Remote administration tools make life easier for IT administrators. From one location, an administrator can remotely deploy updates, run programs, or run commands on several network devices. But these tools also make life easier for attackers who want to run commands on, and compromise, other devices within a network.
Consider this scenario: an attacker wants to steal credit card numbers from a company that manages financial transactions. Through a phishing email campaign, a company employee inadvertently installs malware on their Windows workstation, giving the attacker access to that workstation. Now inside the network, the attacker wants to find and access a server with credit card information.
So how does the attacker compromise the credit card server, laterally moving from the workstation to the server, while remaining undetected? One option is to launch a legitimate remote administration tool with a system service, such as PsExec.
What is PsExec?
PsExec is a Windows Sysinternals utility that enables IT administrators to run commands and executable binary files on remote servers. PsExec requires the IT administrator to launch a system service. Launching a service includes these components:
- ADMIN$ share, which is a hidden share located on Windows devices. Only users with administrative privileges can access ADMIN$.
- Service Control Manager (SCM), which is located on Windows clients and servers. The SCM manages programs and services that run on Windows devices.
- Remote procedure call (RPC), which is a network protocol that enables communication between a client and server. For example, the SCM has an interface (svcctl) with operations (such as CreateServiceW). Operations are similar to procedure commands. If an IT administrator wants to perform a procedure (such as creating a service with SCM on a remote server) the administrator's client sends an RPC request to call the specific interface and operation (svcctl:CreateServiceW) on the server. The action of calling the interface and operation runs the procedure.
- Named pipe: A process that enables peer-to-peer communication over the Server Message Block (SMB) file sharing protocol. Typically, read and write file operations are sent through named pipes.
Users with administrative privileges must follow a basic workflow to launch PsExec. First, the administrator uploads an executable file, PSEXESVC.exe, to the ADMIN$ share on a remote server over SMB (1). Next, the administrator sends RPC requests to connect to the SCM and launch a service that will run PSEXESVC.exe (2). The PsExec service is launched and an SMB named pipe is established between the administrator and the remote server (3). The administrator can now send commands with the PsExec command-line interface (for example, psexec \remote cmd) and receive output through the named pipe.
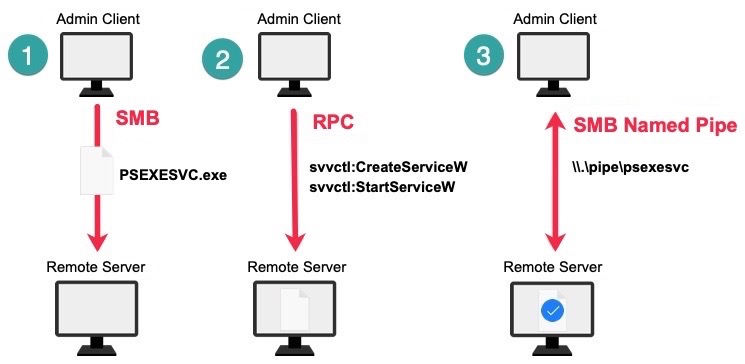
The general workflow for launching a PsExec service.
If an attacker wants to remotely run commands on a target with PsExec, such as the credit card server, the attacker must have the ability to upload executable files to the ADMIN$ share on the target. The attacker must also have the authorization to interact with the SCM interface on the target. These activities require local administrator privileges, which are typically associated with highly protected accounts.
However, it's not impossible to acquire these privileges. Attackers can steal credentials for an account with these privileges, or escalate the privileges of a compromised account.
Because PsExec has powerful capabilities, many threat groups (such as FIN6 and APT39) have included PsExec in their attack campaigns. Additionally, the pen testing tool, Metasploit, has a PsExec module for rapidly querying and interacting with remote servers. Based on this history, some organizations prohibit PsExec.
How to Detect PsExec Misuse
Detection methods can include checking system logs for the PsExec service name and for named pipes. System logs can show which credentials launched the service. But this approach requires the network defender to search hundreds of logged events for a single service or named pipe. The attacker can also create a modified version of the PsExec utility, changing the names of the service and named pipe to evade detection.
ExtraHop automatically detects unusual RPC traffic crossing the network that is associated with services such as PsExec.
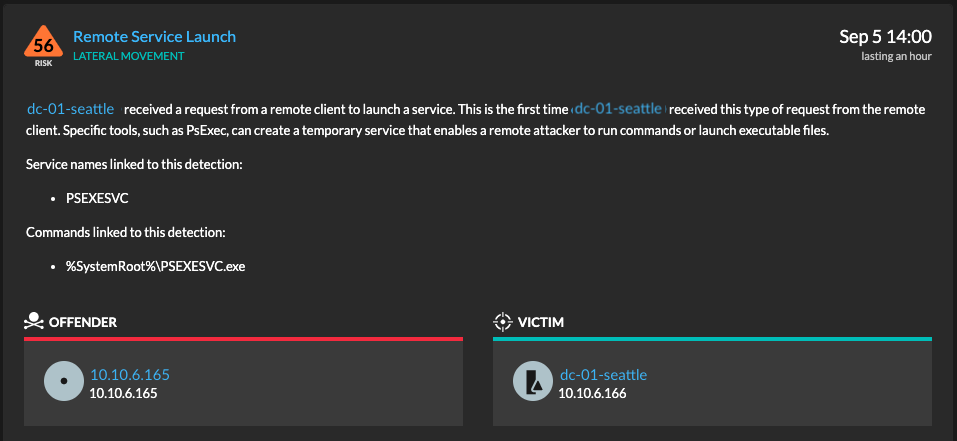
The detection card displays which device (offender) sent RPC requests to start a service on a remote server (victim), and which executable file (PSEXESVC.exe) is linked to the service.
Administrators usually manage remote workstations and servers from a few administrative devices. This means that a new device, associated with a non-admin user, should not be launching services to make changes on other network devices. Quickly identifying unusual services, and the executable files associated with them, can help network defenders confirm if an attacker is attempting lateral movement from a compromised device.
How to Prevent Lateral Movement by PsExec
Top-down, comprehensive strategies can help reduce the risk of lateral movement by PsExec. One strategy is enforcing the principle of least privilege by reducing the number of accounts with administrator privileges. Another strategy is segmenting networks and creating policies that limit the interactions of a compromised device in one sub-network with other network devices. But network segmentation is difficult to set up and maintain.
Bottom-up strategies can prevent these types of utilities from causing damage. You can create a policy that prevents users from downloading software tools such as PsExec and AppLocker. You can also configure the Windows Registry to require User Account Control (UAC) approvals for any PsExec operations requiring administrator privileges.
Stay vigilant for unusual RPC requests to prevent attackers from deploying and running malware on network devices. To learn more, read this blog about detecting and stopping lateral movement.
