Most organizations have several security tools to defend the perimeter of the network, but the reality is that these vital perimeter defenses are frequently breached. Once attackers successfully bypass perimeter defenses, they can be difficult to detect, especially when the adversary has stolen credentials and is using legitimate services to move laterally and achieve their objectives.
Network detection and response (NDR) provides a covert defense against these advanced threats. NDR cannot be evaded or tampered with, making it a crucial part of any security practice that hopes to catch stealthy threats, supply chain attacks, and advanced persistent threats that use legitimate credentials and systems to achieve malicious goals.
The network is an ideal point for detecting post-compromise attack activities for several reasons:
- The network offers covertly observed ground truth. While log data and endpoint data offer value for threat detection, they can be turned off, evaded, or modified. Passively observed network traffic is not subject to this tampering. Attackers have no way to be sure whether their network activity is being observed.
- Attacker behaviors and techniques on the network are not subject to the same high variability and polymorphism that plague the endpoint. There are millions of ways for attackers to get remote code execution capability on a host and steal data, but there are only a handful of ways to exfiltrate that data across the network. Watching for those network behaviors is much more likely to catch the attacker. Network signals can be used to detect many attacker tactics, techniques, and procedures across every stage of the MITRE ATT&CK Framework.
- The network offers greater breadth and depth of visibility than other options. Any device that communicates across the network can be discovered and monitored immediately when it first appears. Details such as users, software, operating systems, and more can be discerned from the device's network communications.
Reveal(x) provides both enhanced perimeter detections—which is more accurate than traditional intrusion detection—as well as a vital additional layer of defense in the case of an intrusion. This includes detecting subtle post-compromise activity such as misuse of Windows remote procedure calls and abnormal behavior from low-privileged devices or users.
This behavior-based detection approach is able to effectively detect attacks with a much lower false-positive rate than legacy, signature-based intrusion detection systems, which are known for being too noisy to provide much value, but which are still hanging on in many enterprise environments. Reveal(x) detects anything an IDS can detect, and much more, with greater context and confidence. It provides coverage for many attacker tactics, techniques, and procedures across every category of the MITRE ATT&CK Framework, which is directly integrated into the product, as illustrated below.
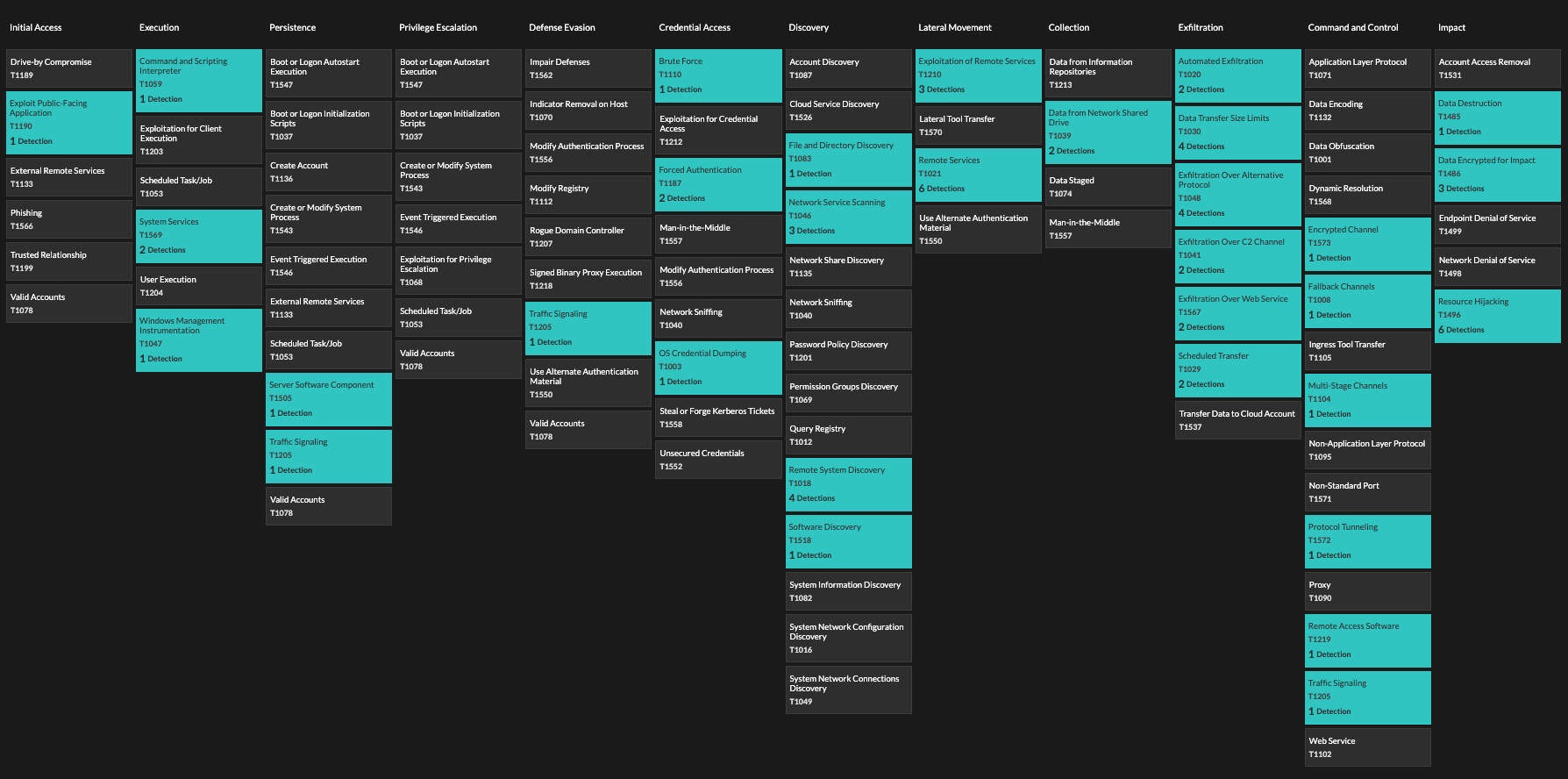
The MITRE ATT&CK Framework is integrated into the Reveal(x) NDR interface.
Spectrum of Detections
Reveal(x) employs numerous methods, including rule-based detection, machine-learning behavioral analysis, peer group analysis, and deep learning to detect the full spectrum of attack activity. Instead of relying on a single method, this combination of techniques provides more holistic coverage of attacker tactics, techniques, and procedures.
| Hygiene | Known Attacks | Unknown Attacks | |
|---|---|---|---|
| Definition | Activity violates security policy, deviates from secure practices, or otherwise indicates risk. | Includes IP addresses, domains, file names, payload strings, or known malicious protocol behavior. | Attacks that do not have a previously known identifier, but exhibit anomalous behavior suggesting an attack. |
| Built-in rule-based | Rule-based detections identify security hygiene issues by comparing observed behaviors on the network against security best practices. This uncovers risks such as the use of the vulnerable SMBv1 protocol or password information sent in cleartext, and more. | Similar to IDS, Reveal(x) uses complex rules logic to identify known attacks by specific attributes, eg. most network CVEs and techniques used in lateral movement. Developed by ExtraHop threat researchers, these rule-based detections are delivered and updated through the cloud. | Not applicable. |
| Custom rule-based | Organizations can also create custom rule-based detections that identify policy violations, such as cleartext data movement between network segments housing PII or health data, that may be unique per environment. | Customers can build detectors to detect threats and mitigate risks unique to their own environment or business, assuring total coverage. | Custom rule-based detections can be used as "tripwires" protecting critical assets such as important file servers and databases. |
| Machine learning | Not applicable. | Reveal(x) uses machine learning to model behaviors of entities on the network and contextually identify behaviors that resemble known attack techniques. | Reveal(x) employs machine learning techniques to detect malicious, anomalous behavior—including deviations from peer group activity, privilege escalation, and more. |
For more information about how Reveal(x) cloud-scale machine learning works, read our blog posts: Tricks of the Trade: How Reveal(x) Uses Machine Learning and ExtraHop Cloud Scale ML: A Deep Dive
Rule-Based Detections and Decryption
For rule-based detections, Reveal(x) does not use legacy techniques such as MD5 hash matching. Rather, our rules use sophisticated logic developed by our threat research team, fueled by the deep visibility Reveal(x) provides into the network. Using layers of signals derived from full-stream reassembly of network conversations and L2-L7 transaction details, Reveal(x) provides higher fidelity detections with much lower false positive rates than legacy IDS solutions.
Furthermore, Reveal(x) decrypts traffic at line rate, out of band, for analysis. This includes TLS 1.3 traffic with perfect forward secrecy. This decryption is done securely and out-of-band so that it has no chance of degrading the quality of encryption or impacting the performance of the network. This capability unlocks transaction-level details and insights that provide a much greater degree of confidence, as well as detailed forensic evidence to help analysts rapidly investigate and respond to incidents. These details are opaque to solutions that cannot decrypt TLS 1.3, which leaves them guessing about what happened and unable to provide deep forensic details for investigation.
Reveal(x) provides full records of transaction-level details, with the capacity for 90 days of lookback, as well as full, continuous packet capture (whether a detection fires or not), all accessible with a click so that analysts can rapidly and confidently respond to threats.
Here's what a Reveal(x) detection looks like, annotated with a brief explanation of each piece of contextual data that is instantly available for analysts.
For an even deeper look at Reveal(x) detection capabilities, please download our white paper: Network Detection & Response: How Reveal(x) Detects Threats
