Earlier this month the National Security Agency (NSA) issued a technical advisory warning of an attack dubbed ALPACA. It highlights the cybersecurity risks of using wildcard TLS certificates. So how does this attack work and why does it make wildcard certificates more concerning?
What is the ALPACA Attack?
The application layer protocol content confusion attack (ALPACA) was first disclosed in June and presented at Black Hat USA 2021. To understand ALPACA, it's helpful to understand how TLS works: The protocol is designed to protect data in transit during a transaction, but it does not bind TCP connections to the intended application layer protocol—whether that's HTTP, SMTP, or any of the many other protocols often secured with TLS. In practice, this means that while TLS secures the data as it's transported and verifies the server name it's connecting to, it doesn't check the application the data is being sent to or even the validity of that data.
In an ALPACA attack, threat actors are able to exploit the above using man-in-the-middle techniques to redirect a victim's browser so that it connects to a different FTP, POP3, or other server that uses the same certificate. The attacker tricks the browser into sending private information to the other server. By doing this, the attacker can extract session cookies and other private data or execute arbitrary JavaScript in the web browser.
The researchers estimate that 1.4 million web servers are vulnerable to these cross-protocol attacks. Of these, 119,000 web servers could be attacked via exploitable application servers.
#### What Are Wildcard Certificates? A wildcard certificate is a public key certificate that is used to authenticate multiple hosts. For example, the certificate "*.example.com" can be used for "www.example[.]com", "smtp.example[.]com" and "ftp.example[.]com". It has therefore become a popular way for administrators who are under pressure to rapidly roll out and manage servers across large numbers of hosts. It saves time and money because a single certificate can be applied to all relevant servers.
What Are the Cybersecurity Risks of Wildcard Certificates?
If the same certificate is used both for HTTPS and another SSL-enabled protocol server such as SMTPS or FTPS, then an attacker can trick the browser into exfiltrating session cookies or executing a cross-site scripting (XSS) attack. XSS is a common technique for gaining initial access, and it can also be used for lateral movement.
The convenience of sharing certificates also makes them a security risk. As the NSA explains, "If one server hosting a wildcard certificate is compromised, all other servers that can be represented by the wildcard certificate are put at risk. A malicious cyber actor with a wildcard certificate's private key can impersonate any of the sites within the certificate's scope and gain access to user credentials and protected information."
Using wildcard certificates increases the risk of ALPACA by opening the door to the cross-protocol attacks described above. ALPACA threat actors can exploit the security weaknesses of wildcard certificates by redirecting traffic from one host to another.
How Might This Attack Play Out?
The researchers that disclosed this vulnerability focused their efforts on a few protocols, including SMTP, IMAP, POP3, and FTP. However, they noted that there are "hundreds of possible cross-protocol scenarios possible with current TLS enabled applications and servers."
The NSA's report on the ALPACA attack also noted that "While the conditions permitting this complicated technique to succeed are uncommon, ongoing research in this area is likely to identify additional configurations vulnerable to this type of malicious activity."
Check for Wildcard Certificates in Your Organization
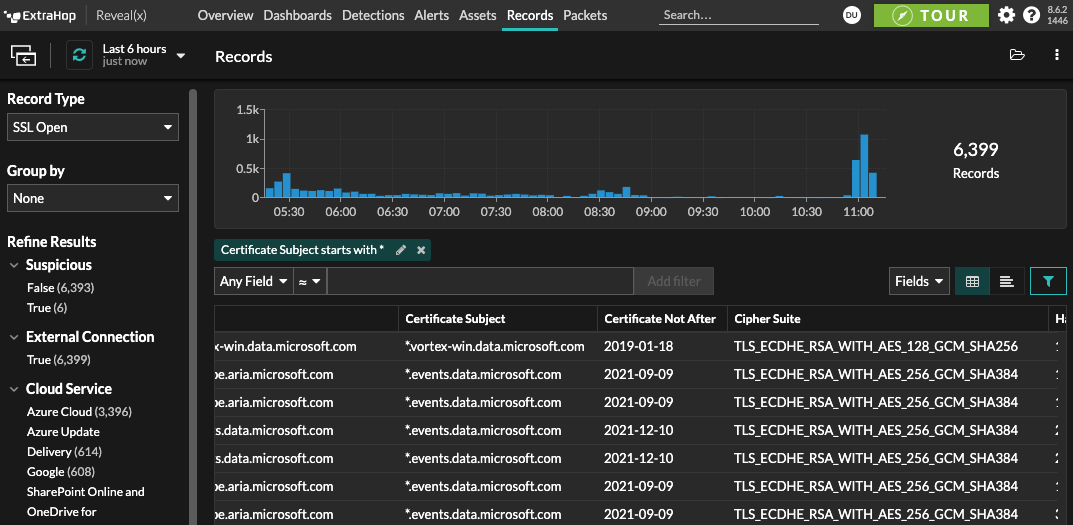
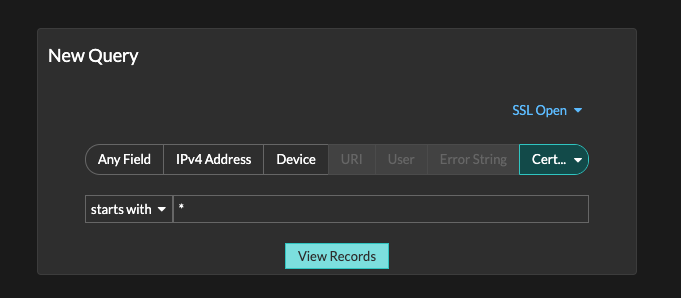
ExtraHop Reveal(x) 360 network detection and response (NDR) can discover wildcard certificates in use on your network, as well as expired certificates and self-signed certificates that also represent security risk. In the Records tab, select SSL Open as your record type, then filter by Certificate Subject Starts With * and click View Records. Then add a filter for your own domain to view only your own certificates.
This will yield a list of all SSL Open events that used a wildcard certificate in your environment during the selected time window. You can explore the list to make sure you don't have any wildcard certificates that are leaving you vulnerable to the ALPACA attack technique by being too broadly scoped or being used across multiple server types such as HTTP and SMTP.
Through passive observation of network traffic, Reveal(x) can identify which systems are using which certificates so that you can quickly identify any that are scoped too broadly, detect lateral movement, and remedy the situation to reduce your risk of future ALPACA attacks.