The new ExtraHop Threat ID bundle analyzes east-west traffic looking at common threat vectors including expiring certificates, weak ciphers, questionable DNS activity, and several types of scans. This analysis allows you to proactively identify and react to potential security issues that are present on your network. Let's have a look at the dashboards included in the bundle and get an idea of the insights that you can gain from each.
Threat ID Overview
Certificates
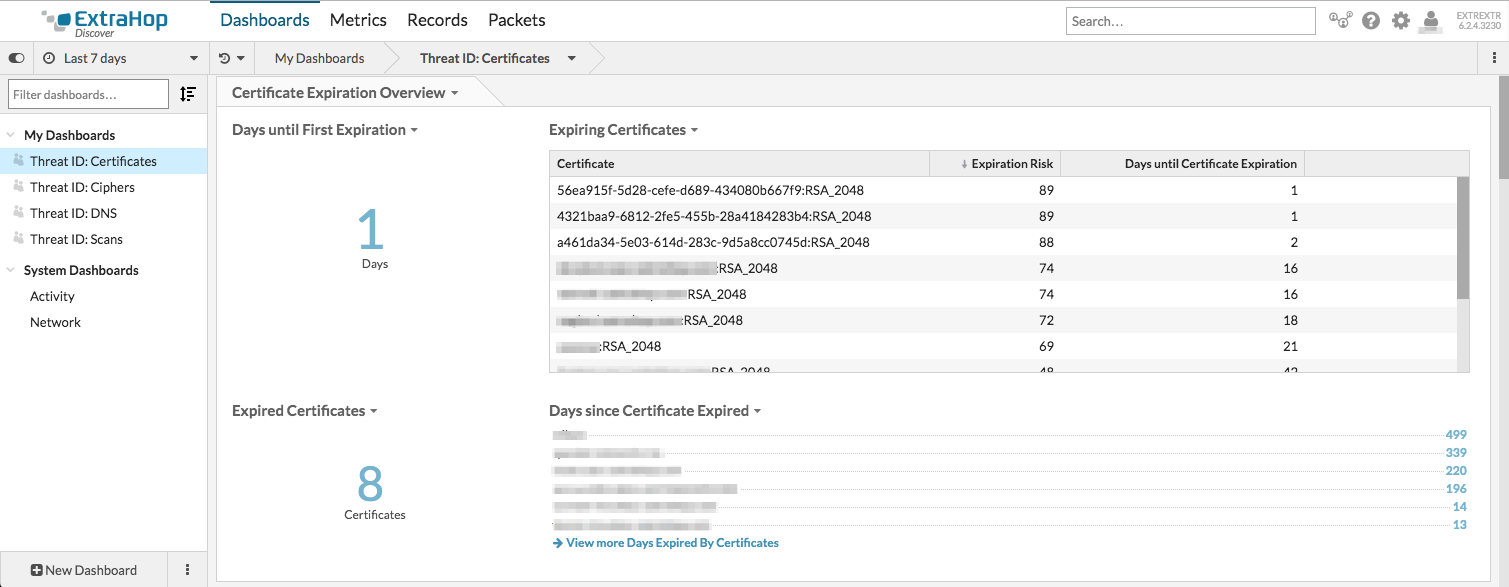
Have you ever had a certificate expire without you even noticing until it was too late? Well now you can easily track soon to expire, already expired, wildcard, and long-lived certificates on your network passively. You can view how many certificates will expire within the next 90 days, how many days until each certificate will expire, certificates that have already expired but are still being used, and more. You can drill down on an expiring/expired certificate and find out how many sessions are connected with that certificate or exactly which servers are using it.
This all allows you to keep track of certificate expirations and help avoid having an expiring certificate slip by your radar and expire without you being prepared.
Ciphers
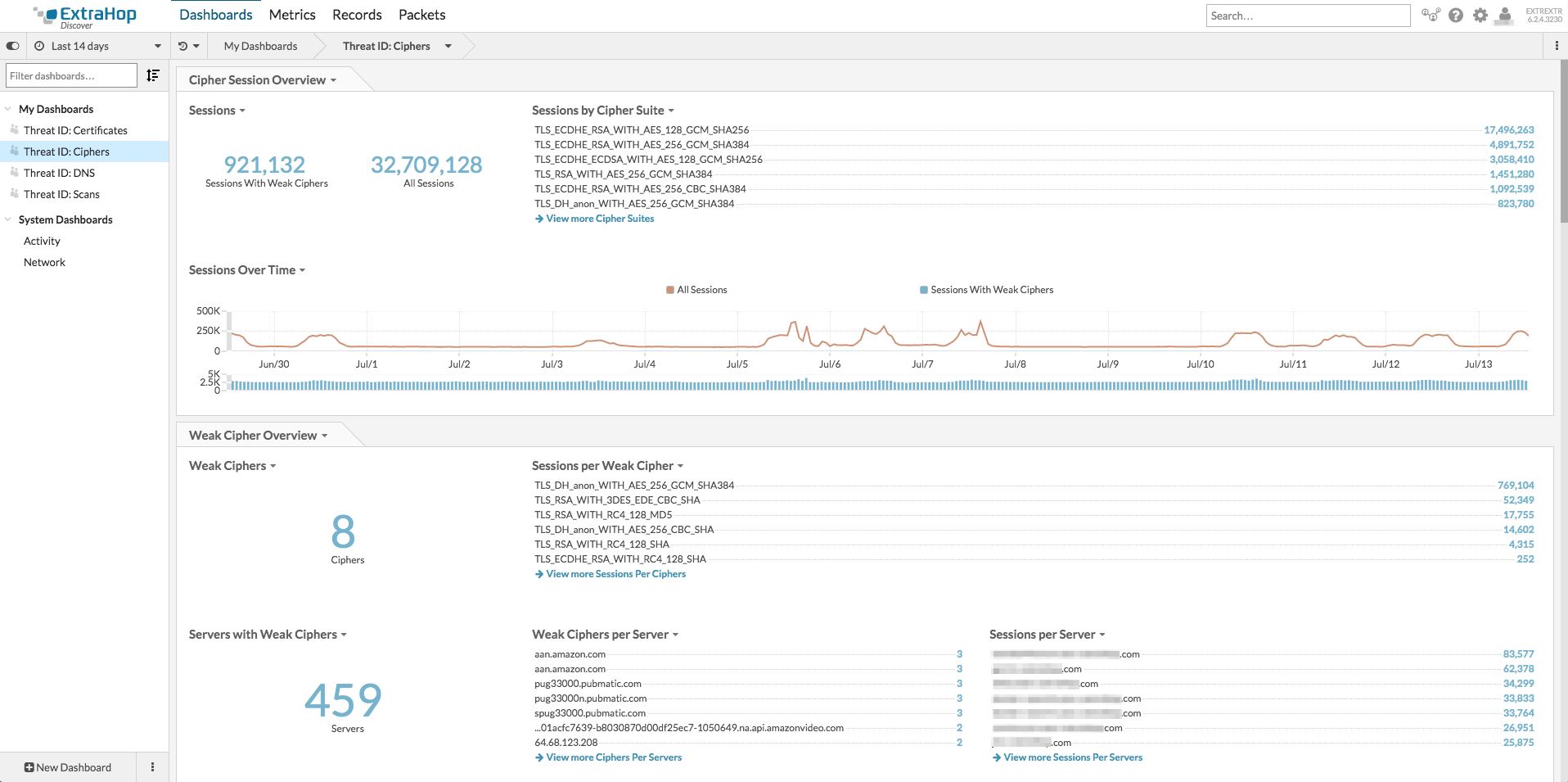
Gain in-depth visibility into the usage of weak cipher suites on your network. Cipher suites are considered weak when they use DES, 3DES, RC4, EXPORT, or NULL level encryption; ciphers that use Anonymous Authentication or MD5 for hashing are also considered weak.
You can view weak ciphers by server, client, or certificate as well as see all of the sessions connected per server, client, or certificate to identify who is using weak ciphers and how they're being used on your network. This information can then be used to identify which certificates should be updated to use stronger ciphers suites.
DNS
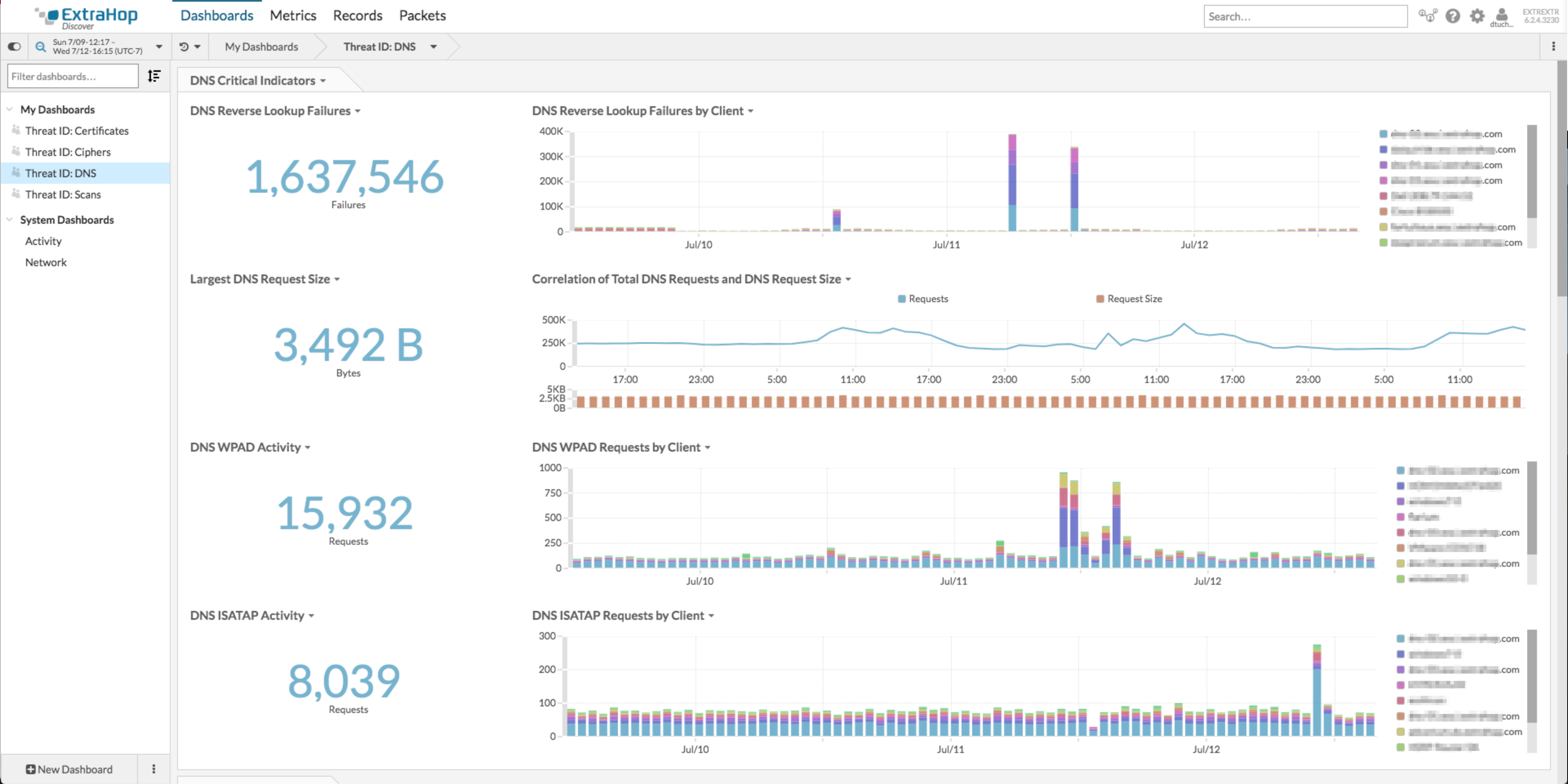
Track questionable DNS activity such as WPAD, ISATAP, and unusually large sized requests as well as DNS errors and request timeouts on your network. It's important to note that some of the indicators of a threat for DNS are normal on your network, but a sudden or steady increase in failures/errors on a specific host might indicate that an attacker is scanning your network.
Take the following screenshot for example, does the number of DNS reverse lookup failures by client look oddly high at times to you?
Those spikes in client failures would definitely warrant an investigation into the cause. In this case it was an nmap scan doing reverse DNS lookups programmatically on the network to identify endpoints, which caused a lot of reverse DNS lookup failures in the process.
Scans
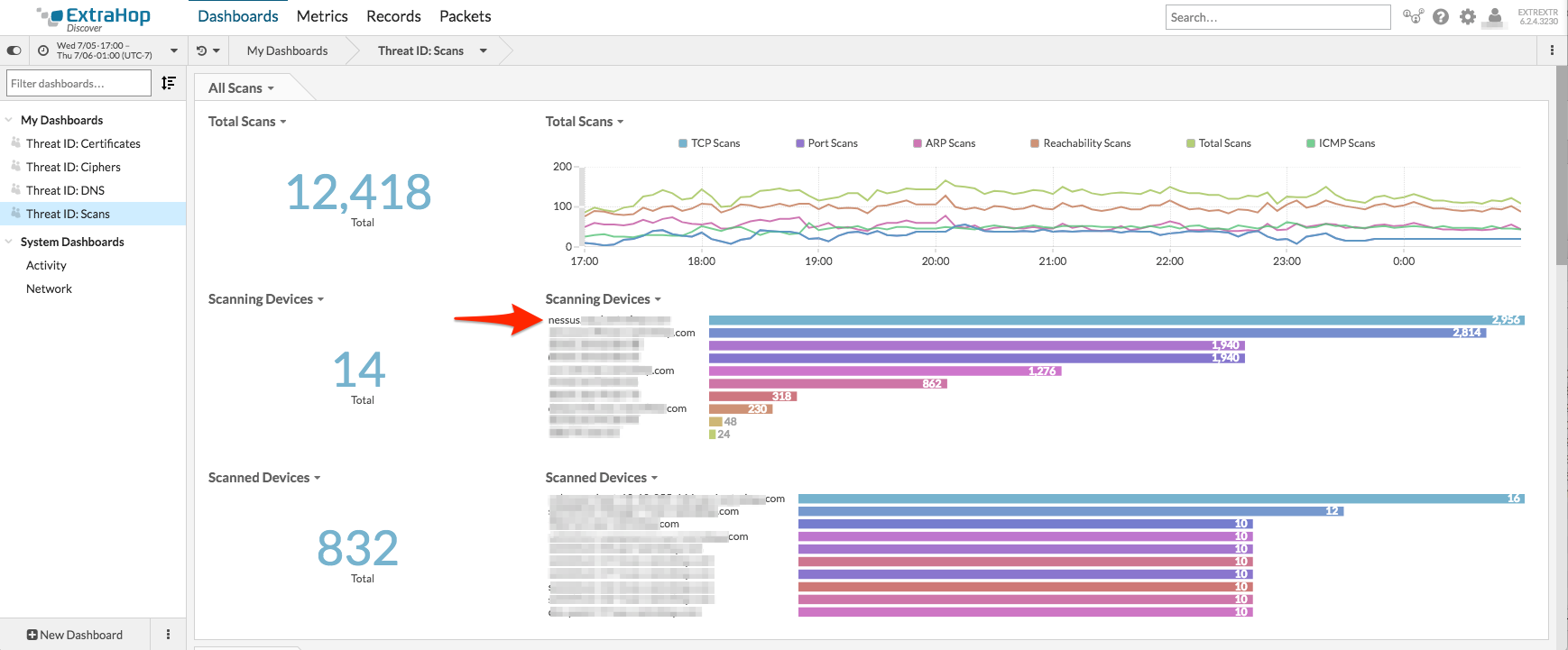
View both reachability and port scans that are occurring on your network real-time to identify potential threats and actors. We currently track several types of ARP, ICMP, and TCP scans. Although all of the aforementioned types of traffic can occur regularly on your network, if you see a spike in any particular type this could indicate a scan is occurring and is worth investigating further.
For example you can see in the screenshot below that the scans dashboard was able to identify that our internal nessus vulnerability scanner was actually completing a scan on the network.
This bundle brings together the information needed to proactively identify several potential security issues that are present on your network in real-time and give you the tools to investigate these threats further.