While release notes provide a comprehensive view of our 8.6 release updates, here is a preview of our most exciting new features.
Detections
In 8.6, users can add detections to an Investigation. Investigations show a map of the offenders and victims from the added detections, so you can more easily visualize connections and determine whether your network is under attack or experiencing a broader incident.
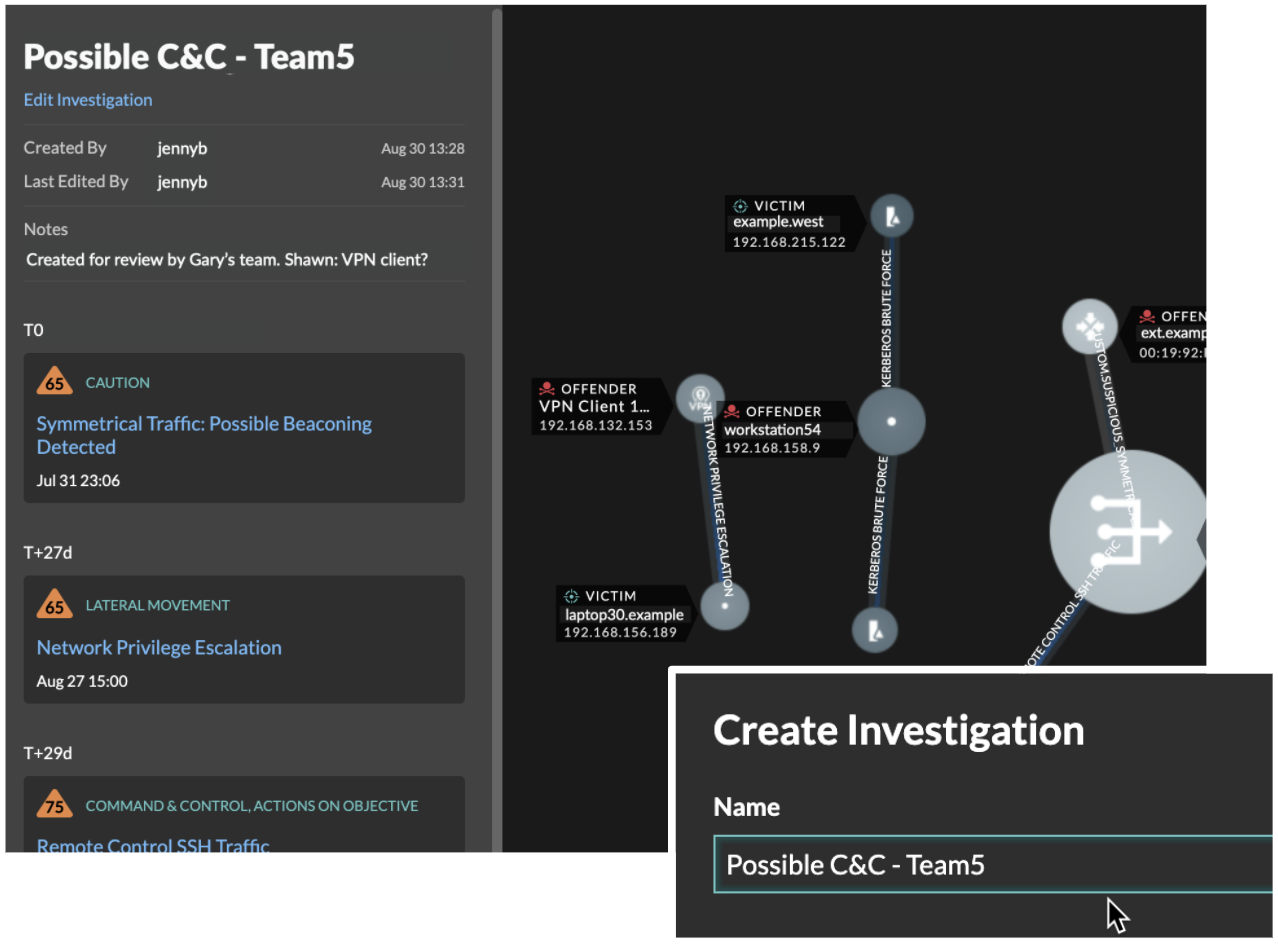
Detection Notifications have expanded from email to webhooks. Write a webhook for a target app, so the right team can be notified immediately and shorten their response time. Check out the example templates for Slack, Microsoft Teams, and Google Chat in our Webhook Reference.
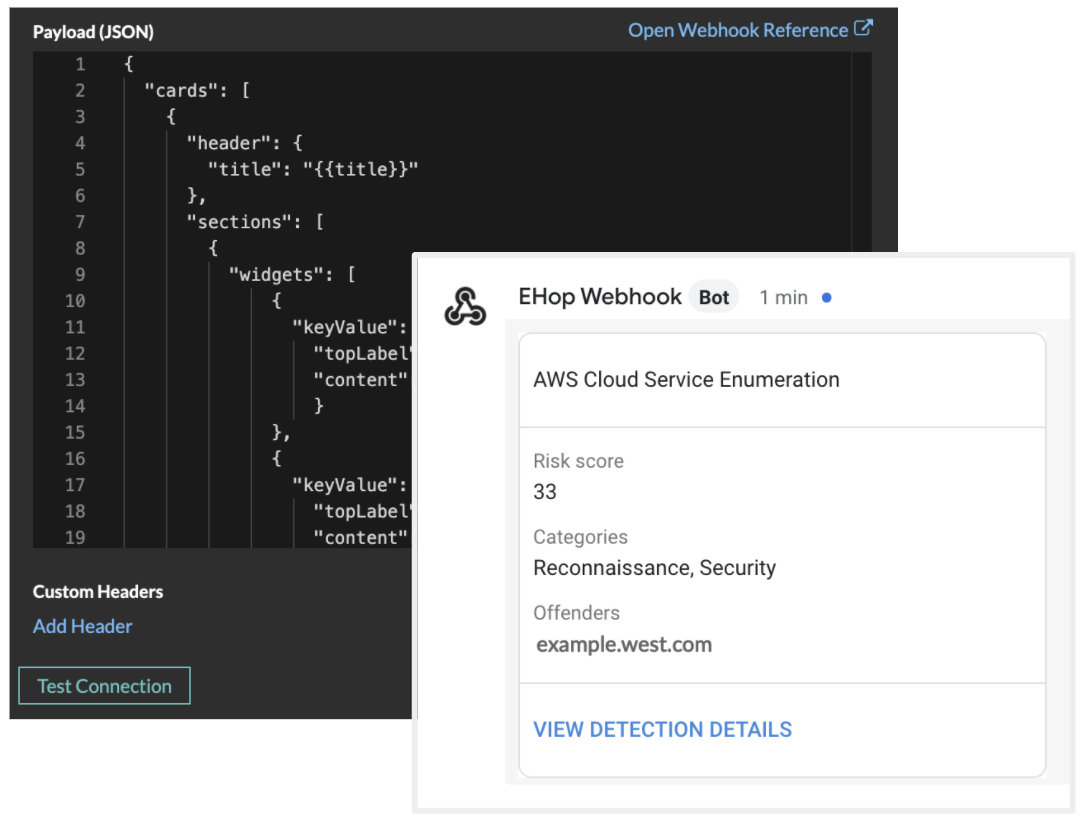
You can also now create a rule to be notified when the risk score changes above a certain threshold.
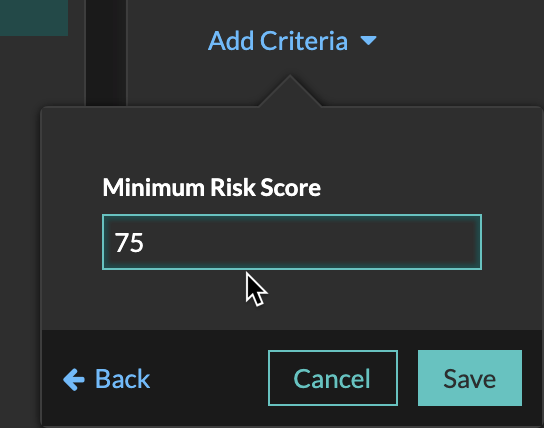
And you can filter by the risk score.
Devices
The Device Overview page now includes a Similar Devices tab. Click to view devices that were observed with similar network traffic behavior by machine-learning analysis. Similar devices can provide insight into normal device behavior when threat hunting.
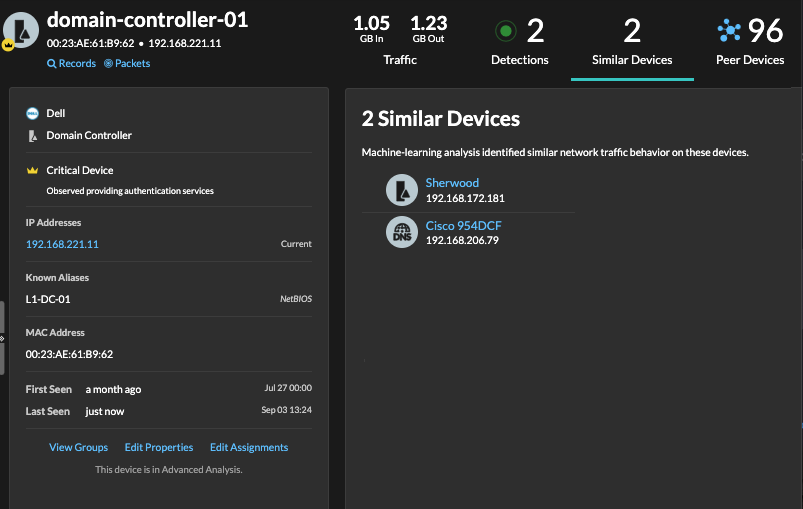
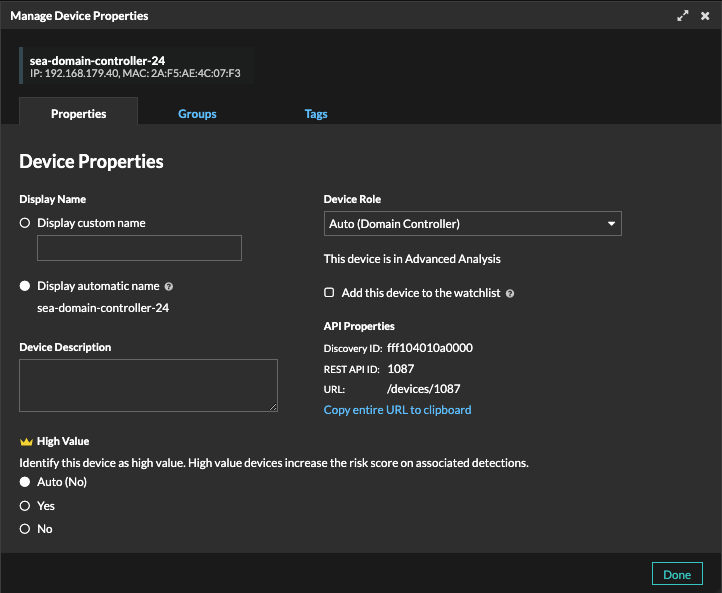
The ExtraHop system automatically identifies high value devices that provide authentication or essential services on the network. You can manually add or remove the high value designation from a device's properties, but this change can affect the risk score in detections where the device is a participant and can affect results when filtering for high value devices.
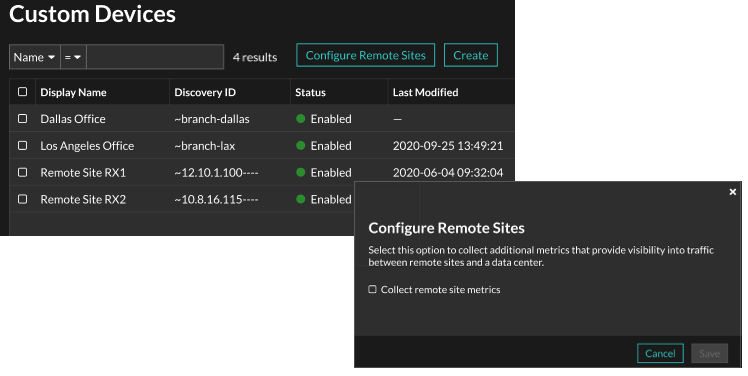
You can configure a custom device to collect metrics from remote sites such as inbound and outbound throughput, retransmission timeouts, round trip times, and zero windows. Remote site metrics enable you to easily gain visibility into traffic between remote sites and a data center.
Reveal(x) 360 Only
Reveal(x) 360 users are invited to try out our beta Microsoft 365 Integration. Retrieve data from Microsoft 365 and Azure Active Directory for analysis by the ExtraHop system through metrics, records, and detections.
Visit our Customer Community for upgrade options and let us know if you have any questions!
