While release notes provide a comprehensive view of our 9.0 release updates, here is a preview of our most exciting new features.
Network Detection and Response
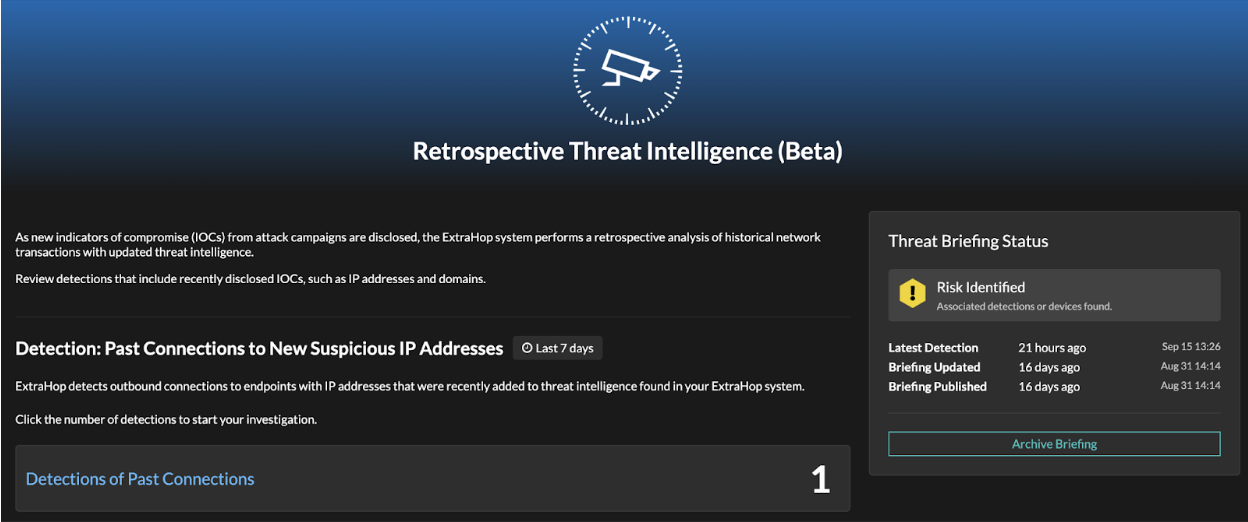
Retrospective Threat Intelligence (Beta)
Reveal(x) 360 users are able to see our retrospective threat intelligence, which applies new threat intelligence to suspicious connections that happened in the past. These detections can help you identify broader attack campaigns.
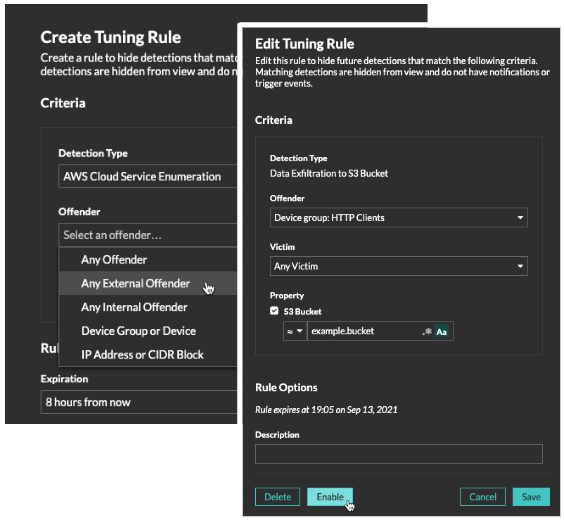
Detection Tuning
We've added the ability to add and edit tuning rules from the Tuning Rules page, and you can now specify participants in tuning rule criteria by their internal or external locality—which you define.
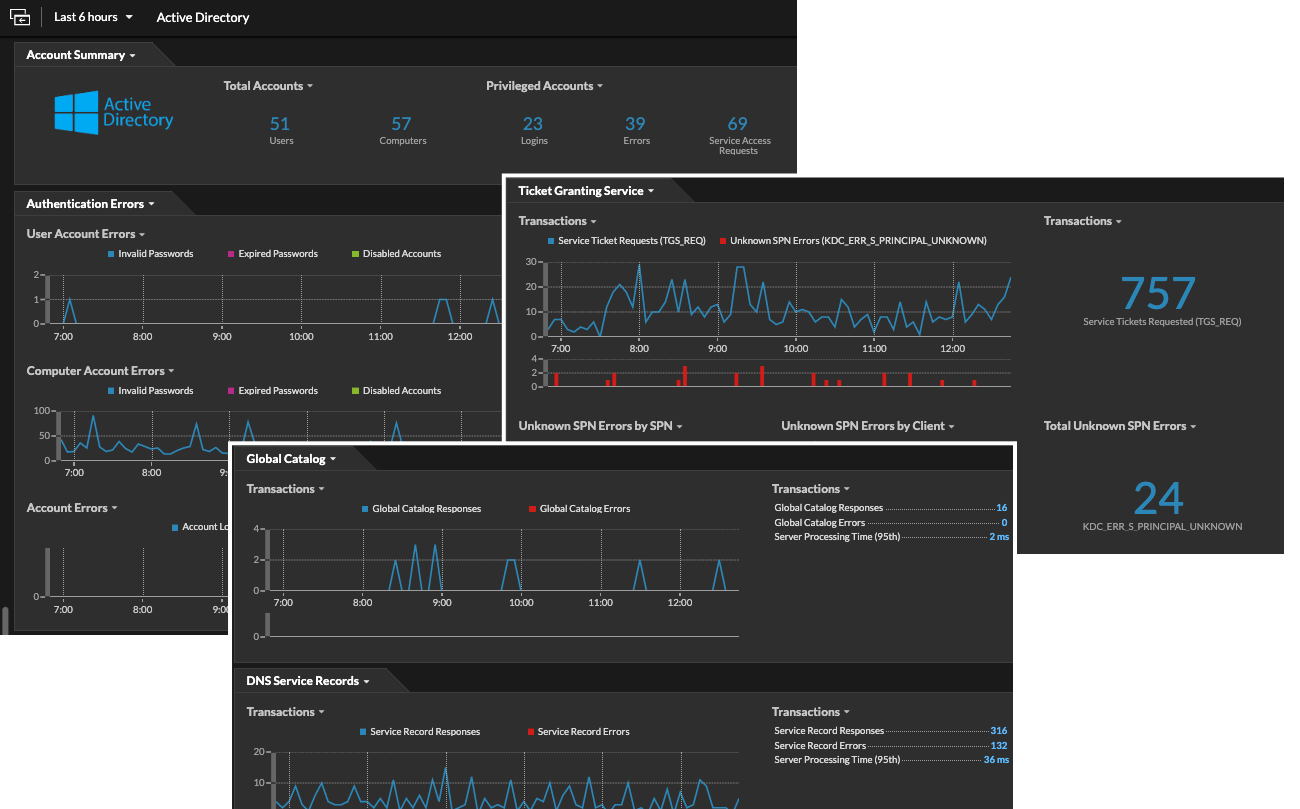
Dashboards
In 9.0, the new Active Directory dashboard provides visibility into Active Directory with new metrics, expanded Kerberos records, and privileged user specification.
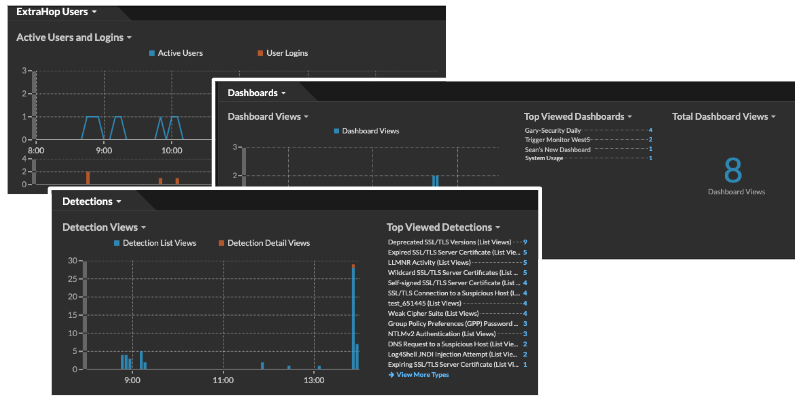
Administrators can now view user and product engagement metrics in the System Usage dashboard. This dashboard tracks active users in the ExtraHop system, and how those users are interacting with detections, investigations, and dashboards.
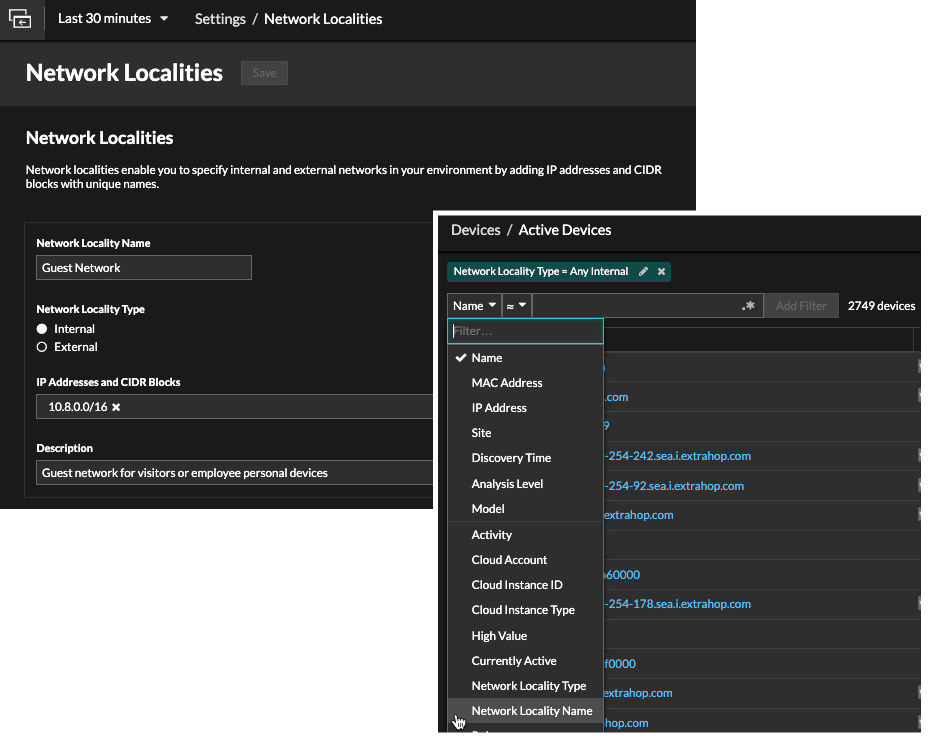
Custom Network Localities
You can now create custom localities such as "DMZ" or "guest network" that better reflect the structure of your network and enable you to filter records and devices by the locality name.
Cloud Threat Detection
AWS Workflows
Flow sensors now support AWS environments with multiple accounts. And, we've added the ability to leverage a Gateway Load Balancer as a traffic mirror target to send mirrored traffic to a sensor. This new approach eliminates the need to route traffic between workload and sensor VPCs, and significantly reduces data transfer charges when compared to Transit Gateway.
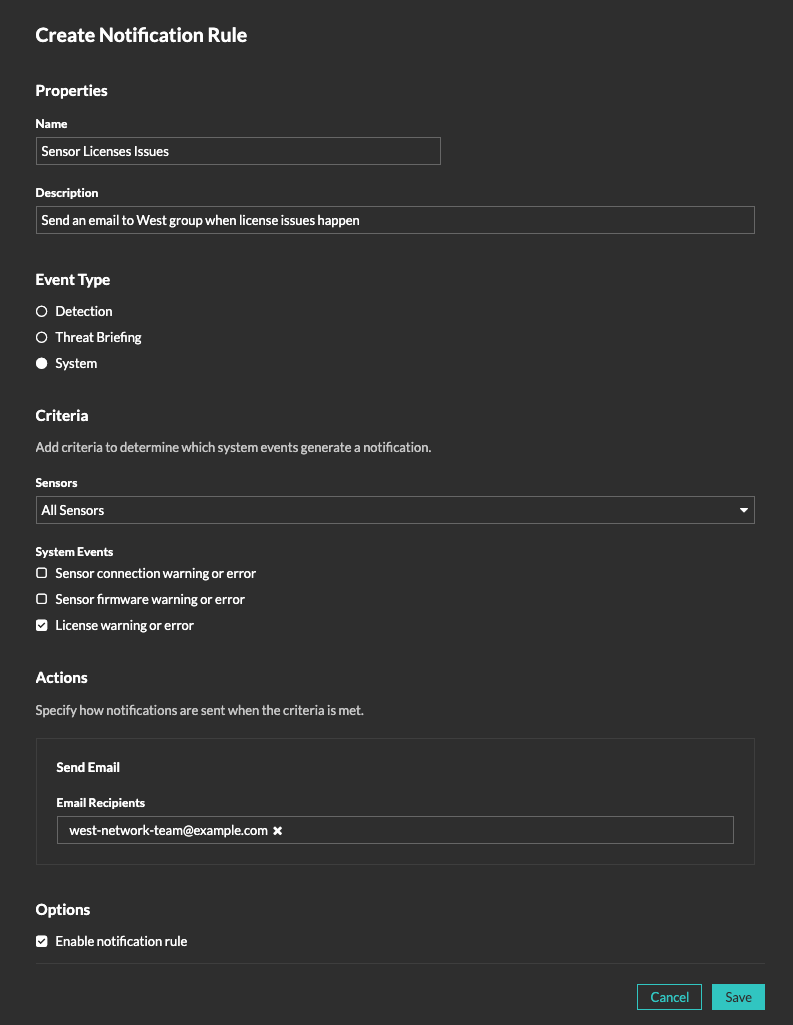
System Notification Rules
For Reveal(x) 360, you can now create a notification rule to email a recipient list whenever system events occur that might need attention such as a disconnected sensor, unsupported sensor firmware, or an expired sensor license.