Let's call a spade a spade here, folks. If you're in IT Ops or SecOps, chances are your job just got a lot harder. Overnight, you went from ensuring the performance, availability, and security of applications and systems for office workers, to trying to ensure the same for a vast number of distributed employees.
We're not going to try to placate you with false promises of a silver bullet, because there is no such thing. But we also work with a lot of organizations just like yours that are facing immense challenges right now, and we think it's worth sharing what some of those common challenges are and how our customers are tackling them.
In this blog post, we will look at the performance and security implications of this rapid shift to the IT infrastructure, the human impacts of these implications, and how cross-team collaboration and data sharing can ease the burden.
Performance Challenges and How to Meet Them
Dramatically increasing the number of people working from home is putting an incredible strain on remote access infrastructure as well as the Help Desk and IT teams handling the escalations.
Get ready for the "ghost in the machine" to manifest. Any tickets with "citrix," "vmware," or "cisco" will be routed to the remote access team who will be responsible for troubleshooting the issue. However, these systems are incredibly complex with many dependencies downstream—such as domain controllers and profile servers—and the remote access team may lack the visibility or expertise to diagnose the true problem.
In these cases, visibility across the entire delivery chain is critical to being able to triage and troubleshoot the issue. Keep in mind that many VPN issues will manifest at the transport protocol layer often in the form of retransmission timeouts and zero window measurements, while downstream issues with applications and resources will be apparent with Layer 7 analysis to identify errors and the associated conversations. Be sure to check out Josh Snow's video (also embedded at the bottom of this post) showing how to set up VPN monitoring dashboards and how to monitor remote connections with TCP metrics using ExtraHop.
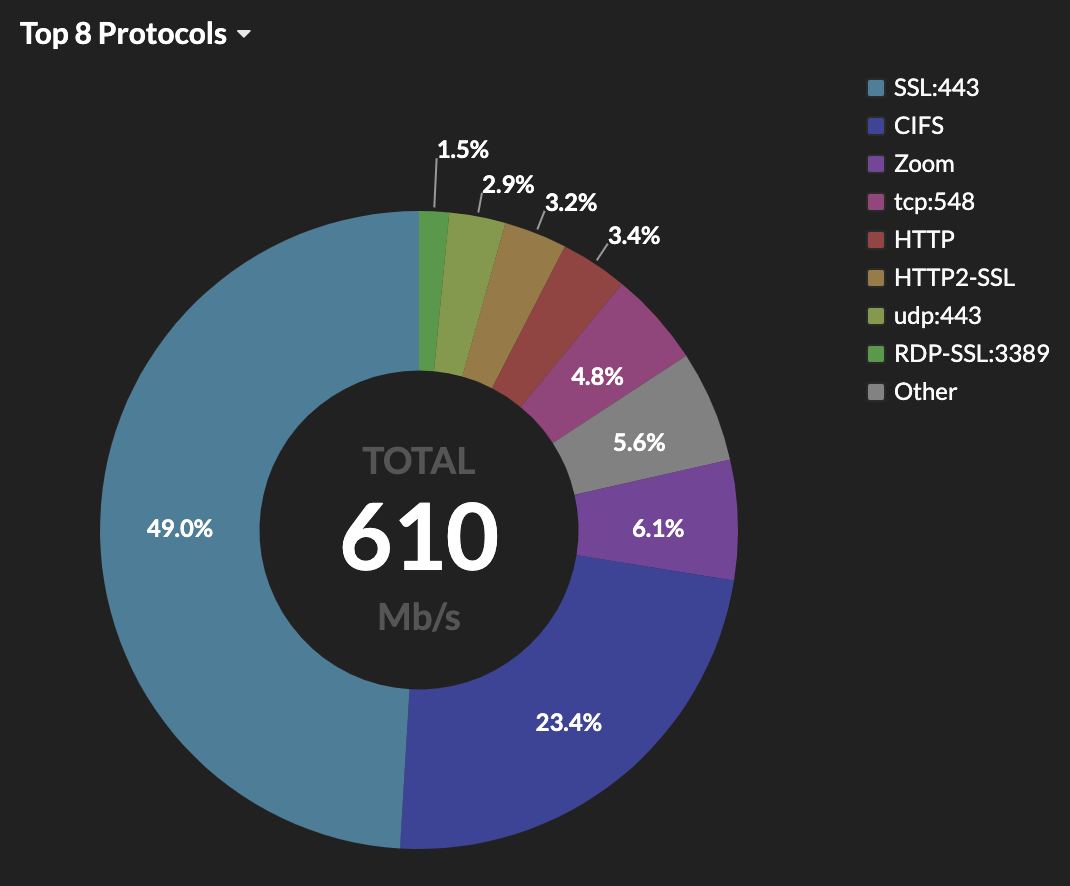
Part of a dashboard set up to monitor VPN activity by an ExtraHop customer.
Measure utilization. You may lack adequate network bandwidth to handle the increased demand of remote users, so monitoring for bottlenecks at the gateway is critical to determine if a bigger pipe is needed. Additionally, while it's important to ensure remote users have access to applications and resources, you should not forget about measuring your organization's success (or failure) to provide that access.
On the one hand, demonstrating how inadequate resources led to performance degradations, makes it easier to justify funding requests. On the other hand, if everything is going well, then measuring remote access utilization can help management understand the value that your team is providing to the business. Management may also be reassured by seeing that people are actually working while practicing self-distancing.
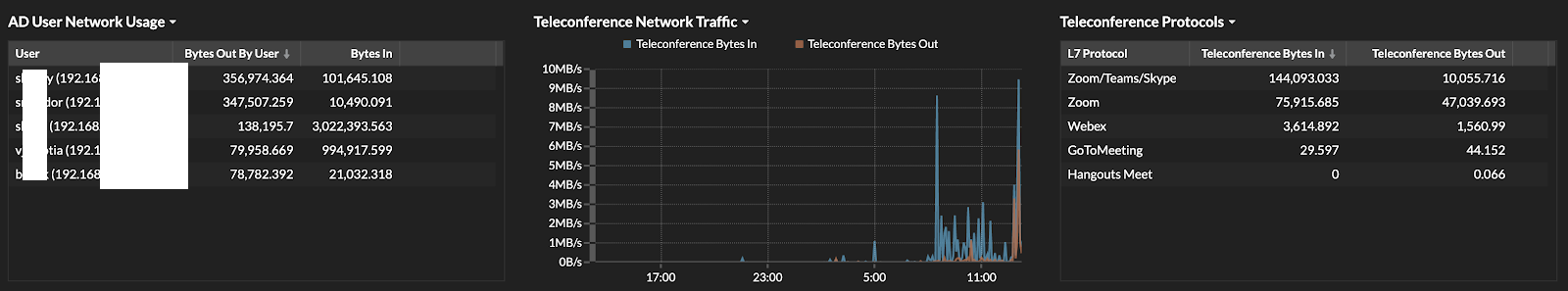
Part of a dashboard set up to monitor VPN activity by an ExtraHop customer.
Security Challenges and How to Meet Them
While making sure newly remote workforces can access the applications and systems they need in order to perform their job functions, availability is not the only challenge. The security implications of this sudden shift, if not immediately apparent, will quickly become so.
Many remote workers have not been issued company laptops, a point underscored by the numbers of companies allowing users to take home tower PCs—PCs with profiles and protections designed to be behind corporate firewalls and monitoring services. These devices may have firewalls disabled, or may not be able to speak to their AV update servers among other potential issues.
While some may be hauling home bulky hardware, others are accessing the corporate network via unmanaged devices that lack adequate antivirus protections. And speaking of access, the number of people working from home may force IT teams to loosen restrictions about what applications and data are accessible through the VPN.
And unmanaged devices combined with relaxed standards leaves the door open for threat actors. There have already been a myriad of COVID-19 related phishing attacks targeting unsuspecting users. But there are a few simple steps security and IT organizations can take to protect the network while they defend a larger and more porous attack surface.
Determine where people are remoting in from. IT organizations should pay attention to the geographic origin of external IPs connecting to their VPN concentrator or access gateway. Knowing where your users should be connecting from is very important, and one user connecting from two geographic locations will represent an actionable finding.
Are people using approved remote access tools? Many organizations have policies against using remote access tools such as TeamViewer, LogMeIn, and GoToMyPC. Enforcing these policies can go a long way toward securing sensitive applications and data, and looking at network communications is the fastest way to identify this type of activity.
Monitor Active Directory accounts. Look for excessive lock-outs, failed logins, and use of disabled accounts—all of which can indicate attackers have compromised a user device and are trying to gain access to more resources. Tracking service accounts for unusual behavior is a good idea, as is setting up "canary" accounts that act as a honeypot or tripwire catching attackers looking for more access in your network.
This is particularly critical given the large number of unmanaged personal devices now accessing the network. These unmanaged devices heighten the risk of stolen credentials, among other security implications.
People Are Still Your Greatest Asset
Right now it's easy to get fixated on the challenges that radically upended user access requirements now pose. If you've read this far, you know that there are a lot of them. But in the thick of it, it's also important to remember that people are your greatest asset, and that goes for your IT and Security personnel as well as your end users.
And that's why, especially for IT and security teams, finding ways to work together, share information, and avoid finger pointing is critical. As noted in the "ghost in the machine" example, teams traditionally focused on one domain—whether end-user experience or security—may lack the visibility and expertise required to manage that under new conditions. Who knows? If we take this opportunity to reach out to our colleagues and get their input on how to solve the challenges we are facing together, then something good might come of this situation we find ourselves in.
Learn More
If you'd like to learn more scaling remote access, join our webinar on April 2 featuring a panel of experts, including ExtraHop Principal Security Engineer John Smith who ran Citrix infrastructure at the Centers for Disease Control and Prevention (CDC) and our own ExtraHop IT Director Bri Hatch, who has a few good ideas of his own as he has kept up with the rapidly growing number of ExtraHoppers around the world.
Meanwhile, watch the short videos below to learn how you can use network detection and response to ease the stress of securing and monitoring remote access:
WFH With ExtraHop Series
Additional Resources
We found these reports from 451 Research to be helpful, and we hope you do as well:
