Microsoft Active Directory (AD) is a target-rich environment for malicious actors. Attackers hone in on it because it's widely used and remains backward compatible with many versions of Microsoft Windows and Server environments. Due to the complexity of AD, properly securing these environments is a non-trivial task fraught with pitfalls and unintended consequences.
In addition to the inherent configuration issues, Microsoft Active Directory relies on NTLM and Kerberos to manage authentication and a number of application protocols that are utilized for application-level tasks like data sharing and system management, including SMBv3, LDAP, MS-RPC, and WINRM. AD relies heavily on these protocols which have diverse capabilities, making them especially useful to malicious actors working to evade security. This approach is what is commonly referred to as living-off-the-land, i.e. leveraging native tools, applications, and protocols to evade security controls and detection.
Why Traditional Detection Techniques Fall Short
Detection of attacks in clear text protocols has been the mainstay of traditional security methodology for decades. However, these detection techniques have always suffered from a variety of limitations inherent to the premises upon which they were built. These limitations leave defenders at a disadvantage especially when combined with the increasing use of encryption as a detection evasion mechanism.
Traditional security technologies such as firewalls and proxy devices are designed to evaluate traffic passing through gateway devices, leaving them blind to laterally moving network traffic. Additionally, these technologies have generally addressed decryption as an add-on rather than part of the tool's core functionality resulting in a variety of limitations such as throughput and packet-per-second degradation, limited traffic analysis capabilities, and limited support or no support for commonly abused protocols such as MS-RPC, SMBv3, LDAP, and WINRM. To make matters worse, attackers can choose to encrypt these protocols on demand, simultaneously creating a new class of Active Directory living-off-the-land attacks and leaving traditional security technology completely blind to malicious traffic.
The most common response to the inherent limitations of firewall and proxy solutions is the deployment of IDS/IPS technology to evaluate traffic in the east-west corridor. However, this solution suffers from the same performance issues as firewalls and proxy solutions while heavily relying on signature-based and flow-based detection methodologies. In addition to being prone to false-positive detections, this makes IDS/IPS solutions easy to evade by both traditional attack techniques as well as the encrypted living-off-the-land approach.
NDR Takes Over for Traditional Security
Network detection and response (NDR) works to address the limitations of traditional security technologies by focusing on decrypting and fully parsing traffic in the east-west corridor. By using specially designed parsers and AI to build baselines for the expected behavior of network devices, NDR is able to provide high-confidence, low-noise security detections on large quantities of traffic. However, most NDR vendors are not performing continuous packet capture, stream reassembly, full protocol parsing, or decryption. The result is a heavy reliance on the statistical analysis of encrypted traffic, also known as encrypted traffic analytics (ETA), with no visibility into traffic payload.
While ETA has been around for years as the primary method to detect malicious-looking encrypted traffic, it is false-negative prone and fails to detect many attacks that do not produce a statistically relevant quantity of data or leverage protocols that are common within Active Directory environments such as the use of SMBv3 in PrintNightmare. In addition, the focus on statistical analysis creates a dearth of rich, contextual data while also leaving security personnel blind to the content of traffic. The result is a lengthy and error-prone data forensics, investigation, and response process.
NOTE: While many vendors claim support for a large number of protocols, these vendors are not performing protocol parsing, rather they are performing protocol identification which provides limited detection and visibility into these traffic flows.
The ExtraHop Approach
ExtraHop Reveal(x) 360 relies on a layered detection approach, evaluating traffic using rules, statistical analysis, and AI to detect malicious activity. Unlike other products, Reveal(x) is designed from the ground up for continuous packet capture and full-stream reassembly making it capable of performing decryption of Active Directory protocols at scale.
The decryption of Microsoft authentication protocols NTLM, and Kerberos with full protocol support for TLS, LDAP, WINRM, MS-RPC, and SMBv3 ensure full visibility into encrypted traffic at line speeds of up to 100 Gbps while simultaneously ensuring visibility into and detection of encrypted living-off-the-land techniques. The ability to decrypt and fully parse both authentication and application-level protocols enables Reveal(x) to perform an unparalleled level of traffic inspection, significantly reducing an attacker's ability to remain covert. Other benefits of this approach include forensic-level record data on encrypted traffic. This data contains information such as the specific SQL queries, commands sent via MS-RPC, and LDAP enumeration behavior.
Ok, so I can hear you asking, "Jesse all that sounds fancy, but how much is reality, and how much is marketing fluff?" Fair question dear reader, fair question. To answer this let's take a look at an example detection:
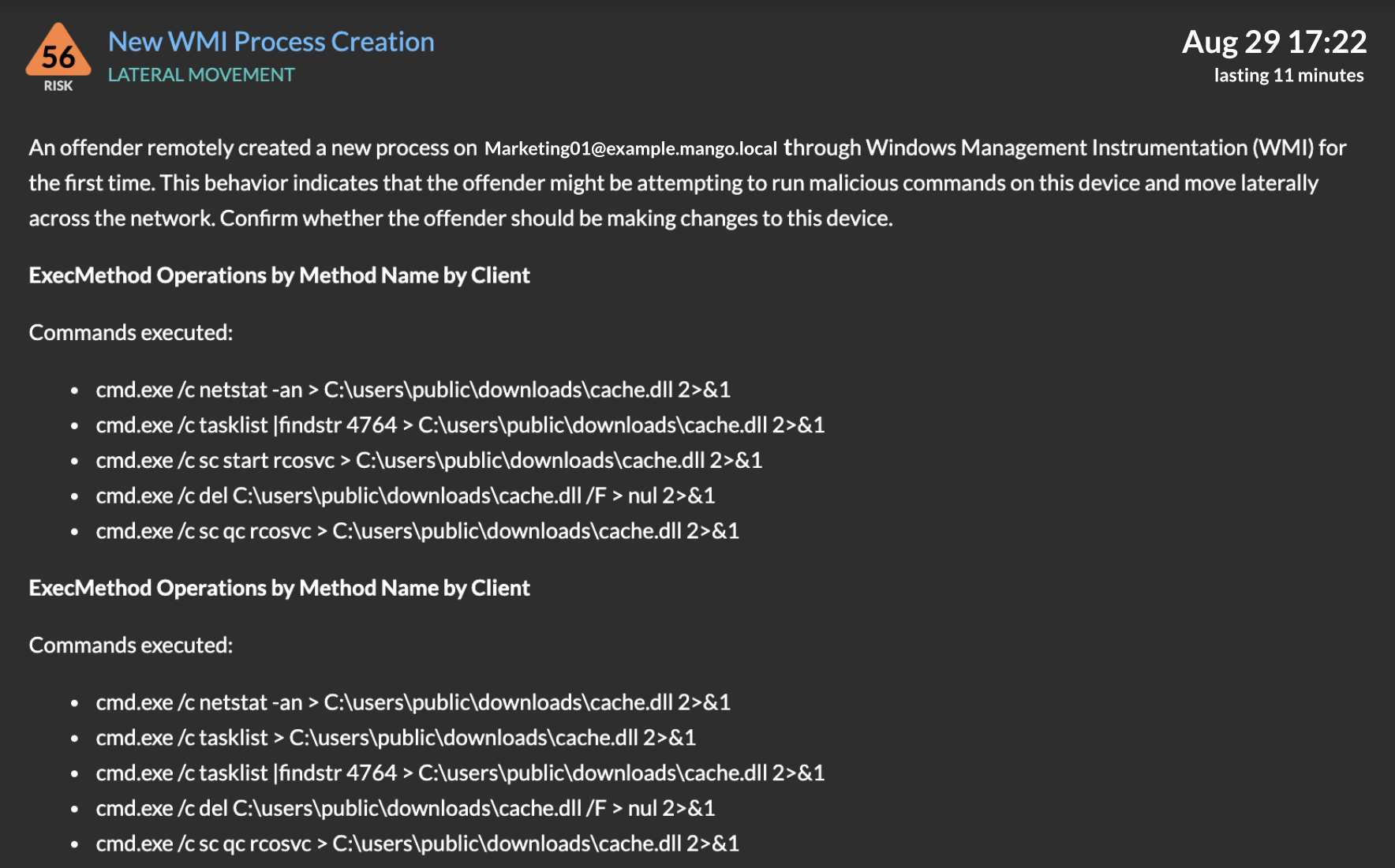
Reveal(x) 360 fully supports the MS-RPC protocol. As many administrators are aware, MS-RPC is one of several potential Microsoft protocols that can encapsulate WMI traffic. In this example, an encrypted MS-RPC session was decrypted and parsed, providing the Reveal(x) detection engines with full access to the data. Reveal(x) was then able to identify both the encapsulated WMI traffic and the specific commands being issued over WMI. The result is a comprehensive detection showing analysts precisely what the attacker was doing on the impacted workstations.
This is security uncompromised. This is security detections bolstered by decryption, TCP-stream reassembly, and full protocol parsing. It's the most advanced network detection AI in the world, finding attackers where they hide and enabling security responders with the comprehensive data they need to stop a breach.
What About Privacy?
When done well, decryption does not compromise privacy. As SANS put it in their 2021 SOC Survey, "In our follow-on questioning, we heard that the most common reason for not using TLS intercept is corporate concern over regulations and privacy. However, no one using TLS intercept reported running into legal issues. One respondent pointed out the need for management education in this area."
Decryption is Security Uncompromised
Unlike other vendors, ExtraHop does not compromise when it comes to identifying malicious activities. Support for the decryption and parsing of common Microsoft Active Directory protocols already provides more visibility and higher fidelity detections than any other vendor. With support for additional Microsoft protocols in the works, this is just the beginning.
ExtraHop is committed to providing security teams with the most comprehensive NDR toolkit in the industry. Whether threats are hiding in clear text, encrypted industry-standard, or Microsoft protocols, Reveal(x) will continue to lead by providing cutting-edge detection and response capabilities to your SecOps teams.
To learn more about how Reveal(x) 360 detects threats, read the whitepaper.
