It's no secret that speed is one of the most important elements of incident response. ExtraHop Reveal(x) not only detects attacks, it integrates with your existing systems to allow you to streamline or even fully automate your emergency responses, minimizing business disruption and limiting privacy violations.
One of those existing systems that you can now seamlessly integrate with is Palo Alto Networks Cortex XSOAR. Cortex XSOAR is a security orchestration, automation, and response (SOAR) platform focused on incident response that enables you to automate security workflows, manage incidents, and investigate underlying issues.
ExtraHop has partnered with Palo Alto Networks to create a full-featured integration that enables:
- Detection-driven investigations - Real-time creation of Cortex investigations for Reveal(x) detections of malicious or non-compliant behavior on your network.
- Orchestrated response - Playbook-driven enrichment and response powered by thousands of security actions to accelerate automated investigation and remediation.
- War Room commands - Access to real-time security commands against ExtraHop Reveal(x) to search for specific devices, hunt for network peers and active protocols, query records, download packets, and more from within the Cortex war room.
Ticket status in Reveal(x) - Enhanced ticket tracking by linking each of your Cortex investigations back to the corresponding detections in Reveal(x).
ExtraHop Reveal(x) acts as the always-on eyes and ears of the security operations center (SOC) and provides high-quality detections which, in real time, can create Cortex XSOAR incidents and kick off automated workflows.
Get an up-to-date list of available bundles
How Reveal(x) and Cortex XSOAR Work Together
Create Cortex Incidents in Real Time
The integration includes an ExtraHop trigger that, for every ExtraHop detection, automatically creates a corresponding Cortex incident in real time via the Cortex REST API. These incidents can kick off automated investigation and remediation workflows including ticket tracking, guided investigation, blocking/locking, and more.
Let's walk through an example where the unusual network behavior that ExtraHop detected was a CVE-2019-0708 (BlueKeep) RDP exploitation attempt. Here's the ExtraHop detection card that shows a detailed description of the attack, the victim and offender device, a timeline of related detections, mitigation options, CVE references, and links to the associated transaction records and network packets:
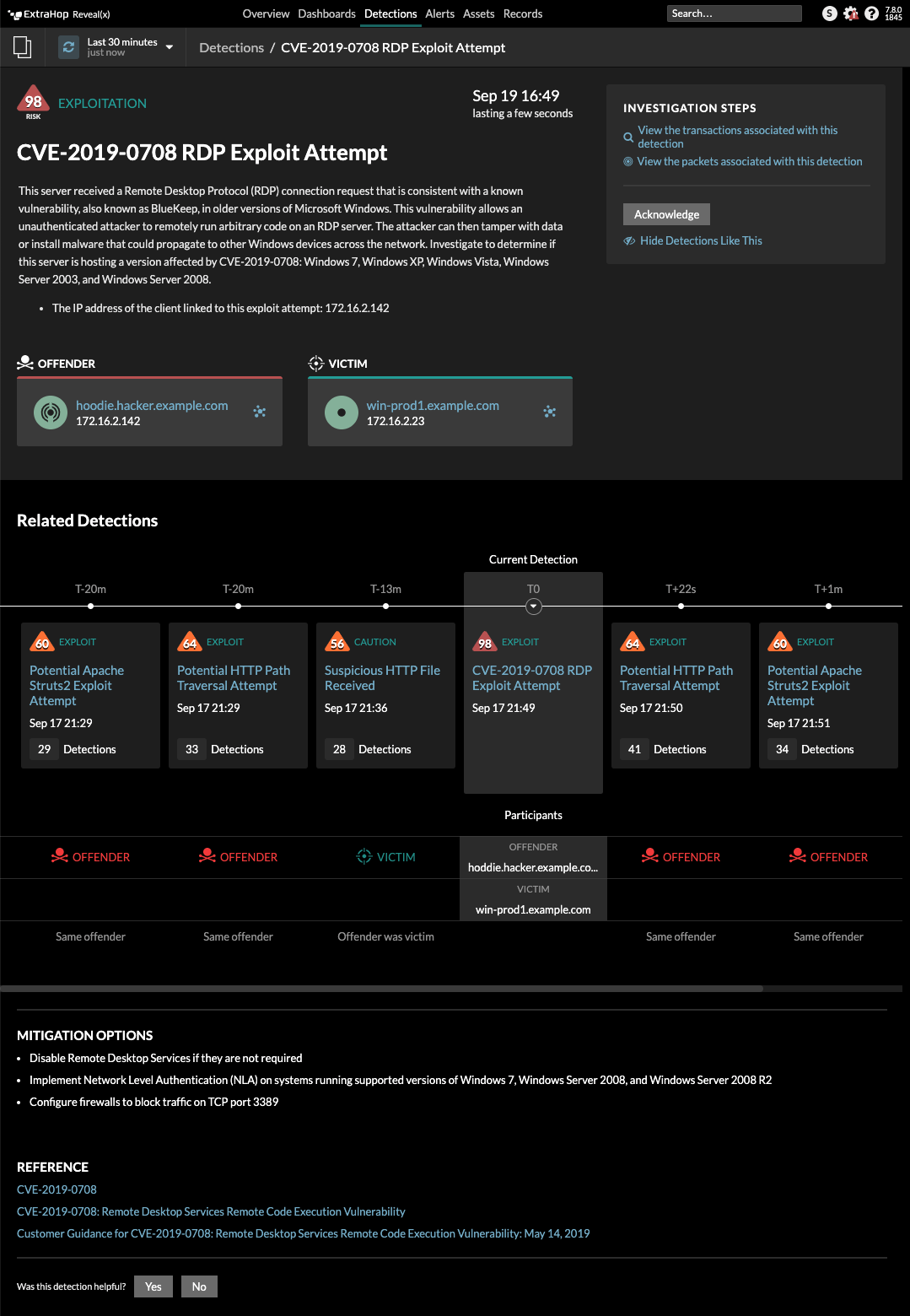
Figure 1. ExtraHop Detection card for CVE-2019-0708 (BlueKeep) RDP Exploit Attempt
The trigger automatically creates a corresponding Cortex incident with all of the ExtraHop detection details. This information helps analysts evaluating the detection to understand the severity of the event. Too often, analysts' time is wasted by alerts with low context—Reveal(x) gathers contextual details so that people don't have to spend time gathering that information for themselves.
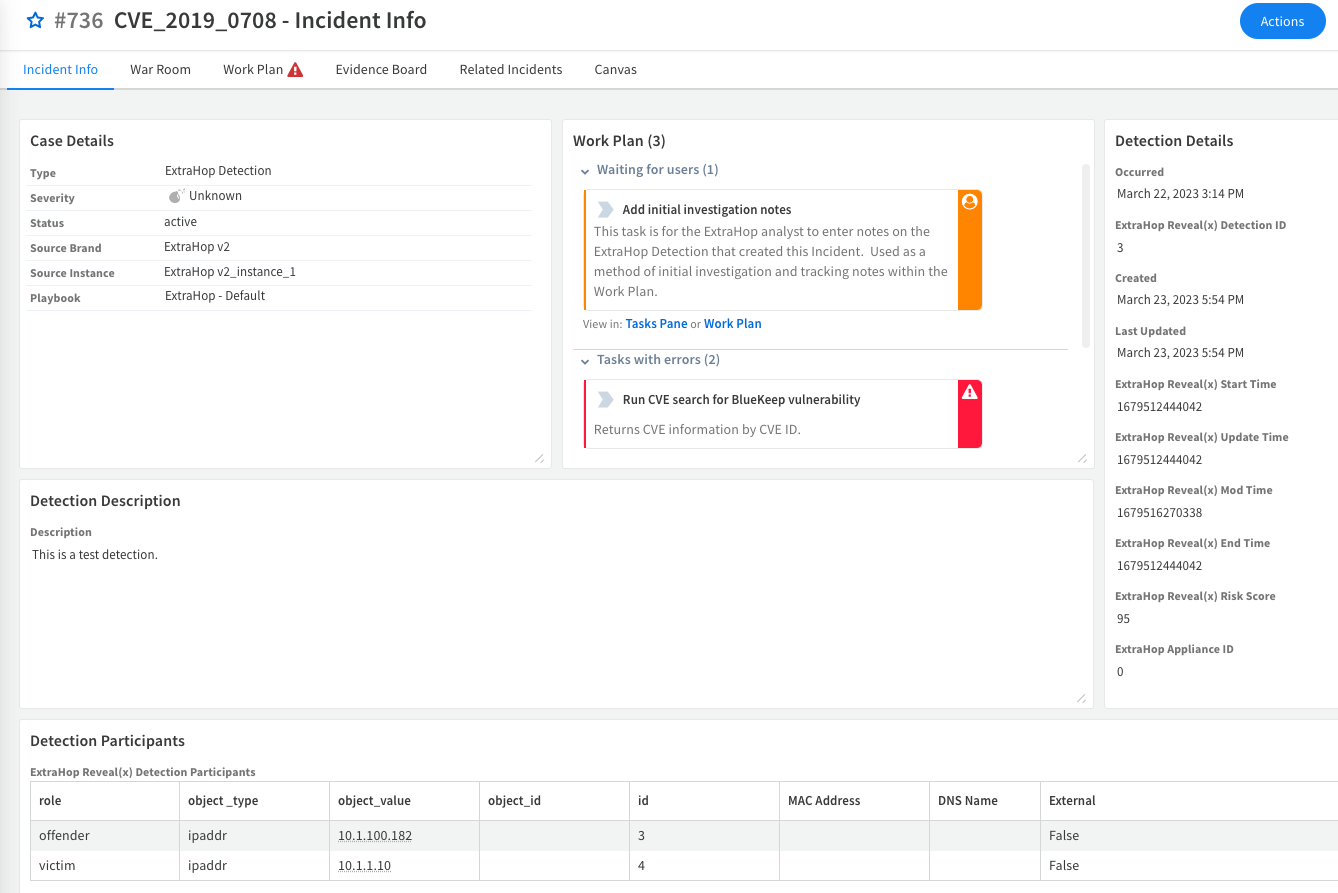
Figure 2. Cortex incident summary for CVE-2019-0708 (BlueKeep) RDP Exploit Attempt
Playbook-Driven Enrichment and Response
Once an incident of type ExtraHop Detection is created in Cortex, the ExtraHop - Default playbook automatically assigns an ExtraHop analyst to the incident, sets up ticket tracking, and runs any detection playbooks associated with the incoming incident.
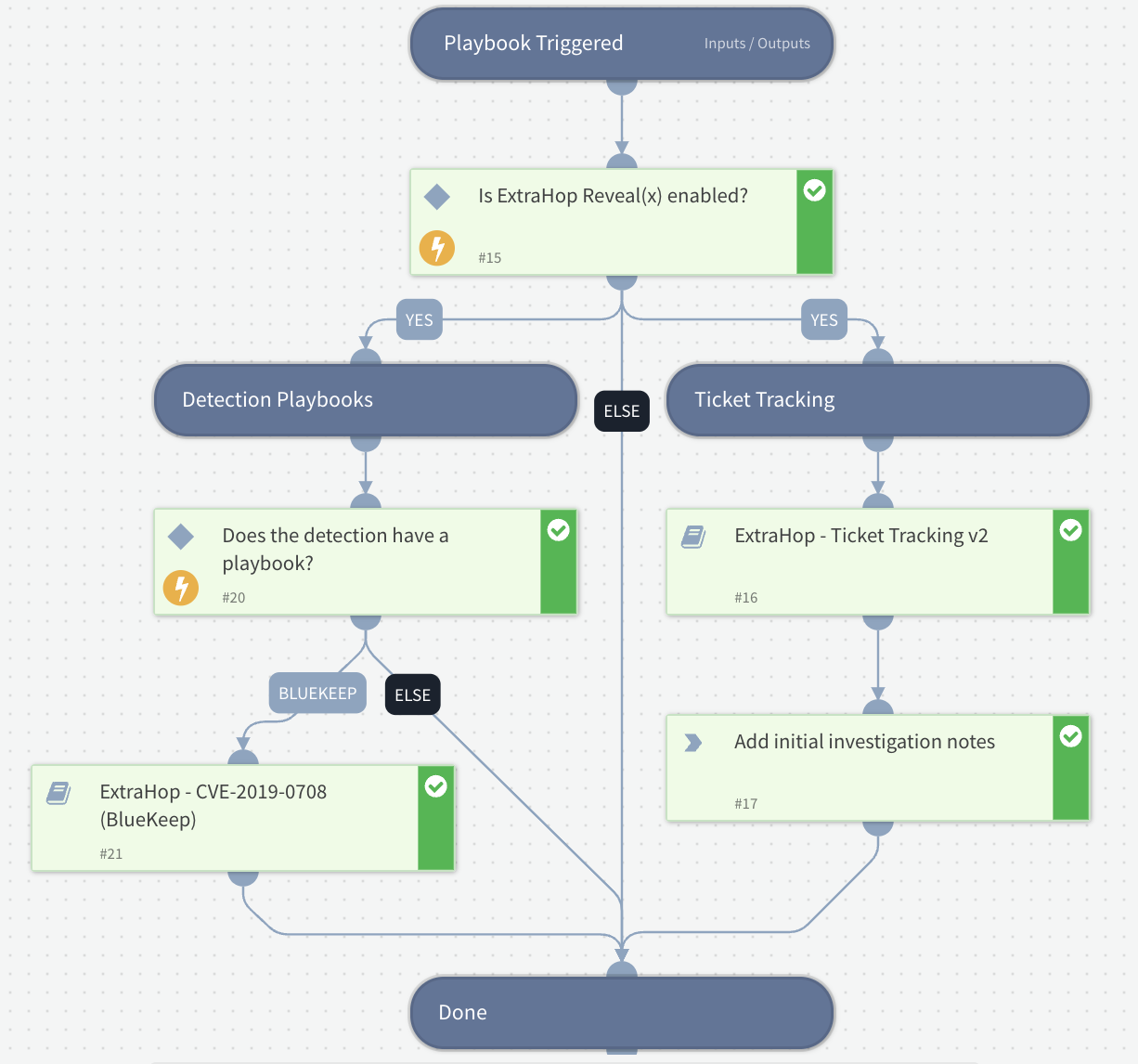
Figure 3. ExtraHop - Default playbook to setup ticket tracking and run specific detection playbooks
In this case, the CVE-2019-0708 (BlueKeep) RDP exploitation attempt detection does have a specific detection playbook which automatically gathers detailed investigation information from Reveal(x) and orchestrates a remediation workflow.
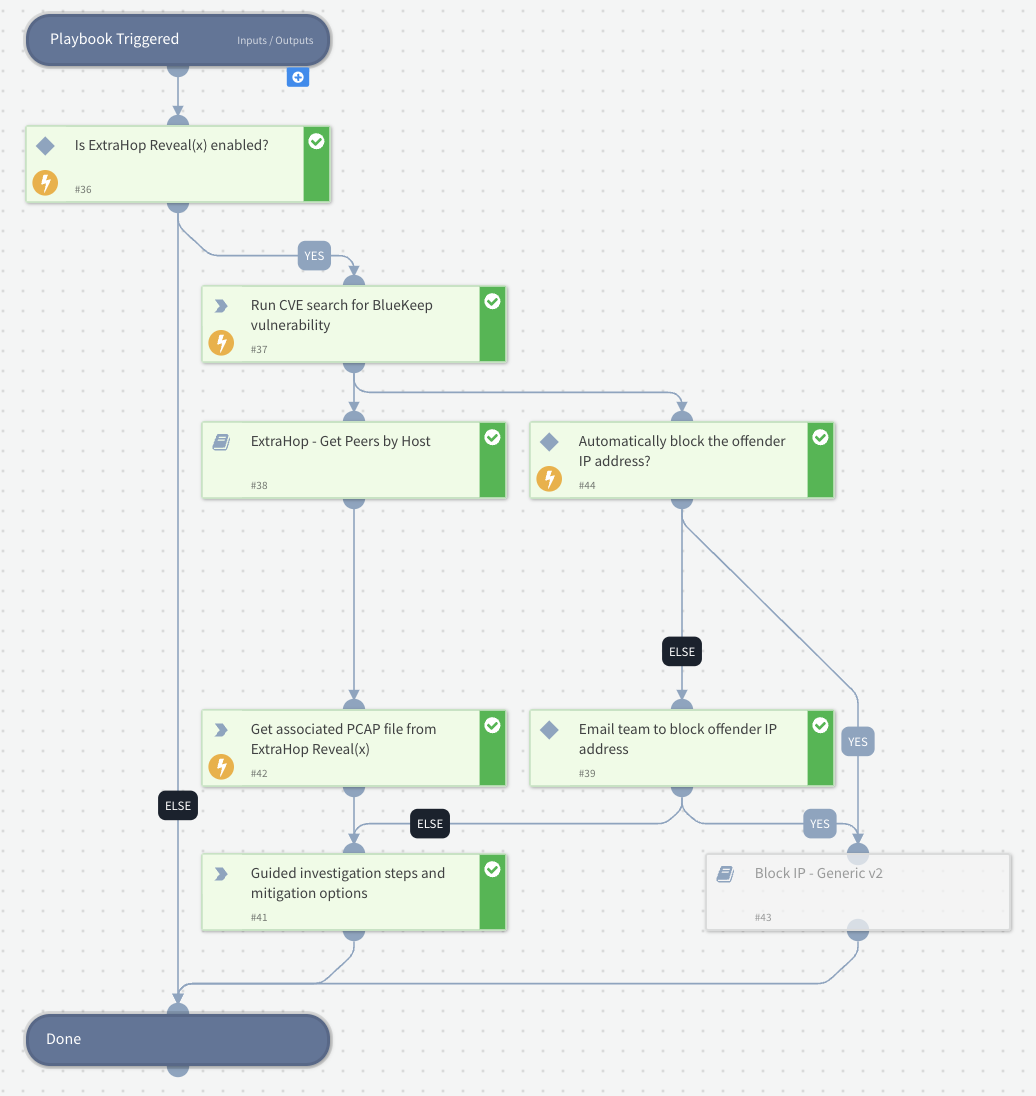
Figure 4. ExtraHop - CVE-2019-0708 (BlueKeep) playbook for automated investigation and response
This playbook starts off by running a CVE search and returns the following:
"A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka 'Remote Desktop Services Remote Code Execution Vulnerability'. This vulnerability allows an unauthenticated attacker to remotely run arbitrary code on an RDP server. The attacker can then tamper with data or install malware that could propagate to other Windows devices across the network."
The playbook continues to run a series of tasks to both automate the investigation of the exploitation attempt and also reach out to your ExtraHop analysts to determine if an automated IP blocking action is appropriate. The automated investigation completes the following tasks:
- Gathers device activity - Runs another ExtraHop contributed playbook to hunt for details on the offender device in your Reveal(x) including all of the network peers and protocols communicated during the exact time of the incident as well as provide a direct link to an ExtraHop Live Activity Map to visualize the network communications at the time of the attack.
- Queries transaction records - Retrieves the exact transaction records associated with the attack from Reveal(x) and displays them in a human-readable table in the War Room.
- Collects PCAP file - Searches Reveal(x) for the exact packets associated with the attack and downloads a PCAP file to the War Room.
- Orchestrates remediation - Reaches out for an ExtraHop analyst approval to automatically block the offender IP address using the supported IP blocking integrations that you have enabled.
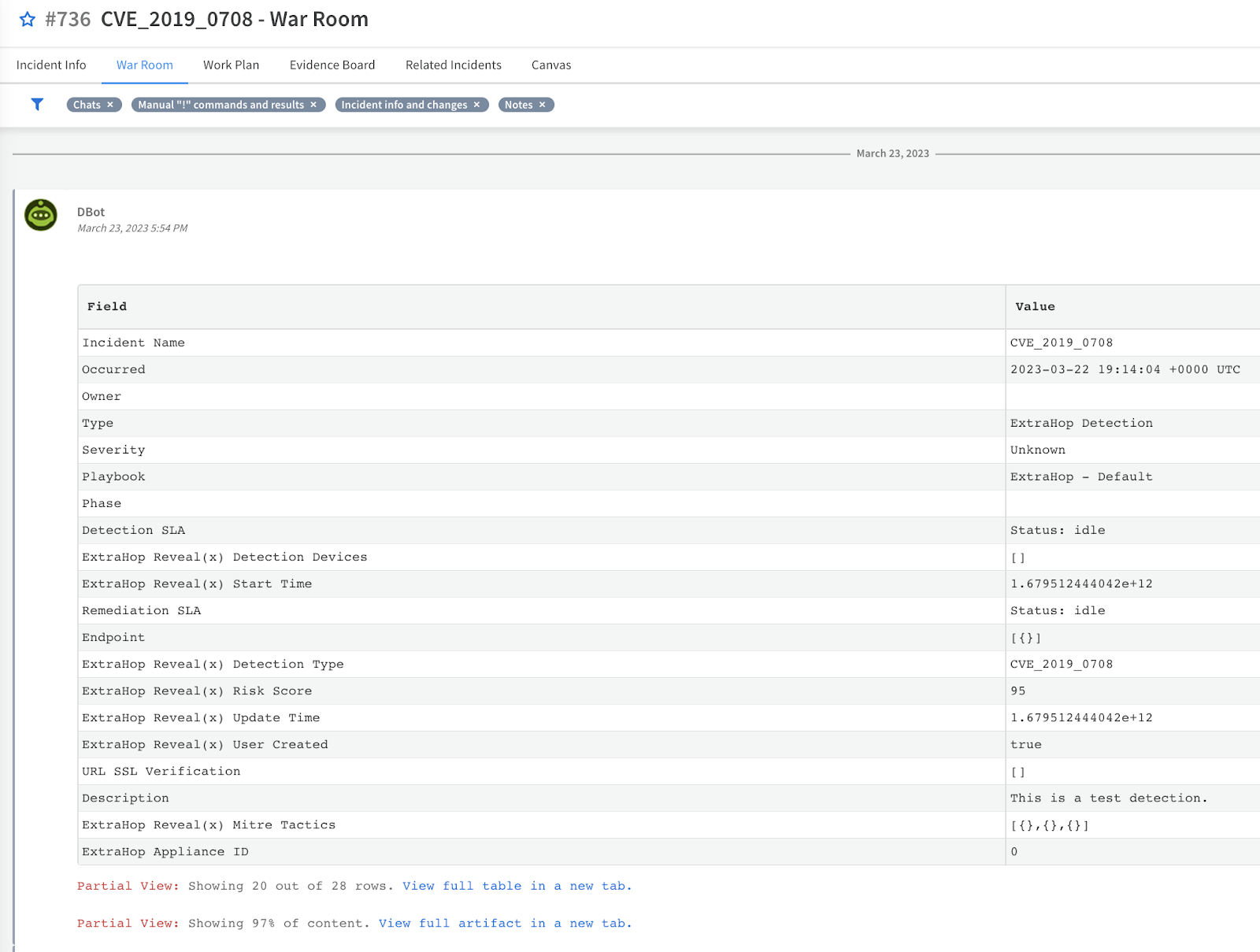
Figure 5. Cortex War Room showing the results of the automated Reveal(x) investigation
As a result of the playbook, within seconds of the incident being created your SOC analyst already has all of the detection information properly organized and formatted to make an informed decision about the appropriate response to take against the exploitation attempt.
Interactive Investigation in the Virtual War Room
The integration brings the power of Reveal(x) to a Cortex War Room with the ability to quickly and easily search for devices matching specific criteria, hunt for network peers and active protocols, query records, download packets, view activity maps, tag devices, and more all from within the interactive command-line in Cortex War Rooms.
Reveal(x) automatically discovers and classifies all devices communicating in your network and then makes those attributes available for search in the Cortex War Room. This enables analysts to search for all file servers running the Windows operating system, for example. This search capability will also discover unmanaged and rogue devices that are not accounted for in a CMDB.
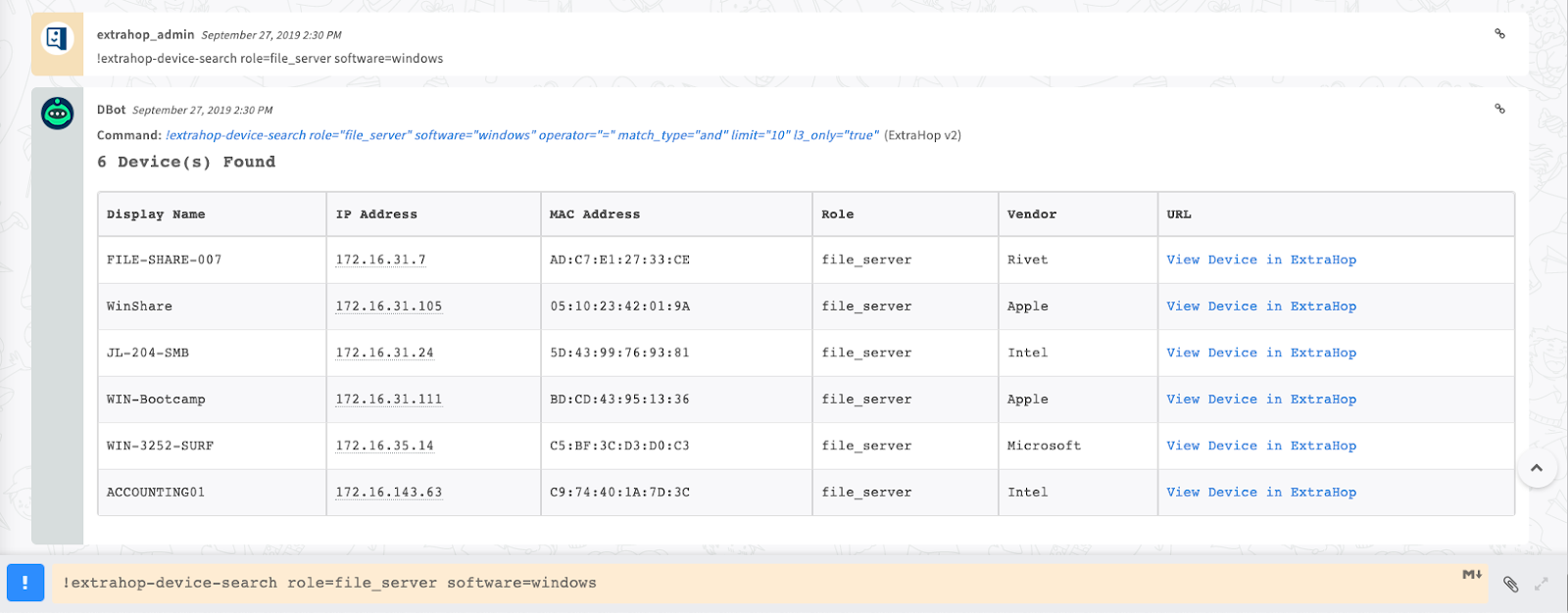
Figure 6. Reveal(x) command to quickly search for all Windows file servers on your network
Enhanced Ticked Tracking for Detections
The integration also links each of your Cortex incidents back to the corresponding detections in Reveal(x) so that your analysts can easily see the assignee and status of the incident from within the Reveal(x) UI.
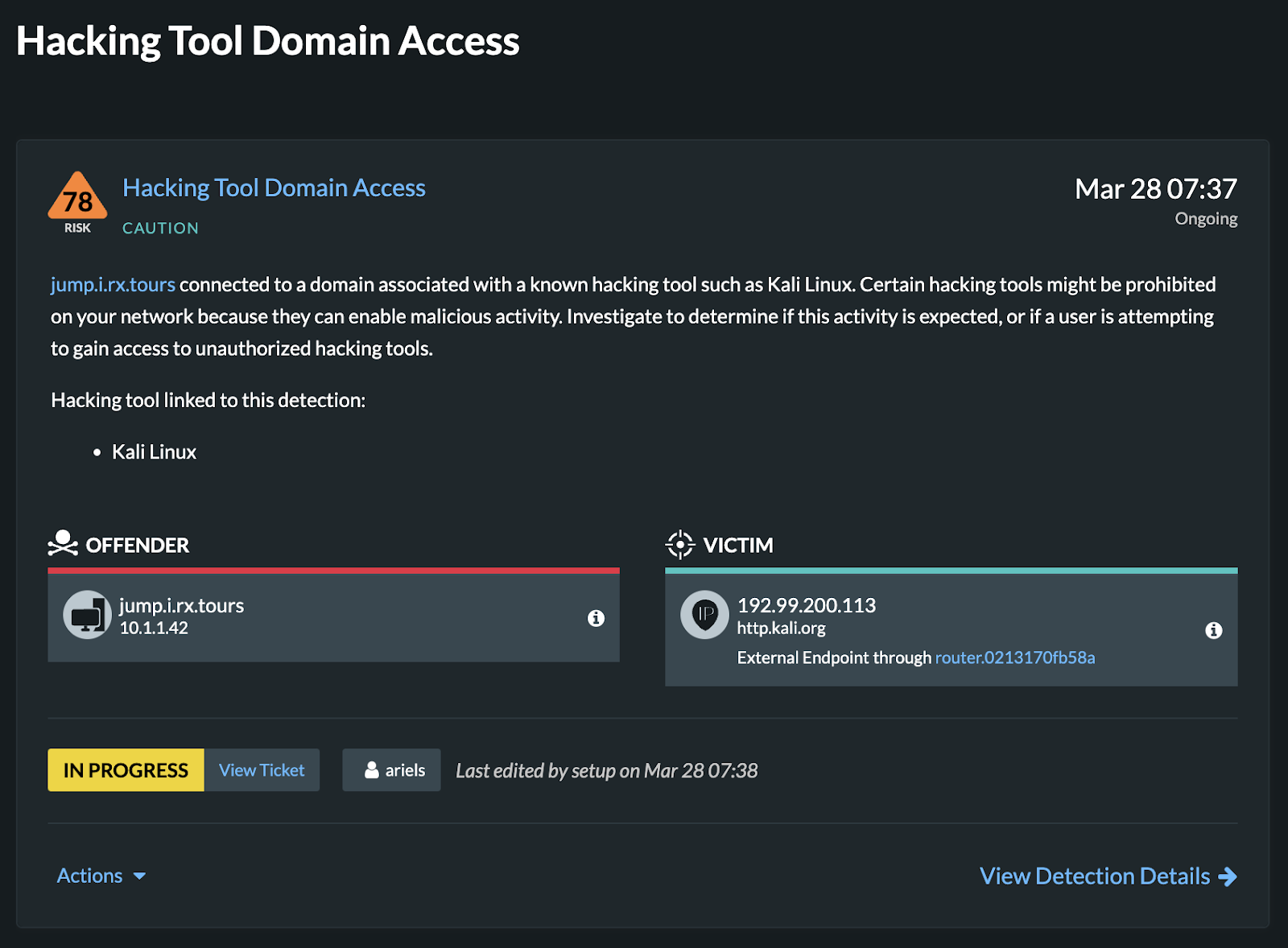
Figure 7. ExtraHop Detections with ticket status updates from Cortex
Network detection and response (NDR) products are a vital layer of defense in detecting suspicious activity at every stage of the attack lifecycle. By integrating the Reveal(x) NDR with Cortex XSOAR, an organization can dramatically speed up the response to newly detected threats with appropriate levels of human interaction.
