2.1 million people over eleven counties in North Texas depend on Tarrant Regional Water District (TRWD) for their water supply and flood control measures. As a critical part of our national infrastructure, they are well aware of the rising risk of advanced persistent threats, but they also have a small network team with no dedicated in-house security staff.
So how does a team like the one at TRWD take on security and regain the upper hand? Should they find themselves face-to-face against sophisticated cybercriminals, it would be a true underdog story—but this small, savvy team in North Texas turned to ExtraHop Reveal(x) network detection and response (NDR) to help them take on advanced threats.
Network Architect Adam Bolden initially came to ExtraHop with a primary objective in mind: to add robust network visibility for TRWD's complex network infrastructure. But modern networks, as it turns out, are dynamic and constantly evolving. ExtraHop Reveal(x) was designed with that in mind.
The Changing Elements of Cybersecurity
When we first meet new customers like TRWD, it's common for them to have one mitigating factor or a single goal that Reveal(x) can solve—but our customers also gain a lot of value by putting our machine learning-based solution to work in more ways than originally intended. While Reveal(x) was designed to be configured and customized to fit an organization's needs, we still learn a lot about how our technology is used by listening to real-world users like TRWD.
Some of today's biggest security threats consist of advanced nation-state actors and large-scale cyber gangs who use the techniques and tactics of advanced persistent threats to evade detection. This means that broad security coverage across physical networks, cloud environments, and IoT devices is now mandatory for organizations who wish to successfully defend against today's threat landscape.
Today's advanced threats are highly adaptive, but our machine learning-based detectors are too. Because Reveal(x) uses behavior-based detections to spot network anomalies across the entire environment, it's a defender's best asset against zero-day exploits and other advanced attacks, and it can easily scale to match the natural growth and change of an organization's network.
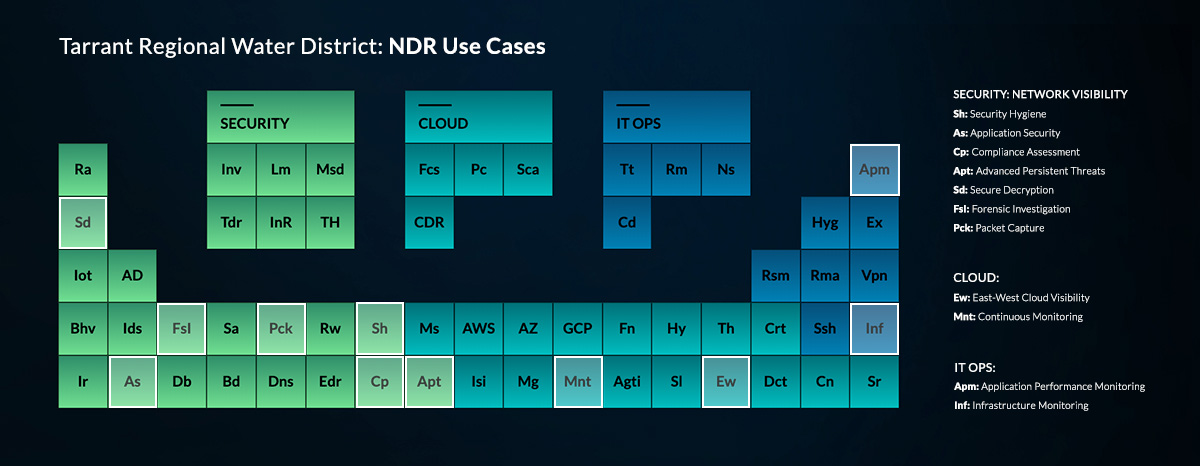
We wanted to see all the ways our customers use Reveal(x) to take back the advantage against advanced threats, so we mapped out the most common use cases across security, cloud visibility, and IT operations. It turns out, there are a lot. The Periodic table of Network Detection and Response NDR Use Cases helps visualize how a single solution can adapt to changing needs and strengthen security across nearly every element of a network to provide truly dynamic cyberdefense.
Reveal(x) for Security, Cloud, and IT Ops
Tarrant Regional Water District initially adopted Reveal(x) to answer a security mandate and boost visibility across their entire environment. They've expanded ExtraHop's footprint to include continuous security monitoring for their critical home-grown applications and use real-time detections to help meet security compliance. Reveal(x) also serves as a bridge into IT ops by enabling performance monitoring for applications and their geographically-dispersed network environments.
When the SUNBURST news broke, the network team had to quickly put on their security hats to investigate their DNS archives, looking for indicators of compromise. Like many organizations, they didn't enable DNS logging on domain controllers, which might have made detecting compromise near impossible. Instead, the team was able to use records, captured and stored by Reveal(x) to easily detect whether or not they had been affected. After the SUNBURST news, Bolden remarked, "Reveal(x) really saves our hide when it comes to identifying potential incidents or a vulnerability—it just helps me sleep better!"
With infinite configurations and solutions, no two Reveal(x) customers are alike, but like a lot of customers, TRWD is implementing new Reveal(x) features and capabilities as their needs change.
To view the elements of cyberdefense and how they can help organizations like yours, check out the Periodic Table of Reveal(x) Use Cases.