Version 9.2 of Reveal(x) includes several exciting new features, including intrusion detection system sensors and an updated integration with the Palo Alto Networks Cortex XSOAR solution. Here’s a quick overview of what we’re announcing. Customers can check out our release notes for the details on these and other updates in 9.2.
Intrusion Detection System (IDS)
ExtraHop IDS can now identify malicious or unsafe activity based on reputable third-party IDS rulesets. The new IDS sensor generates detections when network traffic matches known IDS signatures of unsafe or malicious behavior, such as malware and command-and-control activity. ExtraHop IDS is available for Reveal(x) and Reveal(x) 360 customers.
ExtraHop IDS represents the next evolution of intrusion detection technology. When combined with Reveal(x) or Reveal(x) 360, ExtraHop IDS provides companies with expanded detection coverage through tens of thousands of reputable network signatures and enhanced detection effectiveness with TLS and Microsoft protocol decryption. The combination of Reveal(x) with ExtraHop IDS also allows customers to deploy and manage their IDS sensors from the same console as their NDR sensors, which helps to streamline detection, investigation and response, and gives security leaders the opportunity to consolidate security technologies without compromising functionality or compliance requirements.
Legacy IDS solutions can be ineffective against today’s threats. They tend to generate too many false positives, lacking capabilities to integrate with other cybersecurity tools, and can cause network performance issues. The new ExtraHop IDS expands the industry-leading NDR capabilities in Reveal(x) with high-fidelity signatures for real-time detection of known malware and exploits.
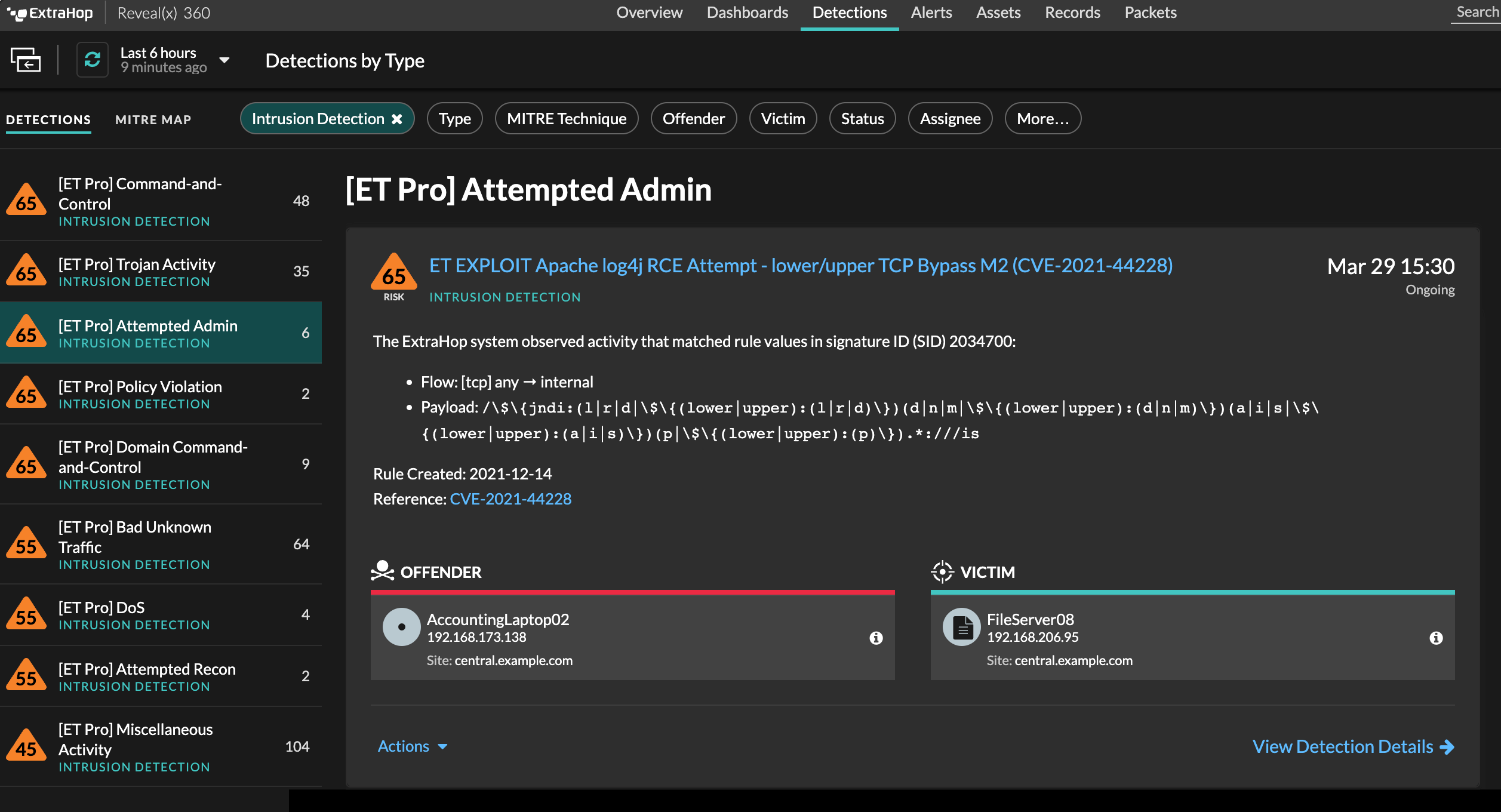
Cortex XSOAR Integration
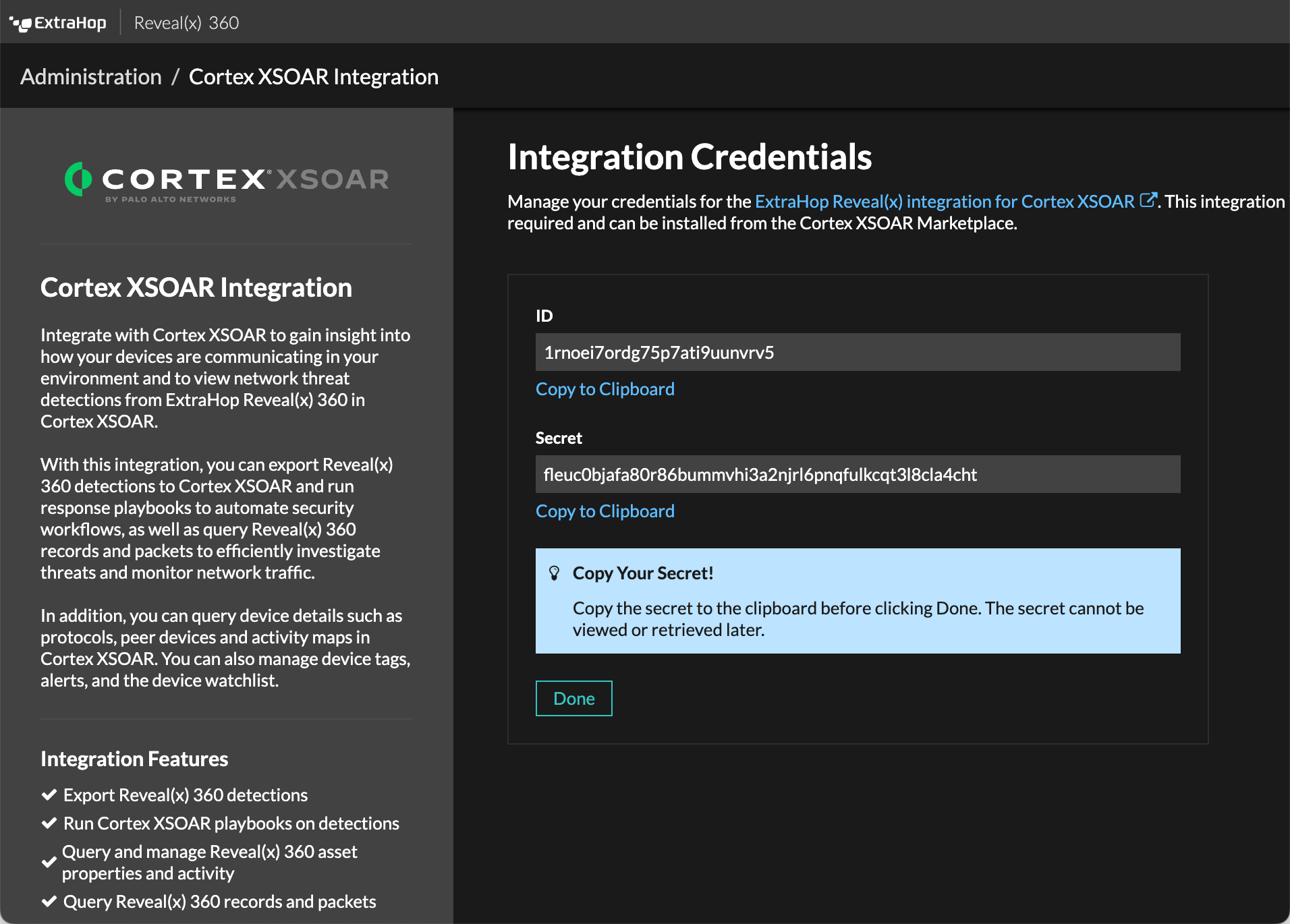
Reveal(x) 360 users can integrate with Cortex XSOAR from Palo Alto Networks to run automated playbooks on detections from the ExtraHop system, query data, and retrieve asset properties and details.
The updated integration with Cortex XSOAR provides users the ability to automatically kick off investigative workflows in response to detections in ExtraHop Reveal(x) 360. Customers of the two products can create a Cortex incident as soon as ExtraHop identifies malicious or non-compliant behavior on their networks, ultimately resulting in streamlined investigations.
After customers use Reveal(x) 360 to search for specific devices and inspect active protocols, records, and packets, they can analyze the results using third-party data and threat intelligence in Cortex to develop incident response and remediation plans. The integration with XSOAR provides simple and secure remediation.
Threat Briefings
We added threat briefings for Microsoft Outlook CVE-2023-23397 (on March 22, 2023) and ESXiArgs Ransomware (on February 15, 2023). Note that threat briefings are cloud-updated and can appear in previous versions of the system.

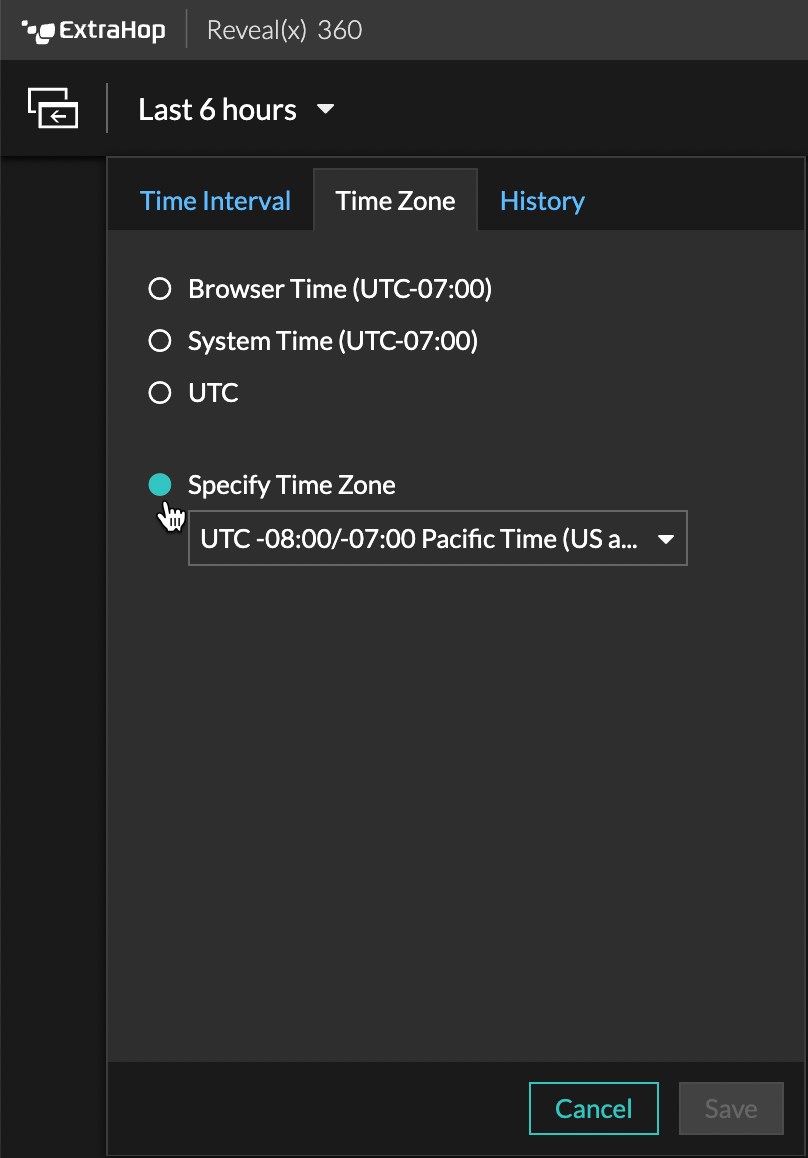
Time Zone Selection
Users can now set their display time zone manually or set their time zone to system time, browser time, or UTC.
Reveal(x) 360
Notifications
Users can now create a system notification rule that sends an email when a firmware upgrade is available for sensors connected to Reveal(x) 360.
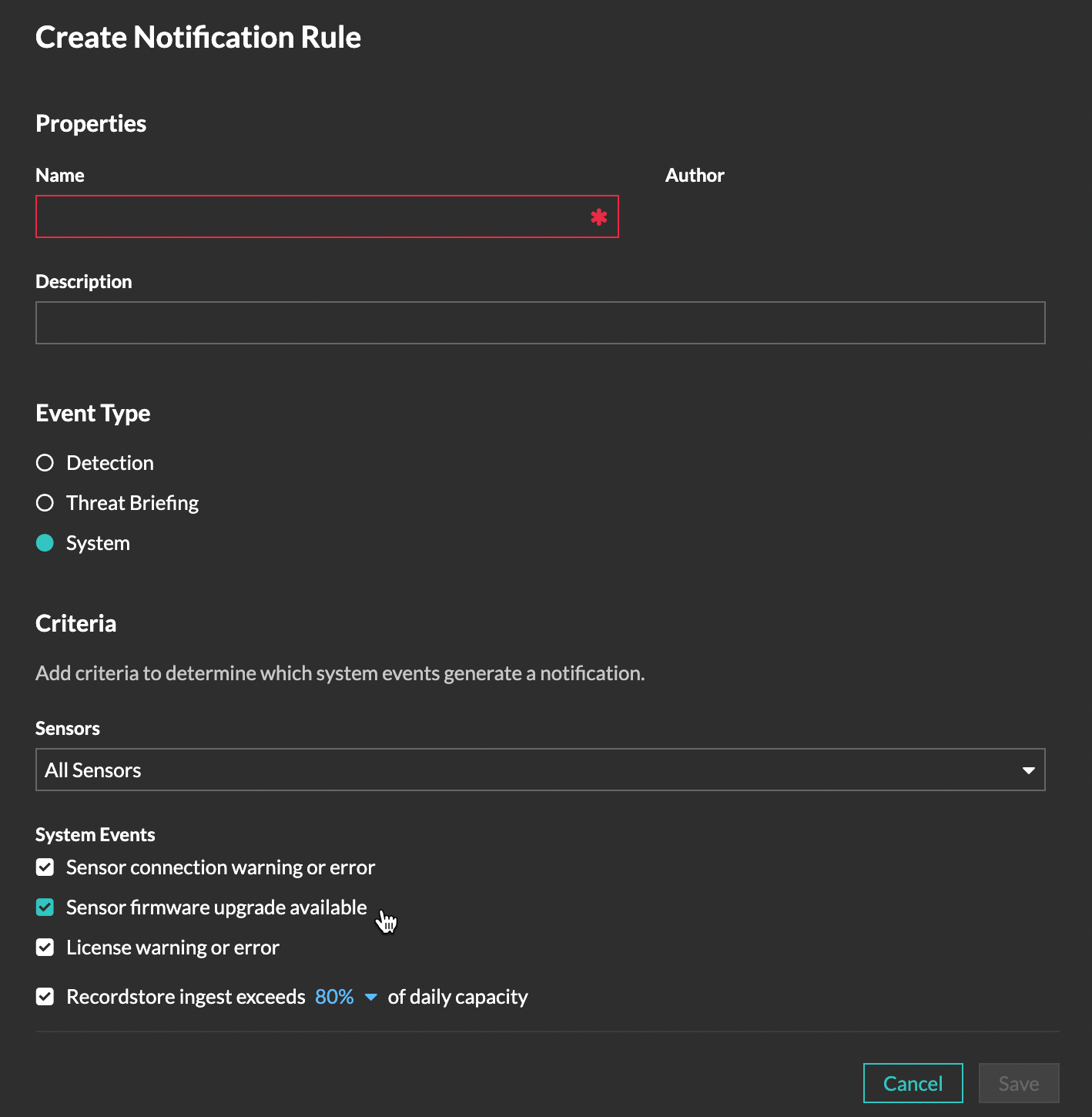
A default system notification rule is now also added to Reveal(x) 360 that includes all system events. The default rule can be disabled or edited.
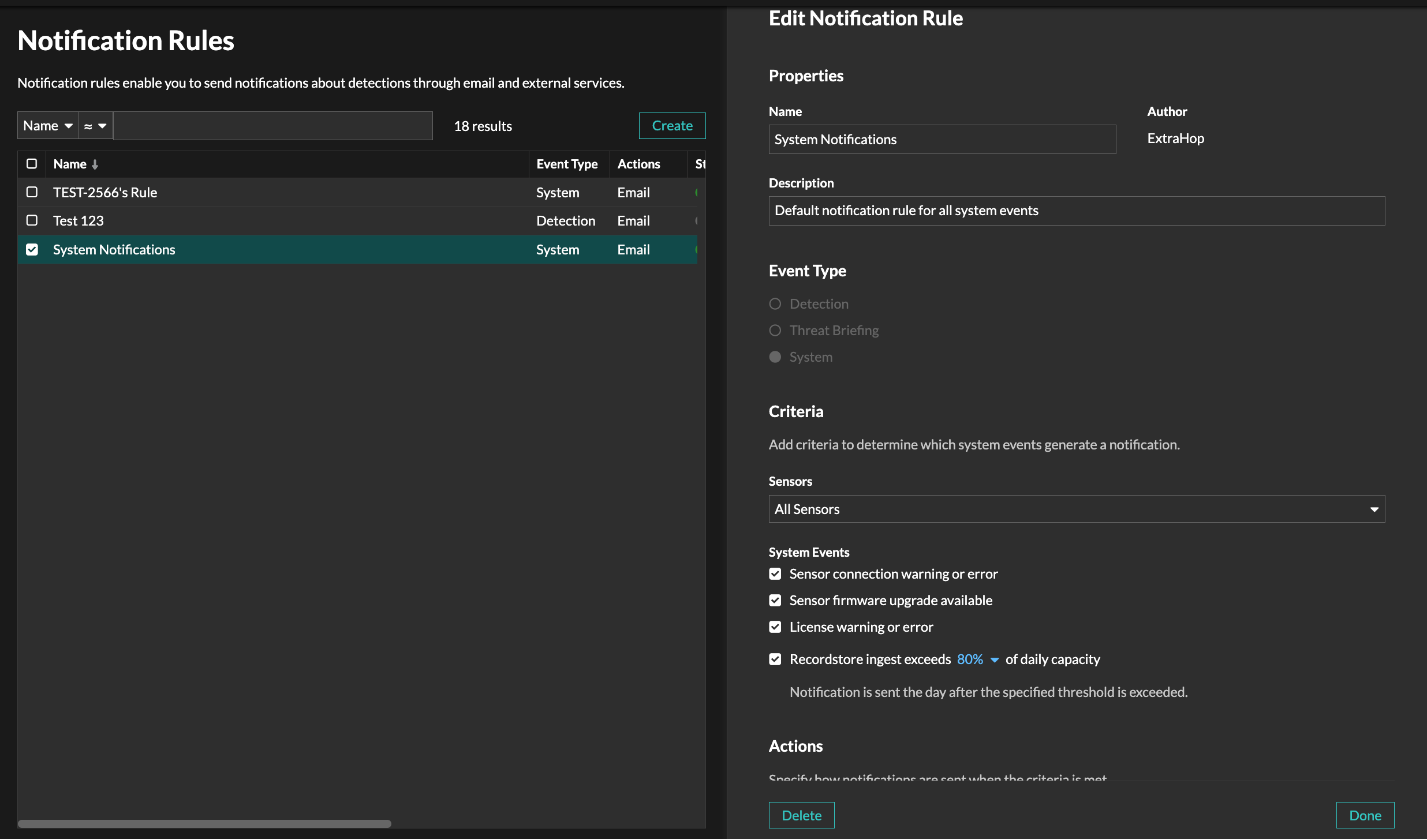
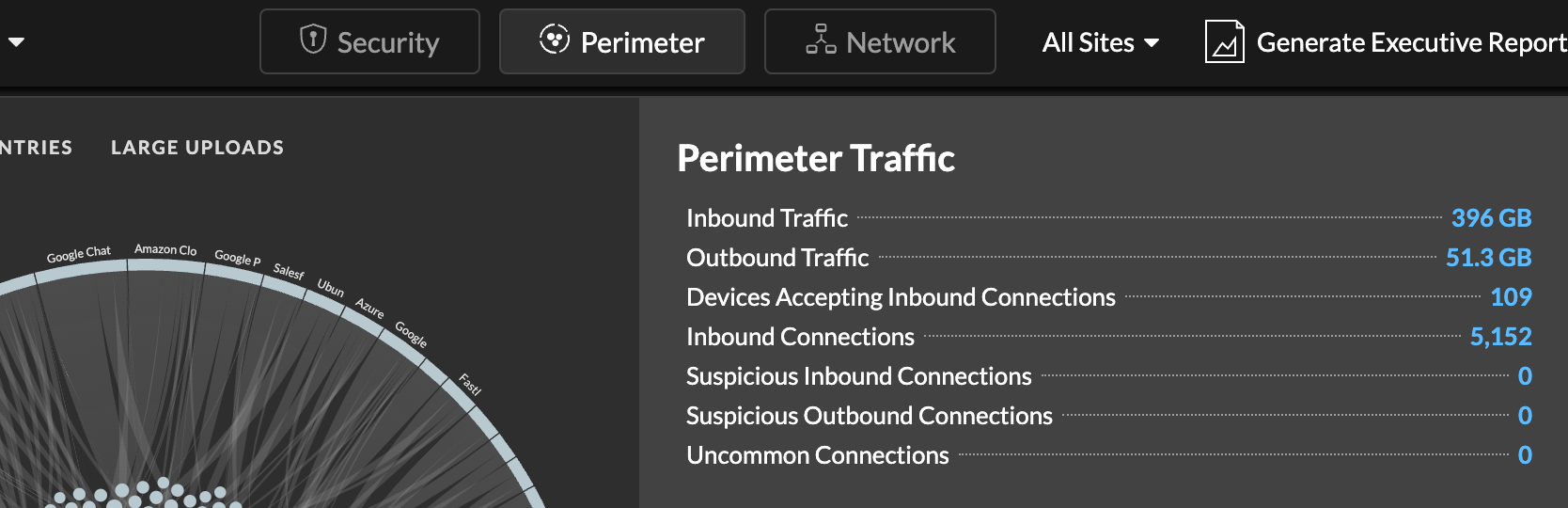
Uncommon Connections
The Perimeter Traffic charts on the Perimeter Overview page now include a count of connections made to IP addresses that are not normally visited or have not been visited in the past.
For Administrators
For environments where compliance requires audits of data sent outside the organization, administrators can now export logs of communications between their sensors and the ExtraHop Machine Learning Service. In addition, the REST API endpoints for running config and license now create jobs that enable administrators to track when changes are applied on a sensor or console.
