Cities are swimming in sensitive data and interesting traffic. Between planning and permitting, courts, fire, utilities, and services like parks and libraries—there's a lot to what makes a city function. It's also a huge attack surface.
On a recent training exercise with a U.S. city, we were looking at inbound suspicious connections in Reveal(x) 360. Hot tip: An awesome place to start looking for bad guys is Overview – Perimeter.
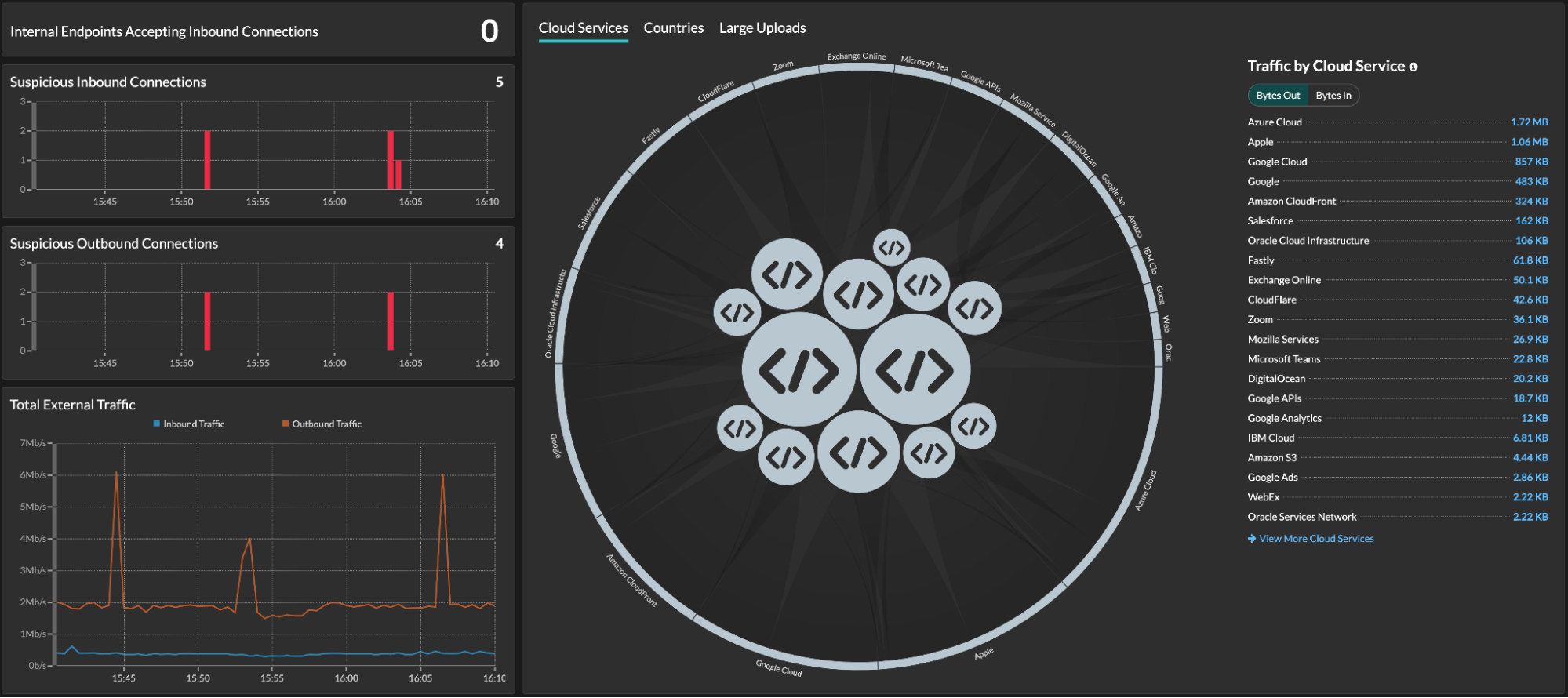
In the suspicious outbound connections dashboard, ExtraHop gives special scrutiny to internal-external traffic, regardless of source or protocol.
Ideally, you'd expect (or hope) to not see any results, but we saw a non-zero number of connections from suspicious IPs. Interesting… Click.
We noticed one popular target was a system we'll call coptrax.city.com. CopTrax is a full-featured evidence suite for law enforcement, including body cams. This city's police department uses CopTrax for dashcams too.
The first question that came to mind is: Why is the body cam system exposed to the internet?
Targets for Attacks
It's important to stop here and note the sensitivity of this information, and what can happen should it land in the wrong hands: Last year, a ransomware group threatened to leak 250 gigabytes of stolen data containing operations, disciplinary records, and informant information from a police department. The stakes were high, particularly for the safety of those informants—some of whom were in criminal gangs—and the stability of the criminal investigations the informants were assisting.
The average cost of a data breach in 2021 was $4.24 million, according to the IBM Cost of a Data Breach Report 2021—that's the highest cost in 17 years. In addition, just last year, it's been reported that 68% of government organizations were compromised by at least one cyberattack, and cyberattacks on police departments are a growing and costly trend. Bad actors know city agencies, and law enforcement offices in particular, are targets for stealing sensitive data.
Search for External IPs
Back to this training. We start looking at the external IPs.
A couple of the external IPs were hosted out of Digital Ocean, a compute-for-hire that could be anybody. Of those IPs, a couple of them were out of Amsterdam. This customer is in the U.S., and the network team could think of no legit reason why an IP in Amsterdam would connect to the city's camera system.
Although this customer was relieved that these bad actors didn't get through to the Comptrax system, it raised some major questions, like: Why is CopTrax exposed to the outside world? Who should be connecting to CopTrax?
It turned out this city had a number of different users connecting to it: City IPs, the vendor (who connects over VPN into a city IP), and the static IPs of the patrol cars that phone home their dashcam footage in real time.
Turning our attention to the firewall, we started digging. We learned the firewall permitted any source IP to connect over HTTP to the police camera system.
We add it to the list of needed changes and keep digging.
First, can the internet resolve the hostname? Turns out, yes.
$ nslookup coptrax.city.com 1.1.1.1
Server: 1.1.1.1
Address: 1.1.1.1#53
Non-authoritative answer:
Name: coptrax.city.com
Address: 216.xxx.yyy.zzz
Next, I turn to Shodan—a search engine that crawls the entire internet—to see what it knows about coptrax.city.com:
https://www.shodan.io/host/216.xxx.yyy.zzz
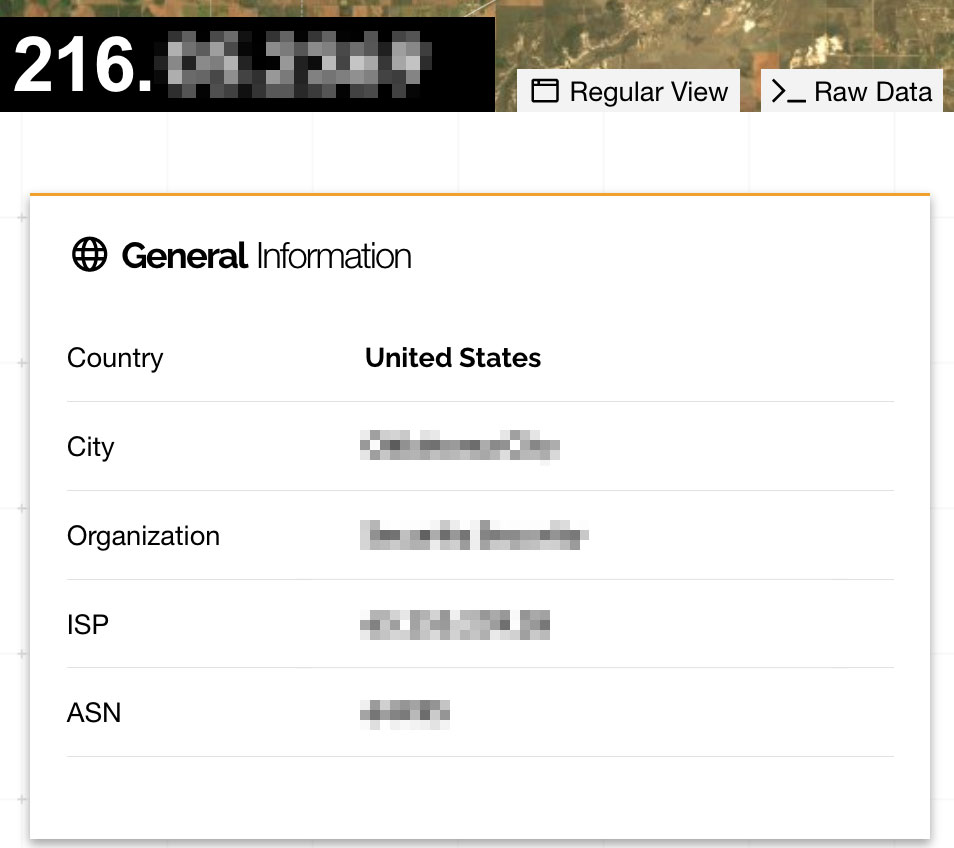
Yep, that's the right location. (ASN and city redacted)
Next, on the same screen, we see Shodan helpfully listing open ports.
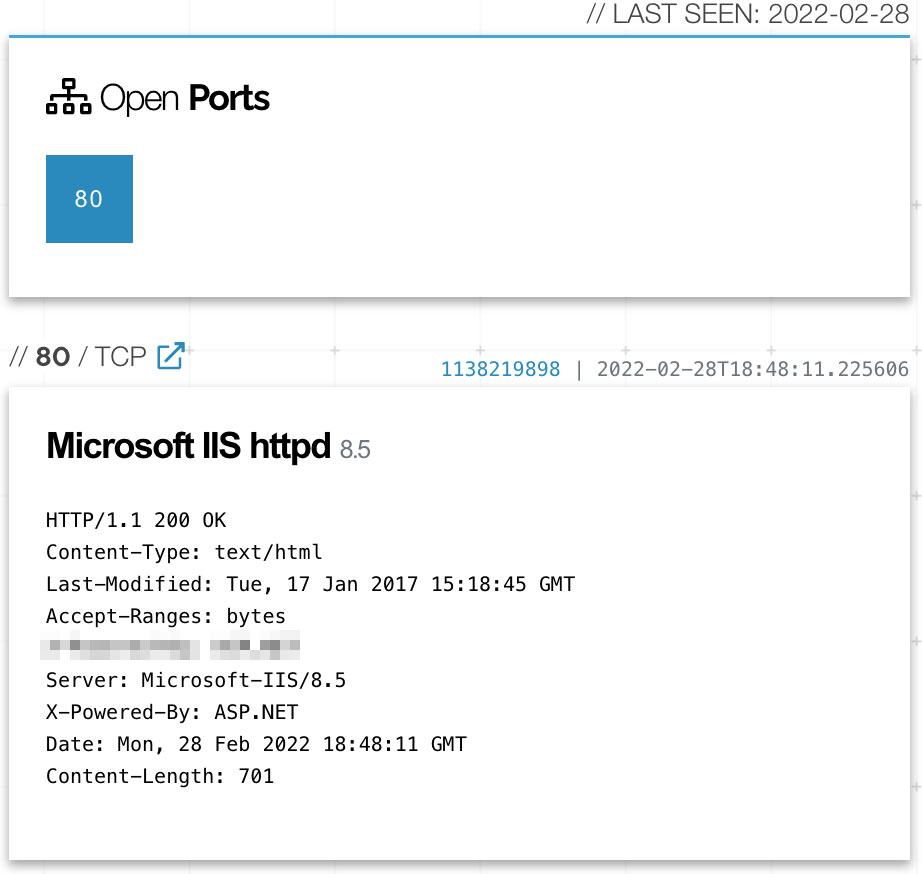
Yep, Port 80 was exposed to the outside world. Note that they are leaking the version of Microsoft IIS (8.5). It can host basically anything on the internet and this is handy if you're crafting an attack.
And for double-plus-extra goodness, we see that this version of Microsoft IIS has a specific vulnerability:
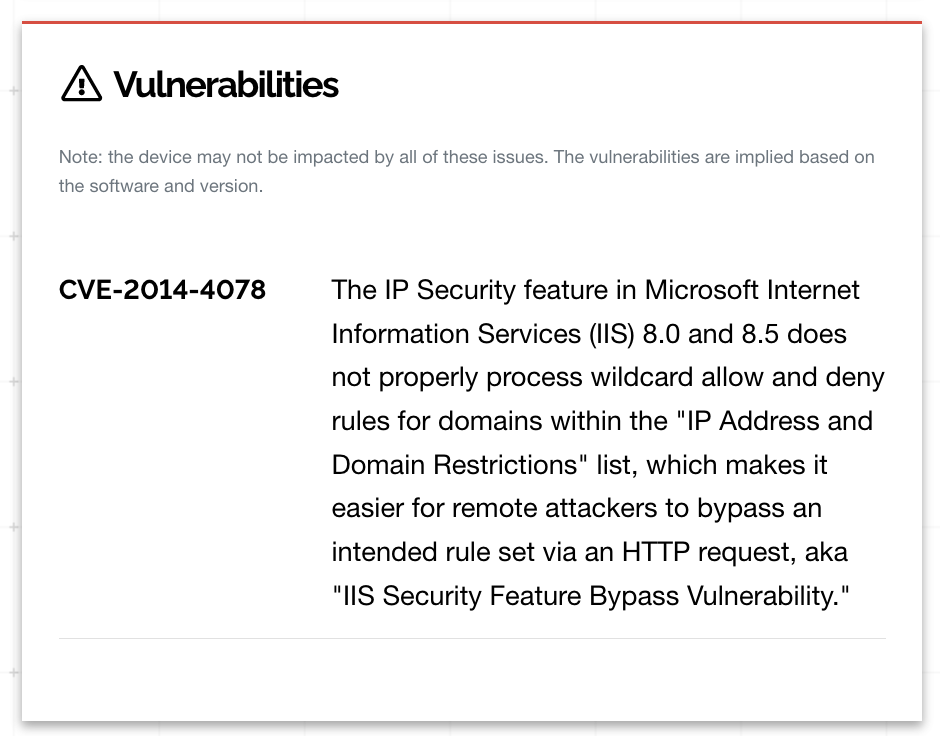
Update: I'm pleased to report that as of this writing, coptrax.city.com is no longer reachable from the internet. Progress.
