To enable all these features, please upgrade to the latest version of ExtraHop Reveal(x), 8.1.3.
UPDATED—August 7, 2020
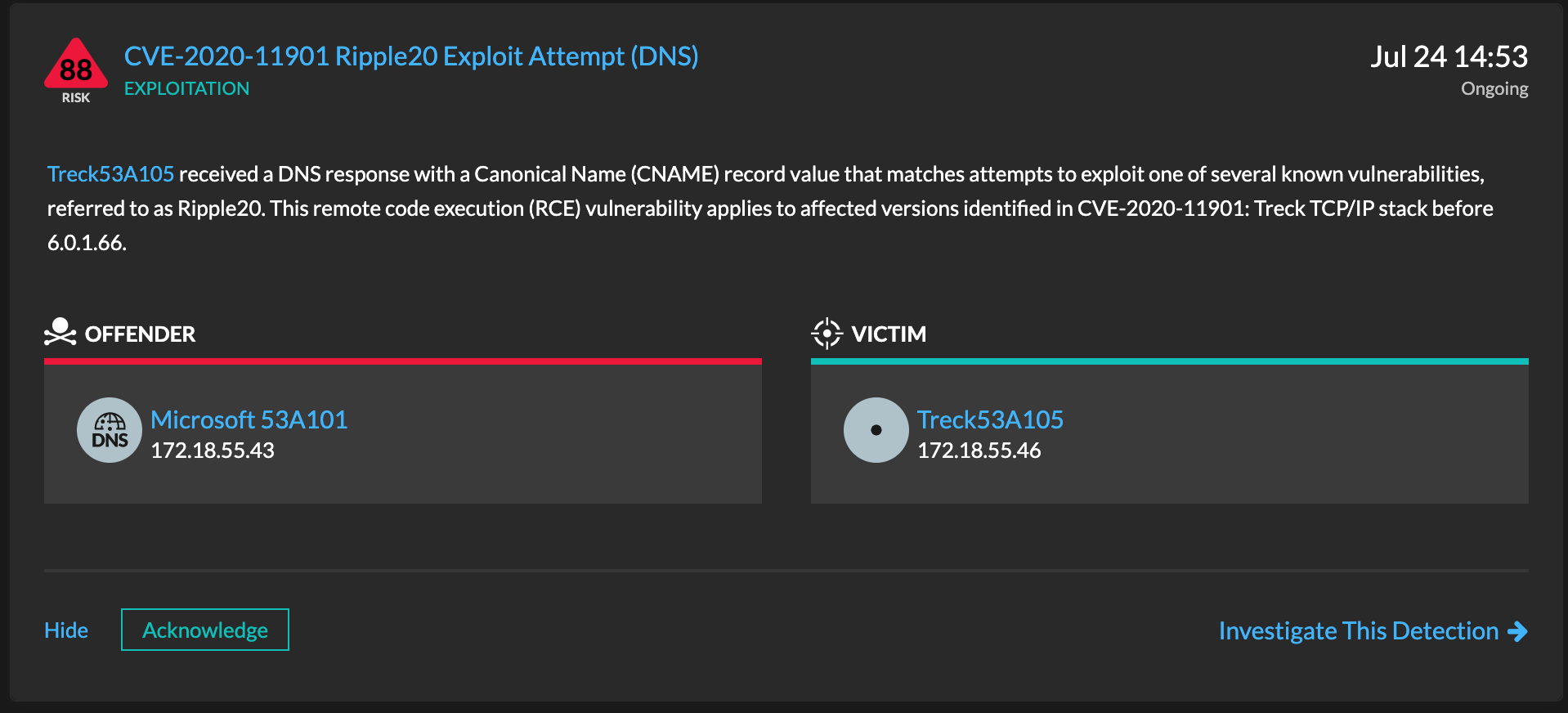
ExtraHop has published detections for CVE-2020-11901, for which JSOF presented details at Black Hat on August 5. In the disclosure, a set of four bugs are described that can lead to remote code execution on an affected device. In its revision of Treck's DNS parsing logic, ExtraHop Threat Research independently identified a separate heap overflow that Treck verified only affects earlier versions of the software and falls under the umbrella of CVE-2020-11901.
Exploitation of CVE-2020-11901 is identified via the following detection:
Critical Vulnerabilities, Hundreds of Millions of Devices Exposed
You've probably heard about Ripple20, but why is it so significant and how will you know if your environment is affected? Ripple20 is a series of recent vulnerabilities discovered by JSOF in devices that contain the Treck networking stack.
The Treck stack has been in use in embedded devices for more than twenty years. Hundreds of millions of devices in the industrial controls, networking, transportation, retail, oil and gas, medical, and other fields that use the Treck software are now known to be vulnerable to exploits. ExtraHop research indicates that 35 percent of environments are vulnerable. These exploits can enable attackers to steal data or even execute code.
Unfortunately, these devices can be hard to identify and even harder to patch. So what should you do if you have (or don't know if you have) Treck devices in your environment? The safest route might be to remove or replace some of these devices as often they are relatively inexpensive printers or other devices that may be aging out.
That's not an easy task to be sure, and it requires an accurate inventory of affected devices. Scanning for these devices can impact your network and its performance. And what about the attackers who are in your systems scanning for these devices as well? Can you detect them?
Our ExtraHop threat research team took a deep dive into Ripple20 and have outlined what you need to be looking for to detect this vulnerability. Let's step through how that works.
Identifying Devices Vulnerable to Ripple20
Finding vulnerable devices can be tricky. To demonstrate the process we'll use ExtraHop Reveal(x), our network detection and response solution, to identify vulnerable devices by analyzing their communications on the network. This is a passive method of discovery that does not require active scanning and will not impact the environment.
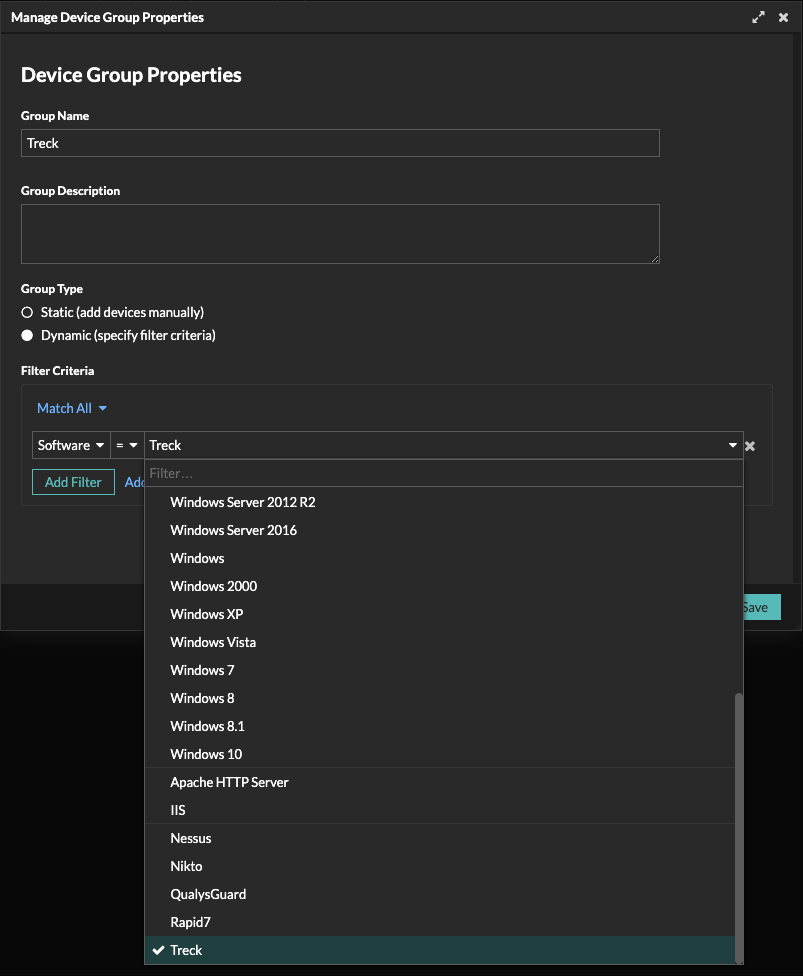
To create an inventory of devices using the vulnerable Treck software, simply create a device group as shown below. (A note for current customers: this is available in version 8.1.3)
First, go to the Assets page.
Then create a new Device Group.
Then specify a Dynamic Group that contains the Treck software.
Once you have that device group, you can use the device group to show you all the devices that use the Treck software stack to take action. See below for our recommendations.
Detecting Scans For Devices Vulnerable to Ripple20
In addition to detecting the vulnerable devices themselves, Reveal(x) can also detect when attackers (or vulnerability managers) scan for these devices or actively exploit the vulnerability. Attackers who have gained a foothold in your network will likely be scanning for devices with Ripple20 vulnerabilities. There are multiple ways for attackers and vulnerability managers to scan for vulnerable devices. ExtraHop has deployed detections that will detect the most effective method of scanning for devices that are using Treck software.
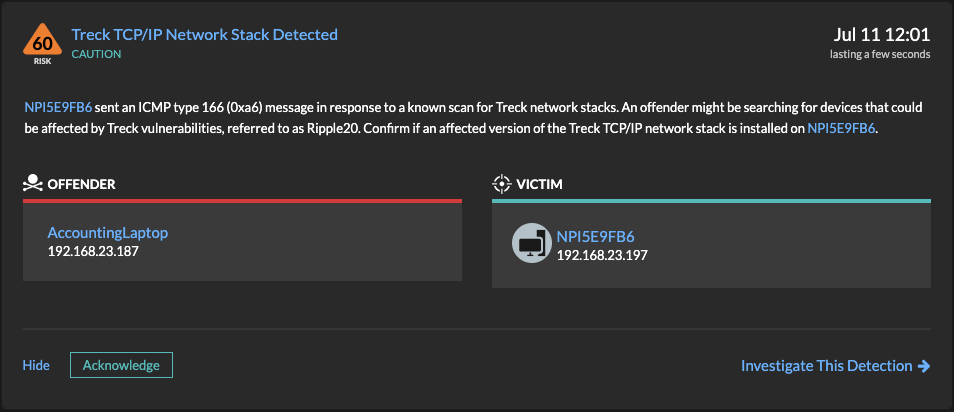
The most reliable method is to send an odd ICMP type 165 (0xa5) message.
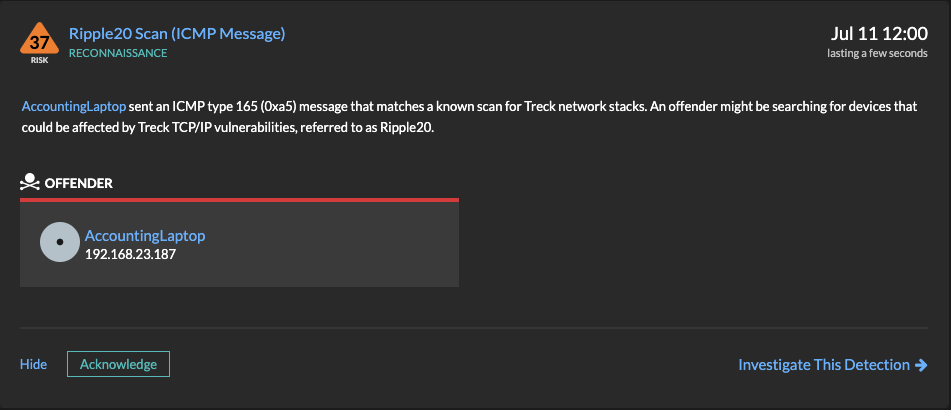
If the device sends an ICMP type 166 (0xa6) message in response, then we can confirm that the device is running the Treck TCP/IP stack and may be vulnerable.
Detecting Ripple20 exploits
Many of the embedded devices using the Treck TCP/IP stack are not going to be able to run endpoint agents and will have very limited logging capabilities. That means security teams will need to look to network data in order to detect attempted exploits.
Reveal(x) detects exploits in progress for both the information leak, CVE-2020-11898, and the worst of the remote code exploits, CVE-2020-11896. These vulnerabilities exist due to the fact that the Treck TCP/IP stack improperly handles IPv4 fragments over an IP-in-IP tunnel.
Both CVE-2020-11898 and CVE-2020-11896 stem from the same truncation, shown below.
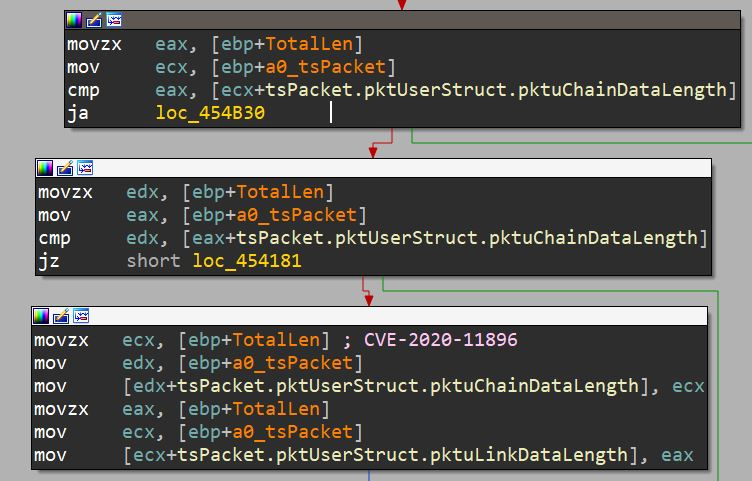
An encapsulated UDP packet leads to a flow wherein exploitation of CVE-2020-11896 can be achieved. The software concatenates the contents of each fragment into an allocated buffer of the truncated size. The size discrepancy can be abused for a heap overflow.
Furthermore, rather than a truncation, a packet can be crafted that says it is longer than it actually is. If the encapsulated packet is an invalid protocol or otherwise one that is not supported, an ICMP error message responds with heap contents that were adjacent to the sent packet—the information leak described by CVE-2020-11898.
The combination of the information leak in exploiting CVE-2020-11898 and the remote code execution provided by exploitation of CVE-2020-11896 allows an attacker to reliably execute arbitrary code in a device running the Treck TCP/IP stack.
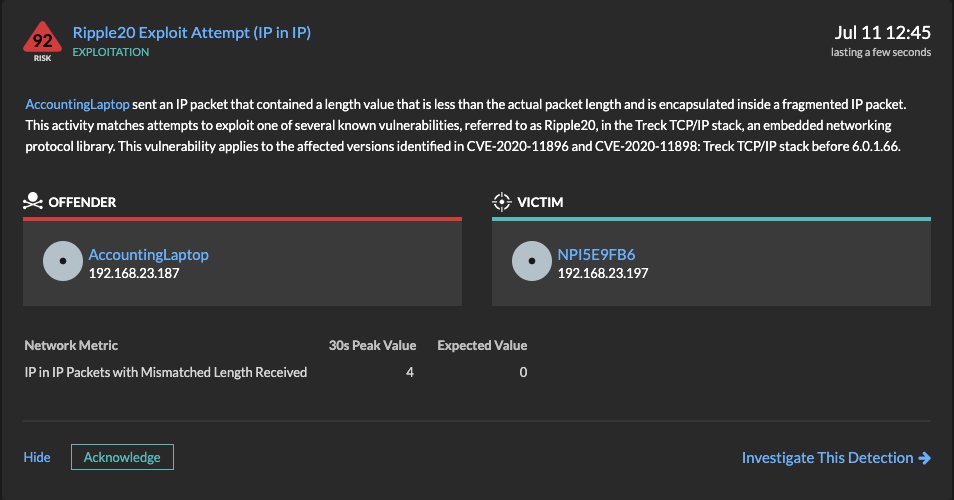
Reveal(x) will detect an attacker attempting to remotely execute code by sending an IP packet that contains a length value that is less than the actual packet length and encapsulated inside a fragmented IP packet. Packets that match these criteria indicate that the attacker is intentionally sending inconsistent packets with a large amount of arbitrary data to the victim.
Recommended Actions
The first step is to identify any devices that may expose you to risk. It is advisable to patch or otherwise replace affected devices where patches are unavailable. In circumstances where neither of these options can be realized, it is recommended that you:
- Verify devices are not publicly accessible
- Move devices to a network segment isolated from local subnets
- Drop all IP-in-IP traffic destined for affected devices
- Drop all IPv6 traffic destined for affected devices
Additionally, special attention should be paid to the Treck device group in Reveal(x) for anomalous traffic.
Looking Forward
The Ripple20 vulnerabilities highlight the difficulty of securing devices and applications within complex software supply chains. In the case of the Treck networking stack, it has been in use for more than 20 years and made its way into hundreds of millions of devices across multiple industries. Most organizations won't be able to rely on their device vendors for a solution or even know if they have the vulnerable devices in their environment.
ExtraHop Reveal(x) passively analyzes the communications of devices on the network to identify their role, criticality, and device details such as manufacturer and software. The threat research team at ExtraHop is constantly building new detections and delivering them dynamically to all Reveal(x) customers, helping them to keep up with new threats such as Ripple20.
Watch this video for more on using Reveal(x) to find vulnerable devices and detect attacks.