You're in the Middle Ages and have just been appointed master-at-arms for a local baron, with directions to make the castle secure. There are so many ways defenses could be improved and it's unclear where you should start. Should you add cauldrons of boiling tar? Invest in more training for your archers? Replace the rusting portcullis?
Security teams have to make similar decisions when deciding which areas to invest in when it comes to protecting their environment. The Critical Security Controls from the Center for Internet Security (CIS) help security teams prioritize actions.
- Controls 1-6 are considered basic, meaning that they are essential first steps to improving your organization's security posture.
- Controls 7-16 are foundational actions, focusing in on technical best practices for specific domains such as malware defense and email and browser protections.
- Controls 17-20 are organizational actions focused on people and process, including security awareness, incident response, and pen testing.
Using the CIS Top 20 Security Controls as a guide, security teams can identify gaps in their defenses as well as areas of investment where they will get the most returns. Network detection and response solutions like ExtraHop Reveal(x) make it significantly easier for security teams to follow the CIS Controls and get value from the framework.
Reveal(x) offers broad support for CIS Controls version 7, including several of the more important—and ambitious—coverage areas for asset cataloguing, administration privilege usage, and limitation of network ports, protocols, and services. We've mapped Reveal(x) capabilities to the CIS Top 20 Security Controls in this white paper.
Get the white paper: How Network Traffic Analysis Makes the CIS Controls Easier.
Much of the CIS Controls are about monitoring and auditing activity, which Reveal(x) supports extremely well because it is continuously analyzing and recording metadata about all transactions on the network.
As an example, take Control 1: Inventory and Control of Hardware Assets, which builds on the truism "You can't secure what you can't see." That saying is even more relevant in today's sprawling, dynamic environments where traditional methods of asset management cannot keep pace. Many organizations have active, scheduled scanners prescribed in Control 1.1, but lack the passive scanning required for Control 1.2 that is core to the Reveal(x) design. Passive monitoring has multiple benefits—it has no performance impact on users or networks, it cannot be detected by attackers, and it is always up-to-date since it is always monitoring network traffic.
Reveal(x) automatically discovers and classifies devices communicating on the network according to their activity. So if a device is functioning as a DNS server, Reveal(x) will categorize it as such automatically. The solution catalogues all activity for every device and extracts contextual details such as the manufacturer, operating system, and user credentials used on the system. This real-time information feeds Reveal(x) analysis of behavior and suspicious activity, and can also be streamed to a CMDB or SIEM for tracking new or rogue devices, or to firewall or network access control devices to enforce access policies.
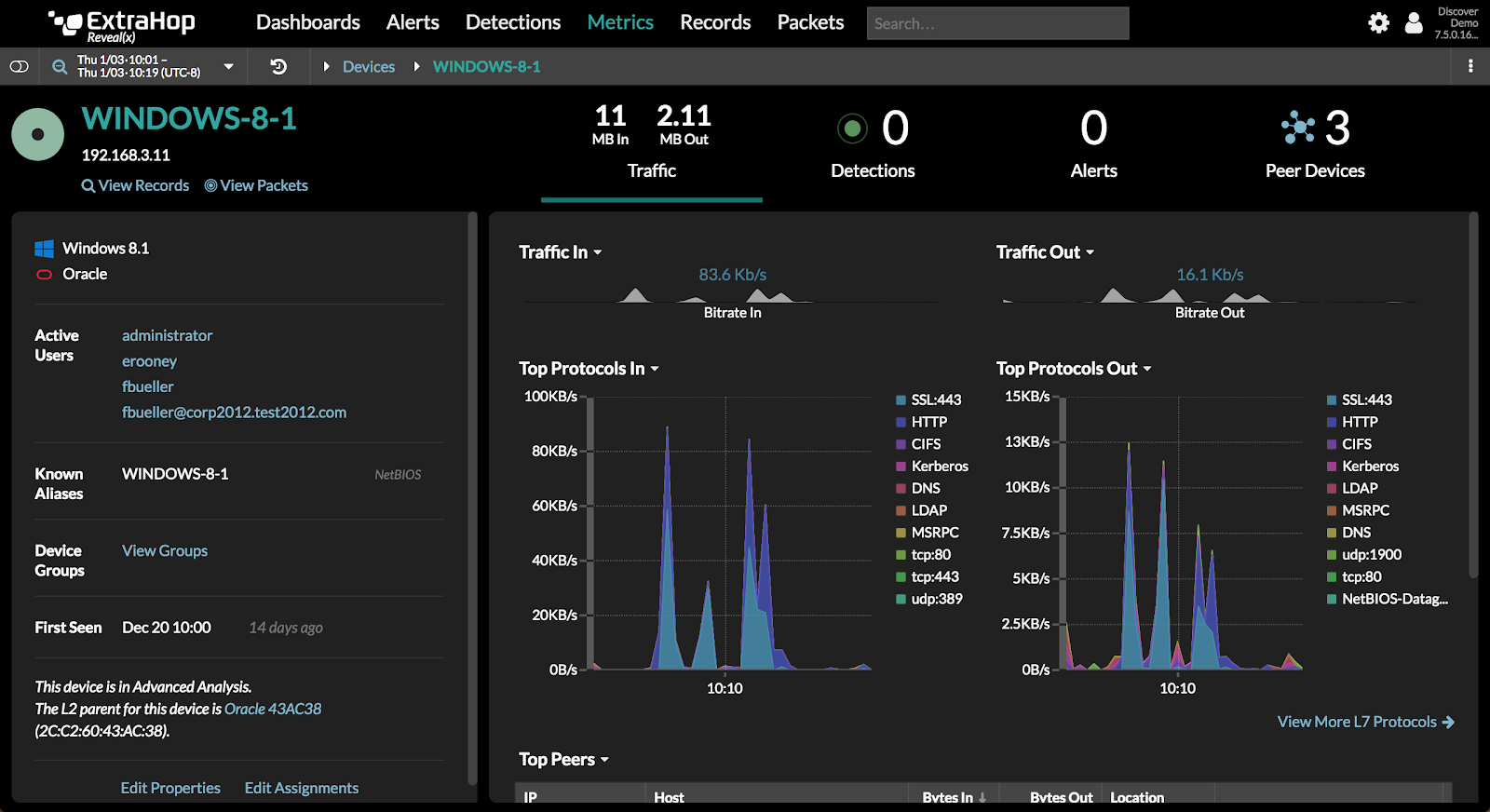
Reveal(x) automatically discovers and classifies devices on the network by analyzing their communications. You can use this information to find rogue or unmanaged devices, track admin credential usage, or monitor the use of sensitive ports, protocols, and services.
Again, this is just one example of how Reveal(x) makes "easy things easy, and makes hard things possible," to quote Perl inventor Larry Wall. The secret is being able to truly understand what is being communicated on the network. If you can do that, then you can easily answer questions pertinent to multiple CIS Controls such as:
- Are there rogue or unmanaged devices on the network?
- Who is using administrator credentials, and what are they doing with those credentials?
- Has any device suspiciously elevated their access privileges recently?
- Are any devices using unencrypted FTP to transfer sensitive files?
- Are any devices using the SMBv1 protocol, which is vulnerable to malware exploits?
- Is traffic encrypted in particular subnets when it should be?
Read more about how Reveal(x) supports the CIS Top 20 Controls in the white paper.
