Active Directory (AD) is an authentication service for managing computer and network accounts across an enterprise. Valuable account information—such as password hashes—is stored on servers called domain controllers (DCs). The DC is a treasure trove for attackers, but breaking into a DC to steal this information is difficult.
DCSync is a technique that makes attacks against the DC easier. Instead of breaking into a DC, an attacker takes advantage of normal processes (such as password replication between DCs) to collect password hashes by impersonating a DC.
Because DCSync is a stepping-stone for other dangerous attacks, detecting DCSync is important. Learn the basics of how a DCSync attack works, how ExtraHop Reveal(x) detects DCSync traffic, and how to prevent these attacks.
What is DCSync?
DCSync is a technique used to get user credentials. This method locates a DC, requests directory replication, and collects password hashes from the subsequent response. DCSync was created by Benjamin Delpy and Vincent Le Toux in 2015 and is a feature of the Mimikatz tool.
Directory replication is a necessary process that helps administrators manage account information across multiple DCs in an IT environment, which might contain several domains. If a user changes their password, directory replication ensures that these account credentials are updated across domains and that authentication goes smoothly for that user.
A successful DCSync attack requires access to an administrator account with Replicate Directory Changes privileges which allow that account to collect password hashes from the DC. While compromising an administrator account (or escalating privileges) presents challenges for the attacker, requesting replicated data from the DC is more convenient than compromising a DC.
DCSync is frequently coupled with other attacks. It might be a next step after exploiting vulnerabilities such as Zerologon, which provides attackers with the necessary privileges. DCSync can also be a precursor for dangerous attacks such as golden ticket, which is made possible after collecting the password hash from the KRBTGT account (an important administrative account in AD).
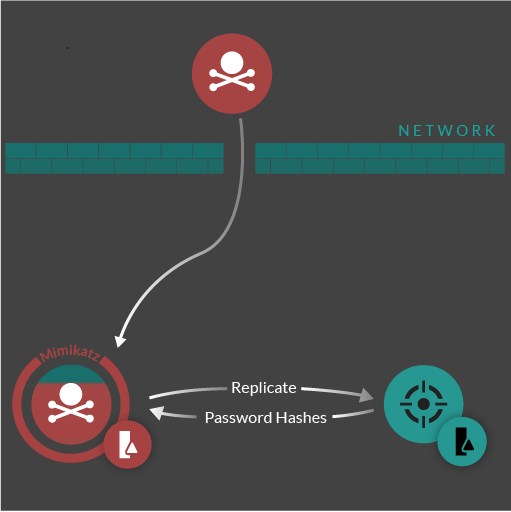
The DCSync attack workflow.
How DCSync Works
DCSync leverages the Microsoft Directory Replication Service Remote (MS-DRSR) protocol to request replicated data from a DC. MS-DRSR is based on the remote procedure call (RPC) network protocol, which enables communication between a client and server. For example, MS-DRSR includes RPC interfaces (such as drsuapi) with operations (such as DRSGetNCChanges). The interfaces are located on the DC server, and the operation is similar to a procedure command. When an administrator wants to retrieve a recently updated password hash from a DC, the administrator's client sends an RPC request to call the interface and operation (drsuapi:DRSGetNSChanges) on the DC server. The action of calling the interface and operation runs the procedure.
After acquiring the necessary privileges, the attacker runs the lsadump::dcsync command in Mimikatz to collect the password hash for their target. Mimikatz locates the DC for the target domain and sends RPC requests from the compromised client that request the password hash from that DC.
How to Detect DCSync Attacks
Network monitoring is the primary method for detecting DCSync because RPC is a network protocol. Directory replication activities can create logs, but attackers can also clear event logs or stop threads from collecting logs with Mimikatz or Invoke-Phant0m tools.
ExtraHop automatically detects unusual RPC traffic that is associated with directory replication between DCs and devices that do not usually submit these requests.
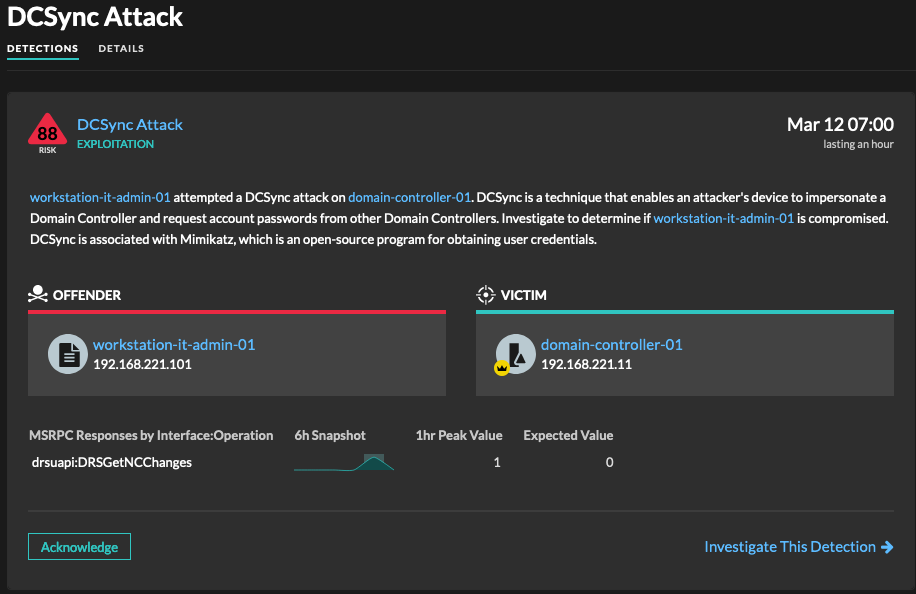
The detection card displays which device (offender) sent RPC requests to request password hashes from a DC (victim).
Evidence of a DCSync attack points to an advanced persistent threat (APT), where the attacker has an established presence on the network, has escalated their privileges to administrative domain levels, and is close to achieving their ultimate attack objective. When you investigate a detection, you can review related detections to DCSync behavior to confirm APT activity.
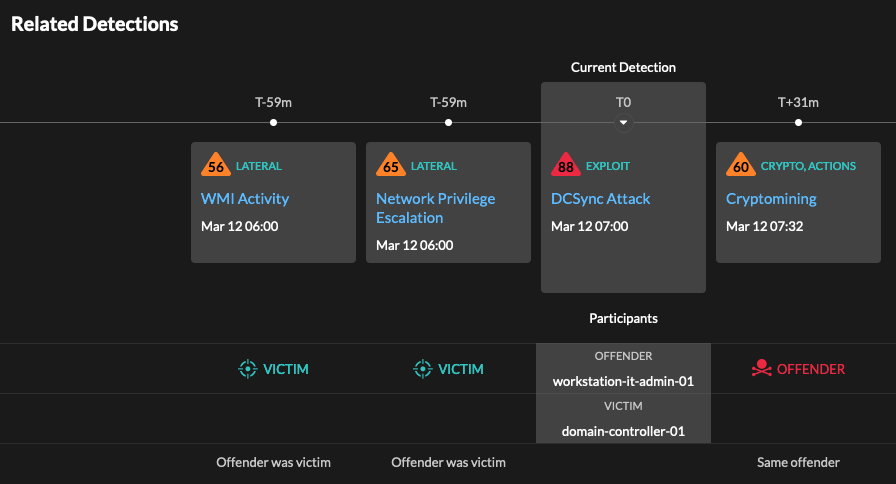
The related detections, which occurred before the DCSync attack, highlight behaviors associated with an advanced attack campaign.
How to Prevent DCSync
Because DCSync takes advantage of normal AD functionality, this attack can be challenging to prevent. Blocking directory replication would complicate authentication across the enterprise. But there are general steps you can take to block attackers from gaining access to the administrator accounts that are needed to perform DCSync.
First, strictly manage the users and groups who have the following privileges, which allow directory replication from a DC:
- Replicate Directory Changes
- Replicate Directory Changes All
- Replicate Directory Changes In Filtered Set
Domain and Enterprise Administrators have these privileges by default. To protect these accounts, follow best practices to secure privileged account access. For example, implement strict login controls on devices with highly privileged users to reduce the exposure of credentials stored in memory to attackers. And enforce strong authentication policies.
Finally, collecting Windows event logs for replication events and AD object changes (such as Event ID 4662) might help with additional monitoring.
Stay vigilant for unusual RPC requests to prevent attackers from collecting sensitive and critical information about network accounts.
To see how ExtraHop Reveal(x) detects DCSync attacks, explore our demo.
