ExtraHop today announced expanded capabilities to its Reveal(x) 360 network detection and response platform. The new capabilities, known as Automated Retrospective Detection (ARD), are designed to give security teams greater visibility into advanced threats hiding in older network data.
ARD draws on thousands of indicators of compromise (IOCs) to automatically search through historical network records for evidence of previously unknown threats as soon as new IOCs are released.
When a never-before-seen malware strain or zero-day exploit emerges, customers will be immediately alerted to detections of past attacks, minimizing dwell time and overall impact, while also saving security operations center (SOC) teams an enormous amount of time and manual effort.
The Problem Automated Retrospective Detection Solves
Many organizations lack the ability to identify advanced persistent threats, new malware, and zero day exploits that have been hiding in their environments for weeks or months because they can’t run detections on older network data. They can only run them on current data, which leaves them with significant blind spots.
Consequently, these organizations are forced to spend days and sometimes weeks conducting manual searches of historical network data to look for IOCs. These cumbersome manual searches of data–sometimes involving hundreds, or even thousands, of IP addresses–often take place during active cybersecurity emergencies, slowing down investigations and breach response.
How Automated Retrospective Detection Works
Reveal(x) 360 combines three powerful and differentiated capabilities to deliver ARD: a curated threat intelligence feed; the Reveal(x) 360 cloud record store, itself a powerful feature that collects and archives in-depth network information; and a cloud analytics engine with the ability to automatically query the cloud record store while continuously analyzing network traffic, using machine learning. The cloud analytics engine with query automation, the record store, and threat intelligence all ingest to a single platform with no limitations or constraints around deployment model, whether cloud, on-premises, or hybrid.
The record store, because it’s hosted in the cloud, provides the cost-efficient elasticity and scalability required to store historical network packets and related telemetry. Meanwhile, the cloud-scale machine learning capabilities built into Reveal(x) 360 are capable of continuously analyzing billions of events to cut through the noise, eliminate false positives, and pinpoint and prioritize relevant threats.
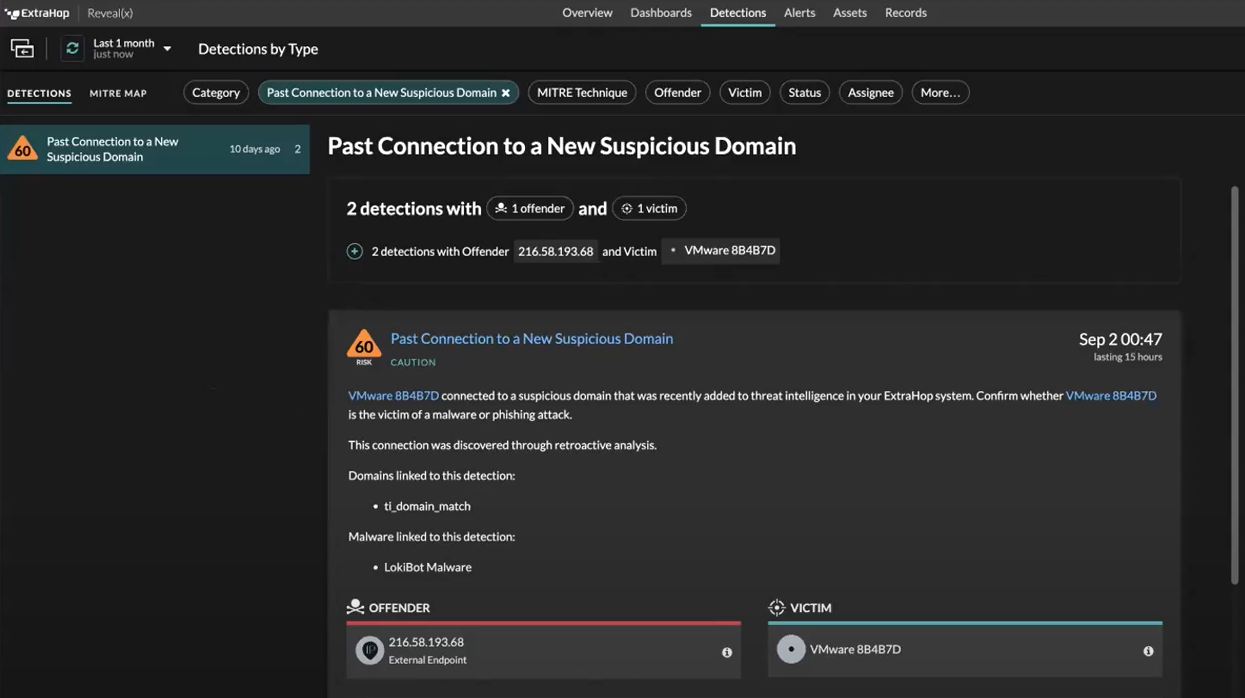
The Origins of ARD
ARD was first released in beta mode as Retrospective Threat Intelligence in version 9.0 of Reveal(x). It evolved from work ExtraHop did to help customers identify whether SUNBURST had infected their environments. (SUNBURST is the malware used in the SolarWinds supply chain attack that attackers were able to deploy months before the attack campaign was discovered.)
While helping customers respond, ExtraHop saw a common need “to go back in time” and search historical records to find out if and when an organization had been compromised. To that end, an ExtraHop threat researcher created a Python script that queried the Reveal(x) API and went through the customer’s record store to look for the associated indicators of compromise (IOCs), including the DNS and IP addresses associated with the attack. Although the script was intended as a temporary fix, customers appreciated the powerful new functionality, which gave ExtraHop its first steps toward a capability to look back into its record store for past malicious network activity and match it with industry-wide security events (which evolved to become Reveal(x) Threat Briefings).
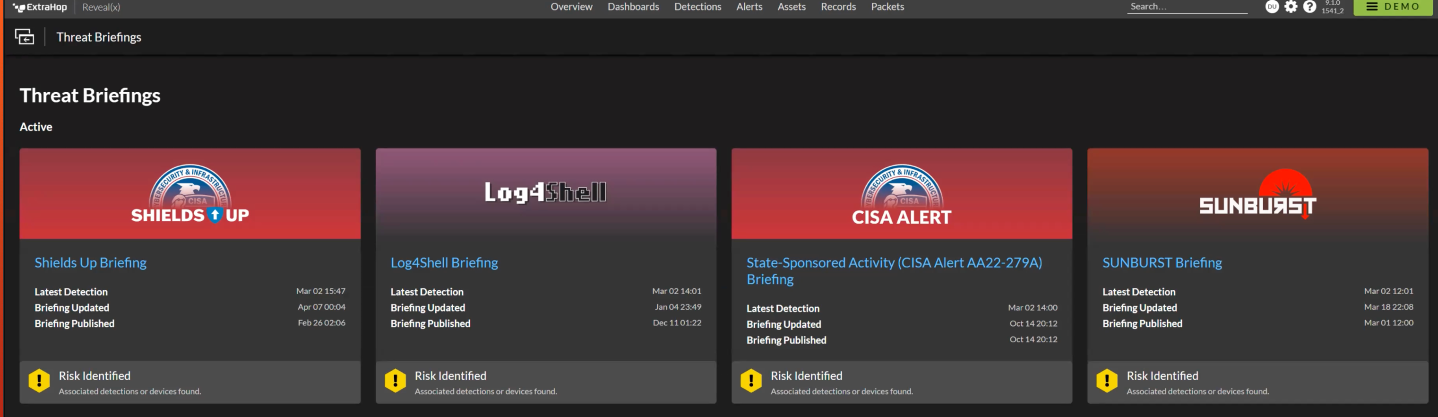
As a comprehensive tool, ARD builds upon threat briefings by introducing automation and correlation in historical network activity by checking for newly reported IOCs that may still be hiding in an organization’s network. ARD adds more automated detection capabilities, focused on historical blindspots, to the threat briefings feature, which spotlights major high-profile threats and attacks.
The Benefits of Automated Retrospective Detection
With ARD, security teams will no longer have to sift through new IOCs, while dealing with the thousands of threat alerts they receive, to understand whether they should manually search for compromises. These cumbersome manual searches often happen during an active emergency, creating situations in which overworked security teams may miss crucial information.
As soon as new threat intelligence is available, ARD allows analysts to know if a new IOC was recently spotted on their organizations’ networks. Reveal(x) 360 with ARD allows security leaders to simplify security operations and reduce costs by automating threat searches on historical network data.
With ARD, security teams can drastically reduce research time and focus instead on their threat response, an especially critical feature for overburdened and understaffed teams ARD eliminates a huge blind spot for customers, enabling them to see more, know more, and stop more threats.
The network is the ultimate source of truth about cyberattacks. Reveal(x) 360 with ARD helps users trust that their networks are secure and free from hidden threats.
