The largest DDoS attack ever recorded (1.35 Tbps) was just announced using memcache as a UDP reflection attack vector against Github. The US-CERT and other organizations just earlier this week had published critical alerts emphasizing the importance of detecting and mitigating UDP reflection attacks like Memcrashed (using memcache), which permits amplification attacks almost three orders of magnitude greater than previously considered.
Distributed Denial of Service attacks are nothing new, but the ever-increasing prevalence of uncontrolled cloud services and IoT devices are making it easier to quickly launch massively larger attacks than before. September 2016 marked one of the largest attacks on record, over 600 Gbps of DNS and GRE traffic generated, at least in part, by IoT devices.
The response to this threat must be one from the entire Internet community. Every open DNS resolver, every IoT device, every exposed UDP service like memcache has to be discovered and its access restricted. Like vaccinations and herd immunity, the more protected each of us are, the more protected we all are.
Protection from these attacks and the foundation of any effective security posture is visibility and knowledge of one's enterprise architecture. The massive, hybrid, distributed nature of modern enterprises makes it even harder to know what is contained within them, let alone what services are vulnerable or exposed at any given moment. Many organizations have vulnerable services open to the internet, and have not implemented best practices for detecting and rejecting spoofed traffic.
ExtraHop's agentless and real-time asset and service discovery allows customers to achieve the level of awareness needed to address these threats. Because ExtraHop detects all assets and devices as soon as they communicate across the network, and understands which protocols they're using, it can provide early warning and continuous monitoring of systems potentially at risk from UDP reflection attacks or other exploitation. Monitoring network traffic in flight allows a conclusive audit of what services are running and what their connectivity is. If a new virtual server is created with memcache enabled and exposed to the Internet, it will be revealed from the first packet sent to/from this service. The same level of detection applies to DNS, FTP, Telnet, or any datacenter service.
Real-time, continuous monitoring permits an immediate response during the early stages of Memcrashed or other reflective DDoS attacks to stop them in their tracks, protecting both the intended target of the attack and all Internet community members. ExtraHop detects these misconfigured services is out of the box, with even deeper detection possible with additional configuration.
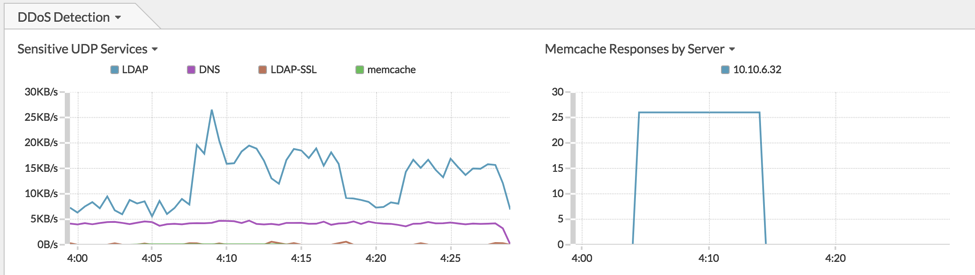
Figure 1: Dashboard monitoring various UDP services usage by throughput and memcache response volumes by server.
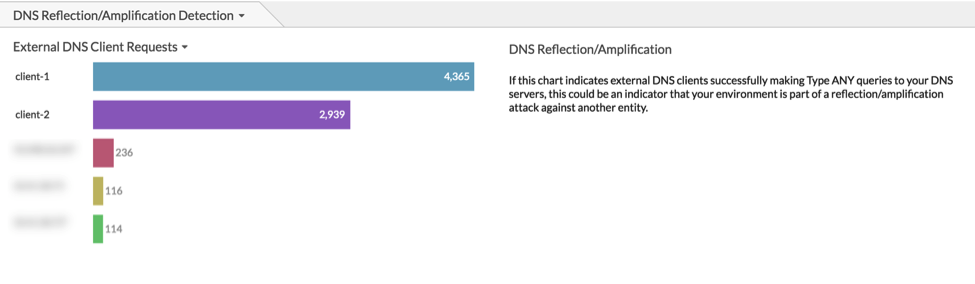
Figure 2: Dashboard monitoring DNS ANY Queries sourcing from external clients
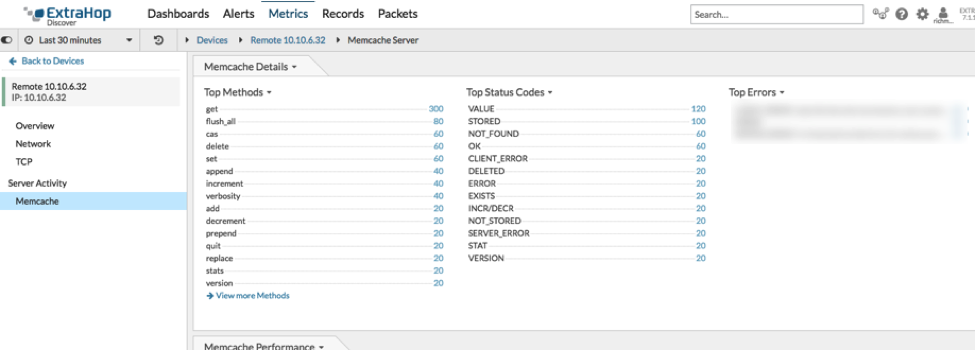
Figure 3: Native server object indicating memcache server activity down to the method, code, and error.
UDP Reflection/Amplification Background (memcached and otherwise)
UDP reflection attacks take advantage of the "connectionless" aspect of UDP traffic, since both the sender and recipient do not have to "commit" to the connection bidirectionally. This allows bad actors to weaponize hundreds or thousands of internet-facing services by making requests to them with a spoofed source address. This spoofed address is the intended target of the attack, which the weaponized services happily flood with responses to requests the target never made.
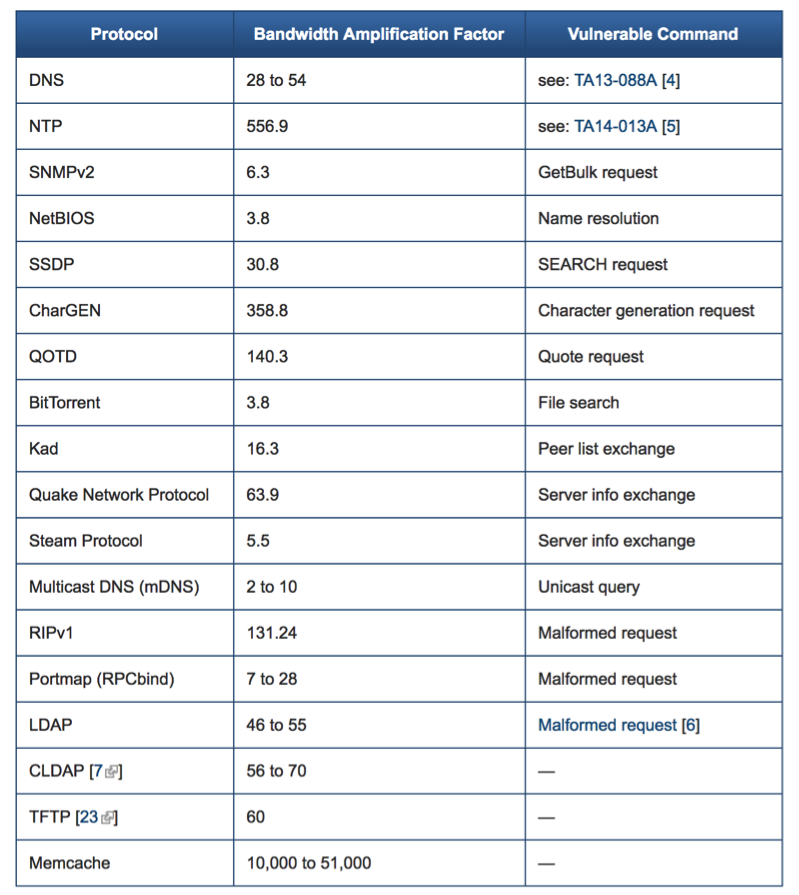
Attackers also make the most out of the weaponized services by crafting their spoofed requests to maximize the Bandwidth Amplification Factor (BAF), in other words, to get the maximum amount of targeted response traffic out of the smallest amount of traffic the bad actors need to initiate. Taken in perspective, DNS has a 28-54 BAF. Memcache has a 10,000-51,000 BAF, almost 3 orders of magnitude greater. The 600 Gbps attack of 2016 almost brought the Internet to a crawl. We have just witnessed a 1.35 Tbps memcache based amplification attack. A 600 Tbps attack would be catastrophic to the fabric of the Internet.
Figure 4: Bandwidth Amplification Factors for common UDP services
I will conclude this blog entry with another loud call to action by every member of the Internet community to take proactive action to both audit their public facing services, and to develop IoT devices which have built-in resilience to being weaponized against targets. The only way we continue to benefit from the Internet is if we are conscientious caretakers of this shared resource.