If you were faced with a new threat, would you have the right tools to effectively stop them? A stake to the heart would be effective, but risky. Is garlic just a myth? Sunlight? What if it's a different kind of threat entirely? In the world of cybersecurity, the real-world villains are almost as mysterious as the ones out of an Anne Rice novel. They lurk in the dark spots in your network, hide in busy network traffic, and wear disguises that make them look convincingly legit.
Since 2015, the MITRE ATT&CK matrix has helped security teams defend their organizations by understanding the habits of the adversary. By documenting and organizing the tactics, techniques, and procedures (TTPs) used by advanced persistent threats and creating a standard taxonomy for each TTP, ATT&CK empowered organizations with a greater ability to find out how attackers are inviting themselves in.
The skyrocketing sophistication and sheer volume of cyberattacks has increased the urgency for public and private sector organizations to tighten their defenses, but knowing about attacker techniques and procedures is only part of the picture. What use is it to know about Kerberos golden ticket attacks (MITRE T1558.001) or abuse of Remote Desktop Protocol (T1021.001) if you don't know how to stop it? While the ATT&CK matrix does list granular mitigation options for many attack tactics, MITRE D3FEND was created to focus exclusively on controls and countermeasures.
What is MITRE D3FEND?
Commissioned and funded by the NSA, MITRE D3FEND is a new framework of defensive countermeasures to help security professionals plan and tailor their defenses for common MITRE ATT&CK tactics. The D3FEND matrix includes countermeasures at every stage of attack, helping prevent, mitigate, remediate, and respond.
Like MITRE ATT&CK, D3FEND is structured as a matrix, divided into high-level strategies. In the case of D3FEND, there are currently five main defensive techniques: Harden, Detect, Isolate, Deceive, and Evict. Beneath each of those tactics are countermeasure technique categories, including Network Traffic Analysis and User Behavior Analysis.
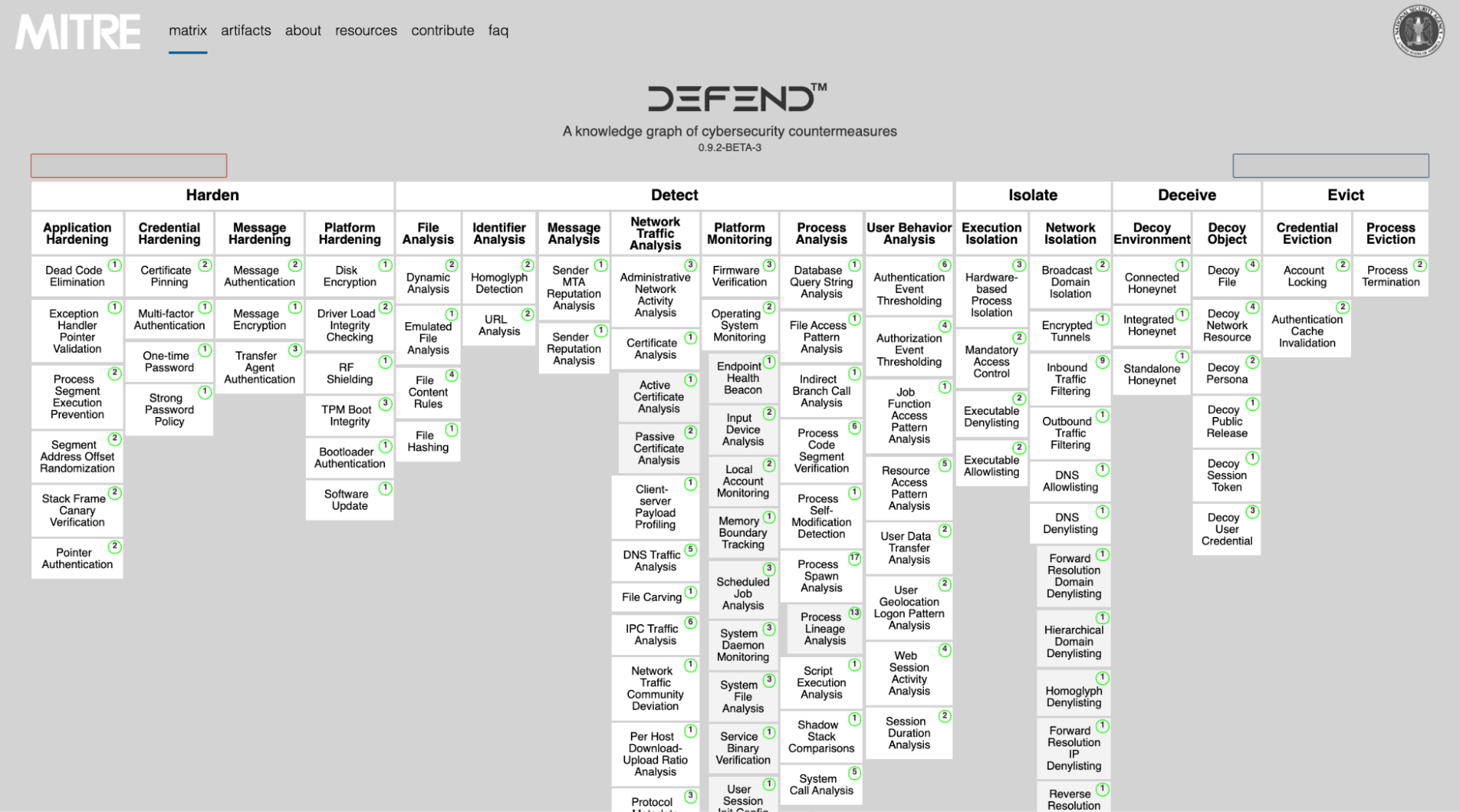
MITRE goes further into countermeasure techniques to list out specific countermeasures. For example, the Network Traffic Analysis countermeasure technique lists Protocol Metadata Anomaly Detection among the list of specific techniques.
Each countermeasure listing contains a definition and a brief description of how the countermeasure works. It also cross references defenses with attacker techniques on the ATT&CK framework.
How to Use MITRE D3FEND to Improve Security.
Like ATT&CK, D3FEND is designed to help create a standard vocabulary by defining the specific functions of countermeasures. By doing this, the matrix can help organizations understand counter measures in detail, which supports both high-level executives comparing the cost vs. risk of a new security tool, and the security architect looking to build or test a strategic toolset.
At a very basic level, security teams can look at each of the countermeasures listed in D3FEND and identify whether (and how) that countermeasure is being used by their organization today. This allows organizations to identify defensive gaps and make more strategic security tooling decisions.
For organizations considering new security solutions, D3FEND is useful for considering how much investment it would take to implement the countermeasure, whether it helps them increase security maturity, hygiene, and posture, or reduces attack surface. By comparing the functions of a security solution with the corresponding ATT&CK offensive technique, an organization can gain insight into how well it might perform.
D3FEND also helps organizations identify drawbacks and considerations for countermeasures. When considering security solutions, an organization must be able to identify ways that an attacker may evade detection or the risk of false positives for a busy security team. This insight can help organizations hone their security processes to stay ahead of adversaries.
To learn more about the MITRE ATT&CK framework, and how network detection and response supports ATT&CK and D3FEND coverage, read our article on Reveal(x) and MITRE ATT&CK integrations.
