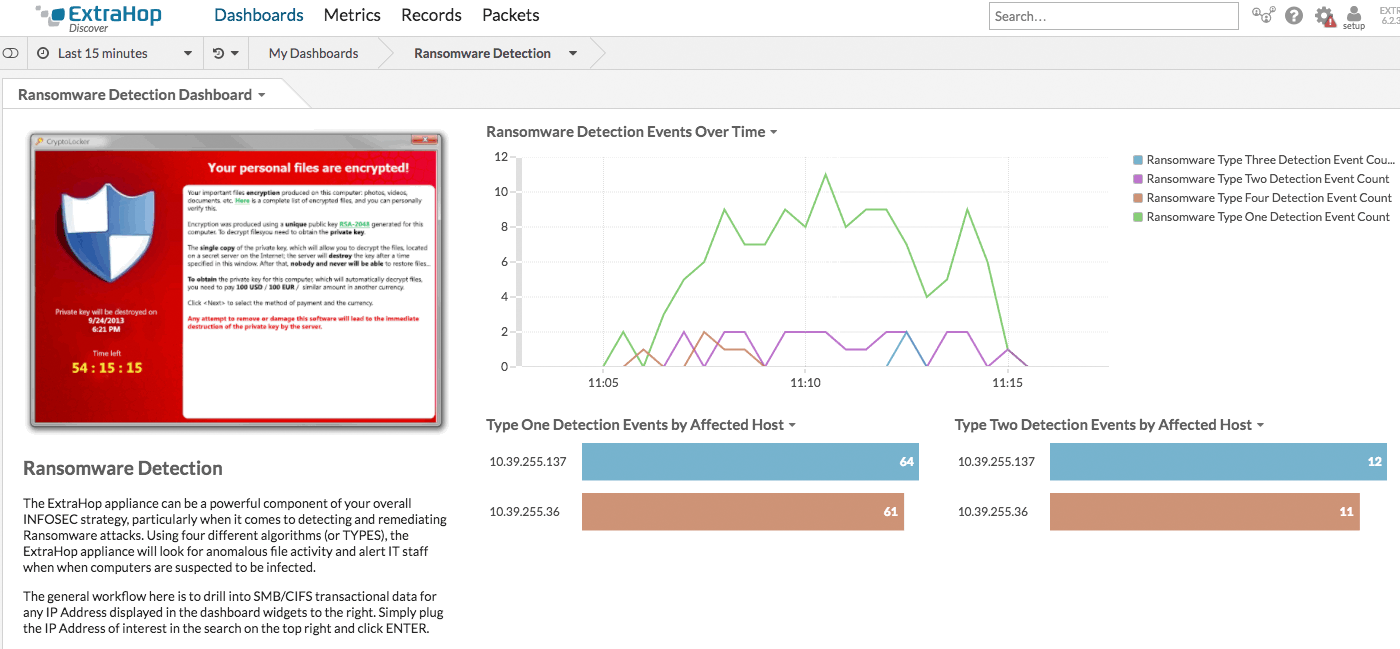
When ExtraHop detects a ransomware attack, our integration immediately applies a ransomware annotation (also referred to as a security tag) to the compromised endpoint in Tetration.
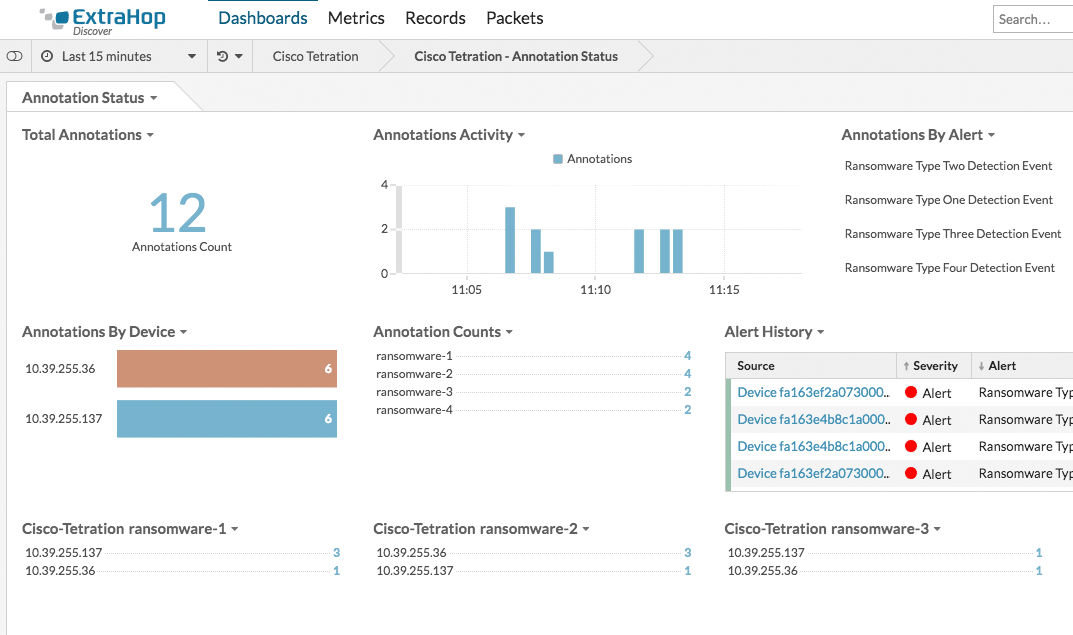
Tetration then instantly applies a security policy that disables the relevant ports to stop the attack. This happens in milliseconds, thereby securing your network to prevent damage to your network and, more importantly, damage to your business.
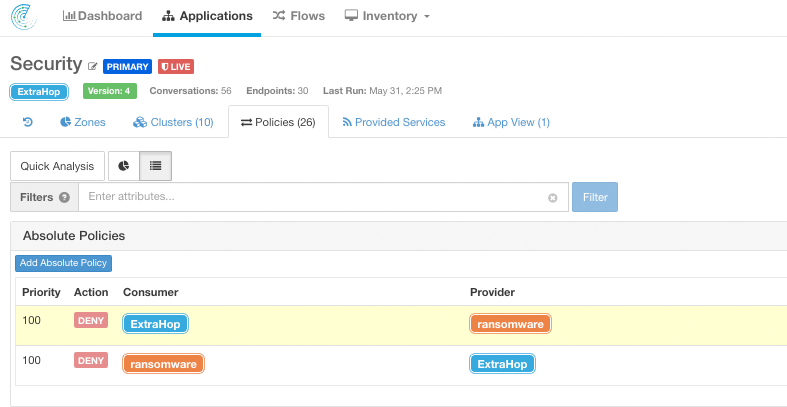
An additional benefit that ExtraHop provides is network forensics. ExtraHop and Tetration stopped the attack. Now, you can go back into ExtraHop to perform your security investigation. ExtraHop has all the transactions and packets you need to answer the who, what, and when of the attack.
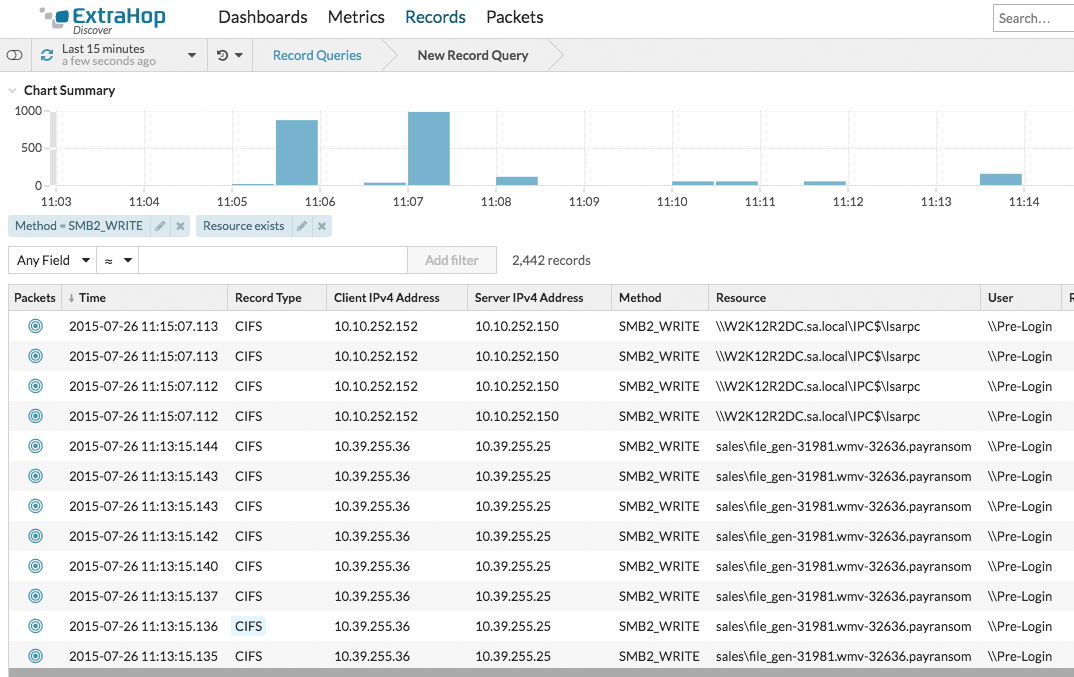
This is merely the beginning of our Cisco Tetration partnership. We have big plans for more features and capabilities to protect your data center.
ExtraHop has been a long time Cisco Technology Partner and our integration with Tetration is another milestone in this close partnership.
To learn more about the Cisco Tetration and ExtraHop integration, stop by booth #329 at Cisco Live in Las Vegas!