There is a new remote-code execution vulnerability for Apache Struts 2 (CVE-2018-11776)—with exploit code out in the wild—that should be of utmost concern for organizations using that software. One of our team downloaded the python script and tried it out. He was able to able to actually install an application, kill processes, and open a shell with it.
The good news is that there is a patch available, but as Apache Struts is often used at the core of sophisticated custom software, many organizations are not able to quickly or easily able to patch immediately.
As they work to get their software patched, ExtraHop customers can detect indicators of compromise for the exploit in real time and kick off orchestrated workflows, if desired. You could do this through Application Inspection Triggers or by simply running some transaction record queries.
The sample exploit code always uses the string java.lang.Runtime@getRuntime().exec. So simply searching HTTP transaction records for this string or even part of it, such as java.lang.Runtime, should work to detect the attack. It's worthwhile to note that attackers could encode the URI in other ways, such as java.lang.Runtime@getRuntime%28%29.exec, so using the shorter string is safer.
There are other ways you could strengthen detection of the exploit. A URI with large response size and receives a 200 code would give you even more confidence that your site was compromised.
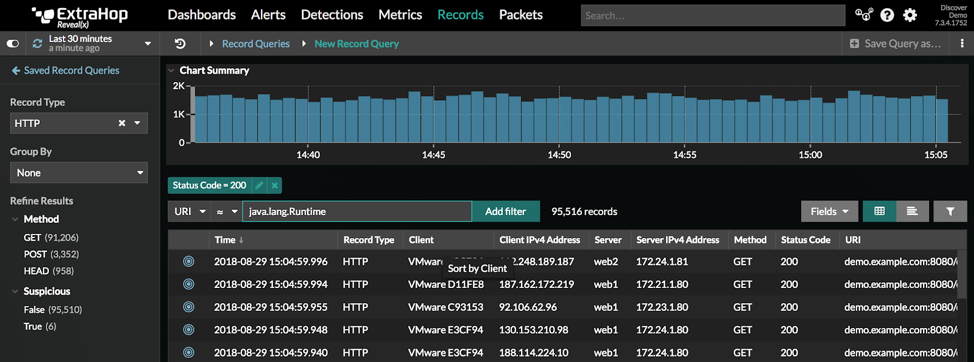
If you're new to ExtraHop, here's how the transaction record query works:
- Click on the Records tab at the top of the UI
- In the left hand navigation pane, filter the Record Type by HTTP
- Add a filter where the URI field equals
java.lang.Runtime - Sort by Response L2 Bytes to see the largest responses (you may need to scroll to the left to view more fields)
- Once you have your query defined, click Save Query as … at the top right of the page to keep this criteria to view later
Questions? Check out the online documentation for how to use the transaction record query capability.
