On June 4, the U.S. National Security Agency issued an advisory urging organizations to guard against a recently announced vulnerability in several Windows operating systems dubbed "BlueKeep" (CVE-2019-0708). They expect exploit code to be available soon that will enable hackers to remotely install malicious software on systems via some older but still often used implementations of the Remote Desktop Protocol (RDP). The NSA also notes that the flaw potentially "wormable" so that it can be exploited to spread malware throughout the enterprise without user interaction, similar to how NotPetya spread in 2016.
While Microsoft has issued patches for BlueKeep, many system administrators do not have visibility into all the RDP communications in their environment, and specifically those systems running vulnerable versions of Windows. New, overlooked, or rogue systems may not have the latest patches and can be exploited. ExtraHop frequently finds unexpected use of RDP and other vulnerable services and protocols in customer environments. ExtraHop urges system administrators to build a complete inventory of their systems and look for vulnerable implementations of the Remote Desktop Service specifically as well as older legacy protocols such as SMBv1.0, which was used by the 2017 NotPetya worm.
What to do next?
The advice on how to mitigate the impact of BlueKeep—aside from patching, which should be the priority—is as follows:
-
Scan your network for open Remote Desktop Protocol (RDP)
-
Disable Remote Desktop Services if they are not required
-
Enable Network Level Authentication (NLA) on systems running supported editions of Windows 7, Windows Server 2008, and Windows Server 2008 R2
-
Block TCP port 3389 at the enterprise perimeter firewall
The bigger point is made by the NSA in their advisory: "NSA urges everyone to invest the time and resources to know your network ... This is critical not just for NSA's protection of National Security Systems but for all networks."
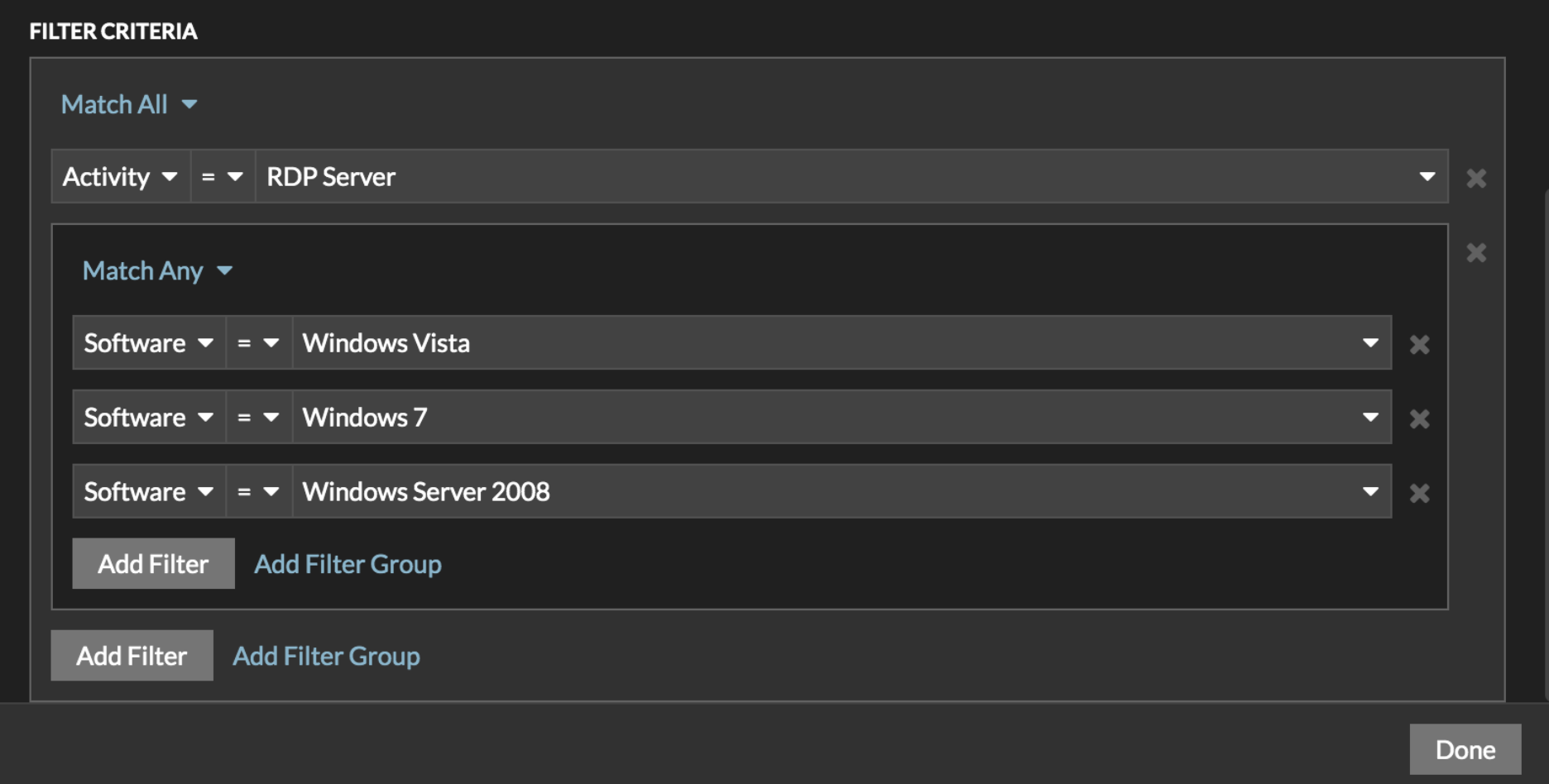
For ExtraHop customers, knowing where legacy RDP servers are is pretty easy. You can view RDP server metrics, but to see just the RDP servers with vulnerable versions of Windows, you will want to create a dynamic group using the criteria shown in the image below. And, of course, Reveal(x) will flag BlueKeep activity specifically as a detection.
Here's a quick video demonstrating how to use Reveal(x) to find devices using affected operating systems, and how to tell whether there is unauthorized RDP and SMB/CIFS activity on your network:
