More and more organizations are moving forward with a zero trust architecture, especially following the Department of Defense’s (DoD) announcement that it plans to meet certain zero trust goals by September 2024. The DoD’s zero trust strategy will accelerate zero trust adoption as thousands of contractors that work with the agency implement their own zero trust security measures.
The DoD views zero trust as the security strategy and architecture that will improve its cyber resiliency and better protect its networks from cyberattacks, even as it continues to expand remote work, modernize its technology infrastructure, accelerate cloud adoption, and provide greater numbers of external partners with access to its systems, networks, and data.
Private-sector enterprises, especially those in highly-regulated industries, have also made significant progress in implementing zero trust architectures and deploying technologies like security service edge (SSE) so they can leverage cloud environments and implement work-from-anywhere in a secure manner. But even SSE has its limitations. For instance, the NIST zero trust architecture requires the ability to inspect all traffic that traverses a network, but SSE can impede security and IT teams’ visibility into some network traffic. Moreover, departmental silos that each integrate independent security solutions can isolate environments, and weaken security and communication across departments.
How Network Detection and Response (NDR) Supplements SSE to Support Zero Trust
SSE providers create secure tunnels for data to traverse, but they accomplish this by blocking access to the data flowing through those tunnels. This means network visibility tools like NDR and NAV can’t inspect this traffic, which leaves security and IT teams with a blind spot. To maintain zero trust, they need visibility into all network traffic, across each security domain, including cloud, hybrid, and on-premises environments. But with SSE, they often have to create workarounds to get this visibility, like using less reliable, recreated models of the traffic or deploying heavy-handed endpoint solutions that may degrade network performance and user experience. Or worse, they entirely forgo visibility into this traffic.
These workarounds can lead to all sorts of downstream problems. Poor network performance and user experience can have negative effects on SLAs and productivity. Gaps in an organization’s zero trust architecture due to lack of visibility can lead to hefty fines for non-compliance in highly regulated industries. And worse still, threats can go undetected in encrypted traffic that’s otherwise authenticated, giving attackers longer dwell times to orchestrate more sophisticated campaigns, like ransomware.
ExtraHop Zero Trust Extension for Netskope
Many of our customers, especially those in financial services, healthcare, business services, and retail, have expressed their concerns about these threats. We listened. ExtraHop is working closely with Netskope to bring unprecedented visibility to remote and distributed environments by integrating Netskope Intelligent SSE—twice recognized as a GartnerⓇ Magic Quadrant™ Leader for SSE—with ExtraHop RevealX—named a Leader in The Forrester WaveTM Network Analysis and Visibility, Q2 2023. The Netskope Cloud TAP is currently available to existing customers via an early access program for non-production environments.
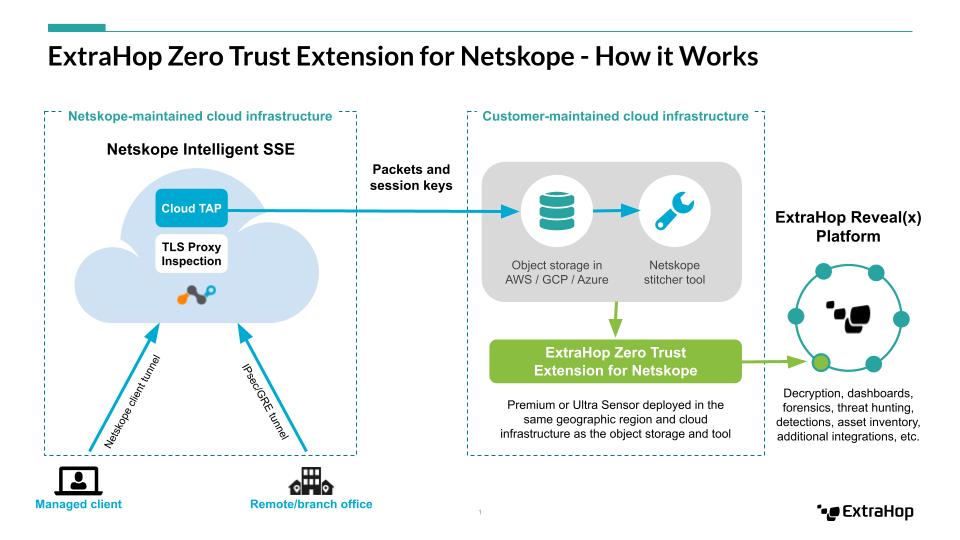
So how does it work? Netskope Intelligent SSE streams encrypted traffic packets and session keys to an ExtraHop Zero Trust Extension sensor and analyzes the data for security and performance anomalies. Reveal(x) natively decrypts the original network packets, leveraging over 70 different protocols, to provide complete visibility into virtually any traffic source. Automatic discovery and classification of devices communicating on the network enables security teams to fully map the attack surface, thereby eliminating blind spots. Continuous, automated 90-day lookback helps identify signatures of new CVEs and zero-day attacks, while signature- and behavior-based machine learning models enable multi-layer detection of malicious activity with high confidence.
The improved visibility provided by the integration will allow organizations to close gaps in their zero trust security posture and will give them broader MITRE ATT&CK detection coverage, both of which help to reduce the risk of a breach and compliance fines. The integration also allows security and IT teams to leverage their existing SSE and NDR investments to achieve greater zero trust maturity by increasing the number of business-critical systems with continuous, forensic-level monitoring and reducing the time it takes to produce quality, audit-ready compliance reports, among numerous other benefits.
With the ExtraHop Zero Trust Extension for Netskope, organizations will be able to maintain zero trust access to their networks without compromising security or performance for cloud apps and remote teams. Teams will gain real-time visibility into network traffic crossing the SSE, along with the granular, packet-level data needed to assess and resolve issues at the speed of business. That’s a rare win-win for these teams and a big loss for attackers.
Does your organization use SSE? What questions do you have about this new integration between Reveal(x) and Netskope Intelligent SSE? Join the conversation on the ExtraHop customer community.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
