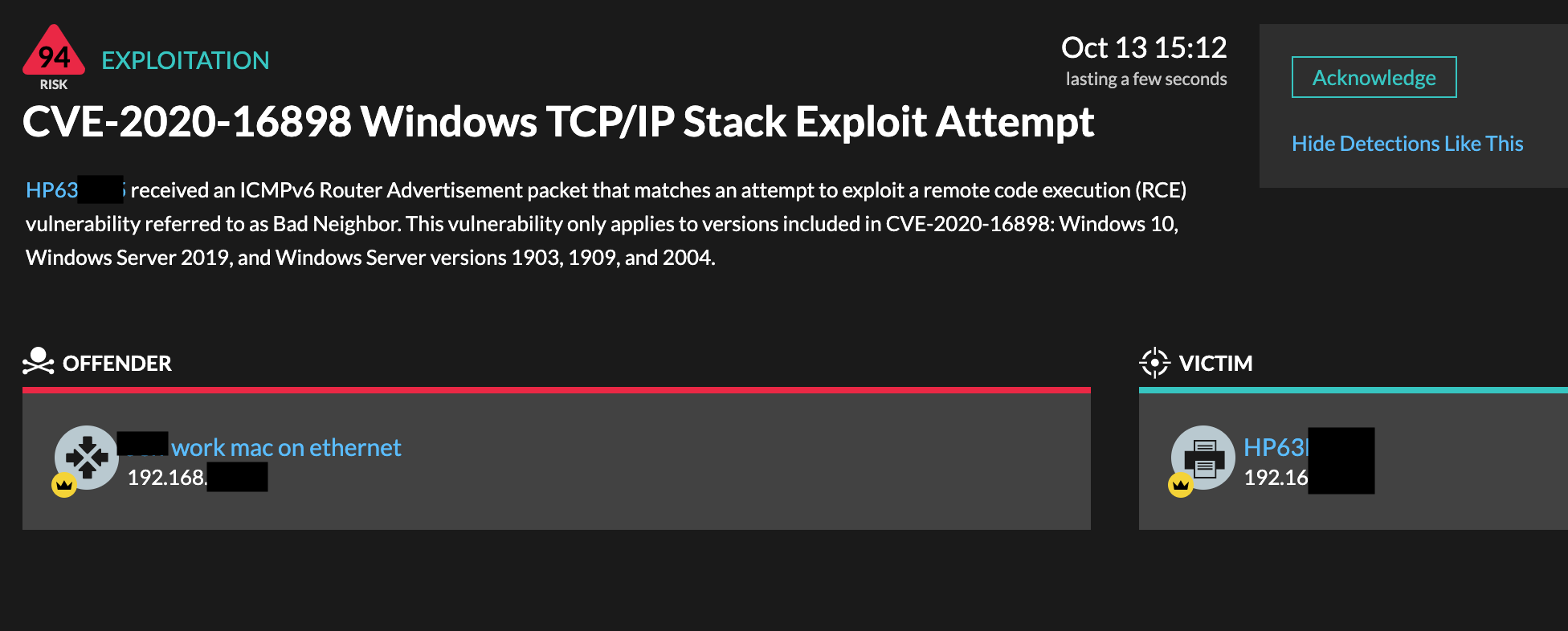
The Windows 10 vulnerabilities unveiled by Microsoft on October 13th include a remote DoS (CVE-2020-16899) and a remote code execution flaw (CVE-2020-16898) dubbed 'Bad Neighbor'. Both of these vulnerabilities are in code that processes ICMPv6 Router Advertisement messages, a fundamental part of IPv6.
This is a widespread problem, as evidenced by the fact that through 2020, 80% of all PCs will have migrated to Windows 10, according to Gartner*. Given the fact that Windows 10 device patching is markedly quick, we do not expect to see a NotPetya-scale impact from this bug. But, organizations must immediately patch their systems to avoid impact. Users essentially cannot disable the IPv6 functionality, but can mitigate it with work-arounds if applying the patch is difficult.
This vulnerability would allow a hacker to exploit a remote code execution (RCE) vulnerability to run malware or launch a denial of service (DoS) attack. Because this vulnerability is in the IP stack in the kernel, other security solutions (like EDR, SIEM or IDPS) are unlikely to detect these particular exploits. EDR solutions will only see the attack once the payload is executed and logs in a SIEM are unlikely to detect this vulnerability because messages (ICMP) are rarely logged.
ExtraHop Reveal(x) has a unique ability to see network attacks. By monitoring network data, Reveal(x) will catch threats that other tools miss and enable your team to investigate and respond to threats 84% faster.
Recommendations For Mitigating Bad Neighbor
Any organization using Windows 10 is vulnerable and should deploy the patch immediately to avoid compromise of their Windows 10 systems.
To ensure that our customers remain safe before they have time to deploy the patch, ExtraHop has created and deployed detections for this vulnerability for all customers running 8.0 and higher.