PetitPotam is a proof of concept (POC) exploit that enables a new variant of NTLM relay attacks that target the Active Directory Certificate Service (ADCS). NTLM is an insecure protocol that enables a number of attacks. This particular attack is enabled by a vulnerability in the Encrypting File Services Remote Procedure Call (EFSRPC) protocol discovered by Gilles Lionel.
The vulnerability enables an unauthenticated attacker to force an authentication attempt between a victim domain controller and an attacker-controlled machine—the phase of the NTLM relay attack that usually requires user interaction—making this variant uniquely dangerous.
PetitPotam has been conflated with the full NTLM relay attack chain, specifically the ADCS attack showcased by Mimikatz author Benjamin Delpy. ExtraHop already detects the ADCS variant with our existing detection, but I want to share how NTLM relay attacks work and how we plan to anticipate and protect you from future variants derived from PetitPotam.
How to Detect NTLM Relay Attacks with ExtraHop
NTLM relay attacks have been a staple of Windows exploitation for a long time and remain a threat in many enterprise environments. While the technique is continuously updated and improved, ExtraHop is uniquely positioned to stop man-in-the-middle (MiTM) attacks by detecting relayed credentials in real time.
ExtraHop detections focus on techniques rather than tools, so our NTLM relay detection identifies exploit attempts independent of attack tools and specific variants.
The following diagram shows a typical NTLM relay attack:
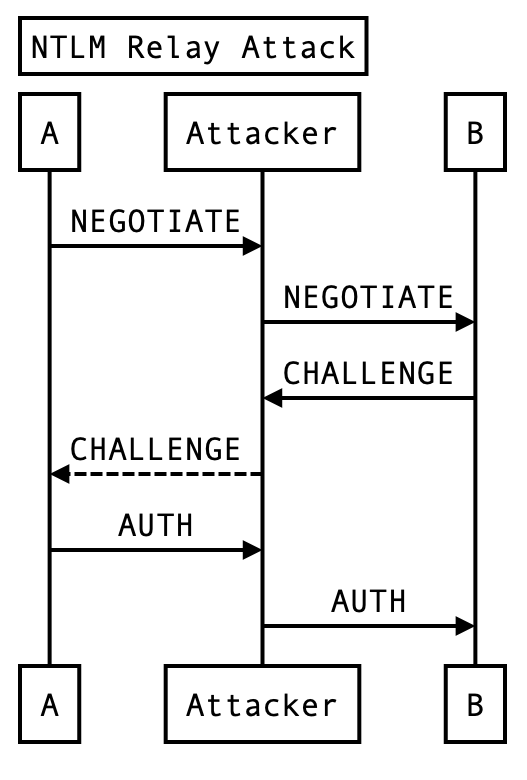
A successful NTLM relay requires an attacker to relay all three NTLM messages (NEGOTIATE, CHALLENGE, AUTH) from the target client to the victim server. If the relay is successful, the ExtraHop system captures the packets representing the CHALLENGE message.
By caching CHALLENGE messages and comparing them with each new request, the ExtraHop system can detect NTLM relay attempts as they happen. Because the NTLM server CHALLENGE message is a 16-byte random number generated by the victim server, the likelihood of the same CHALLENGE string being generated by two independent servers is extremely unlikely and meets our strict acceptance rate for false positives.
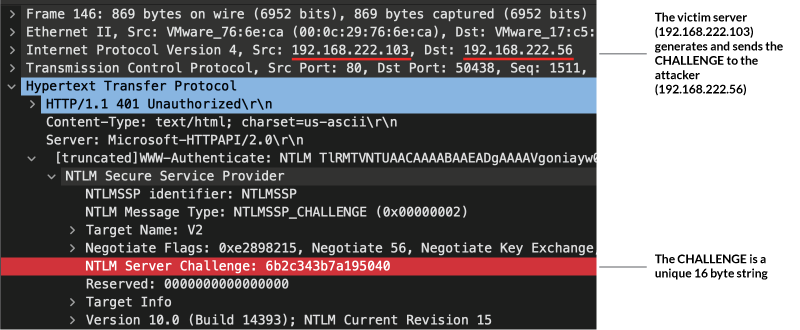
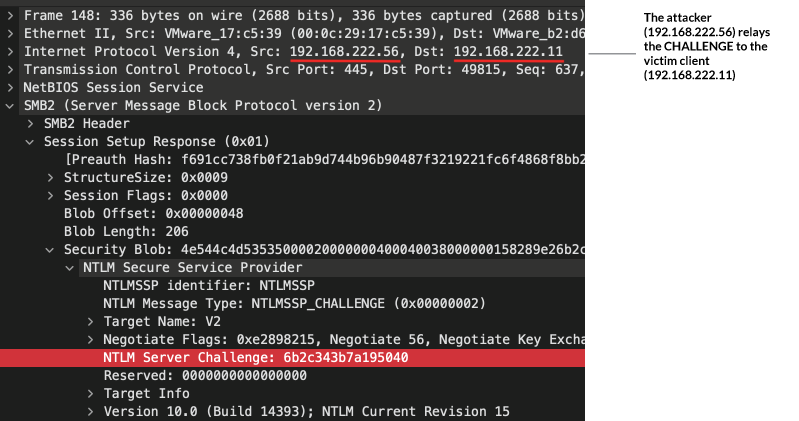
In the following screenshots, you can see that the NTLM challenge generated by the victim server is sent to the attacker, who then relays the challenge to the victim client.
What's Different About PetitPotam?
Previous methods, such as LLMNR poisoning, required user interaction to generate an authentication attempt. PetitPotam enables an attacker to force a victim client to authenticate to an arbitrary machine without any user interaction. The ADCS attack is nearly identical to the standard NTLM relay depicted above, with the addition of the vulnerable EFSRPC call that forces the initial authentication attempt:
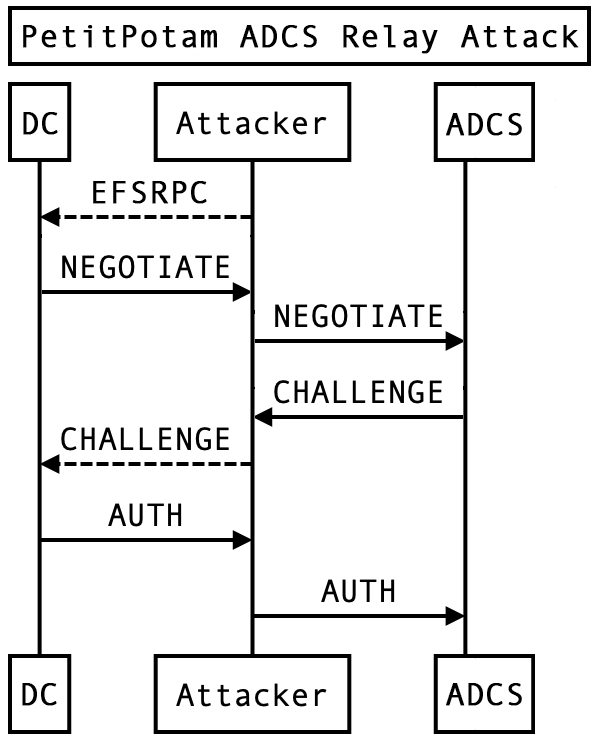
For any variant of NTLM relay to succeed, a previously issued CHALLENGE message must be relayed to the victim client. This defining characteristic of the attack technique is how we can identify all NTLM relay attempts with confidence that our detection will protect our users from PetitPotam and newer variants of this attack.
Attack Tool Landscape & Timeline
Here is a look at how this attack unfolded:
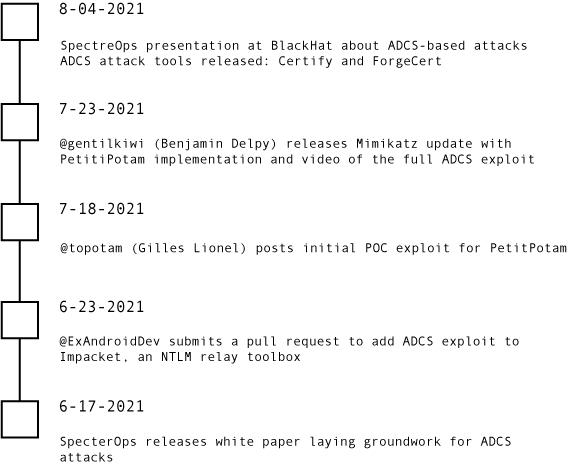
Source Links
- SpecterOps white paper
- Pull request from @ExAndroidDev
- POC from @topotam (Gilles Lionel)
- Mimikatz release notes
- Impacket toolkit
- Tweet and video from @gentilkiwi (Benjamin Delpy)
- SpecterOps presentation at BlackHat 2021
- ADCS attack tools: Certify, ForgeCert
What's Next?
With PetitPotam added to well-known Windows attack tools like Mimikatz and Impacket, we expect to see an increase of ADCS attacks in the wild, as well as PetitPotam chained with other types of common Windows vulnerabilities.
With new exploit vectors and attack tools released every day, ExtraHop offers defense against classic attacks like NTLM relay attacks as well as new and emerging threats. By identifying the technique as broadly as possible, we provide forward-looking protection as well as the most granular tools for investigation and forensics.
