Scale Your Cloud with Confidence
Cloud policies, or the guidelines under which organizations operate in the cloud, are carefully curated to help your business take advantage of the speed and flexibility of the cloud without misconfigurations or oversights... but rules only work if everyone understands them and actively pursues compliance. According to the SANS Institute's 2019 study, 42 percent of enterprises reported security breaches due to cloud service or resource misconfigurations.
If your development team is moving fast to spin up new cloud instances and scale the business, costly and time-consuming operational management can seem like an afterthought. ExtraHop Reveal(x) 360 provides the cloud-first approach to cybersecurity that allows security teams to scale their organizations without also scaling risk.
Complete Visibility
Automatically discover and classify each cloud instance your team spins up, and flag all misconfigurations, insecure APIs, and unauthorized access. At the same time, discover and track all rogue instances and decrypt SSL/TLS traffic in real time to spot otherwise undetectable malicious behavior.
Real-Time Detection
Instantly detect anomalous behavior and malicious activity within and across all workloads, and improve your prioritization and risk management by automatically correlating those detections against your critical assets. Reveal(x) 360 uses cloud-based machine learning with over 5,000 wire data features and 70+ protocols to provide the highest fidelity detections so you can focus on what matters most.
Intelligent Response
Take a nuanced approach to incident response with Reveal(x) 360. Pivot from detection to forensic evidence with investigative workflows you can complete in 3 or fewer clicks. Leverage integrations with AWS, Azure, and Google Cloud tools, as well as ServiceNow, Check Point, CrowdStrike, and Splunk Phantom to speed up mitigation and response automations.

[ExtraHop] really works natively with the packet level inspection of vulnerability scans. ...It allows us to remediate risk [and] gives us the ability to identify vulnerabilities in environments in real time.
Dan McDaniel
Chief Architect & Information Security Officer,
Wizards of the Coast
NDR and the Cloud SOC Visibility Triad
The SOC Visibility Triad combines data from endpoint detection and response (EDR) and security information and event management (SIEM) tools with network data to support stronger enterprise security in the cloud. But until recently, the missing piece of the triad was easy access to data from network traffic. Capturing network data used to require deploying agents, a complex process that was difficult to scale.
With the introduction of packet mirroring features in the cloud, SOCs can finally take advantage of network data to provide visibility across complex attack surfaces, detect threats in real time, and enable rapid incident response.
Network detection and response provides observed ground truth with context that can't be turned off or evaded by savvy attackers, unlike log and agent-based tools. Because of this resilience, cloud-native NDR is the best approach to helping organizations uphold their side of the shared responsibility model of cloud security.
Ready to Learn How It Works?
Explore Reveal(x) 360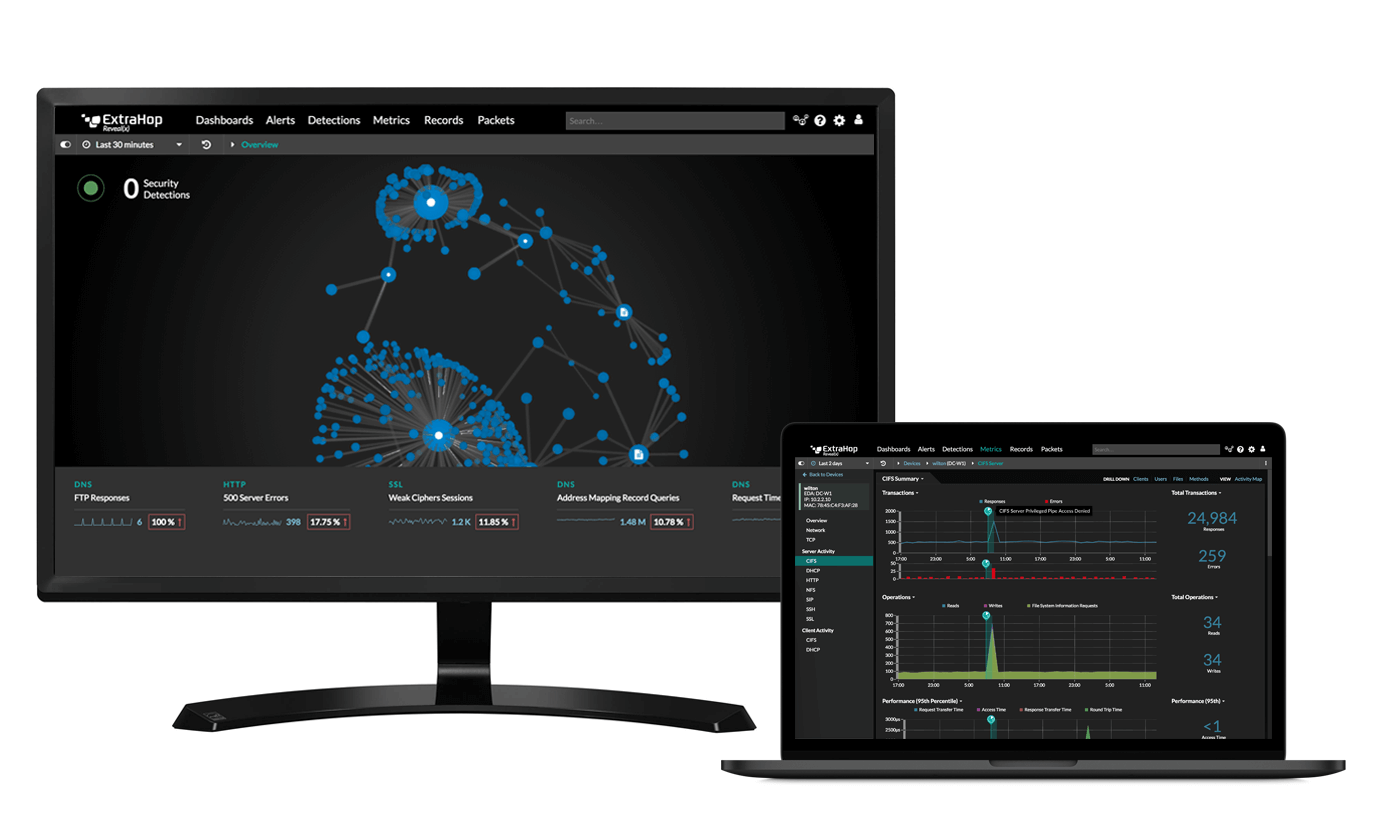
Start the Demo
Stop data exfiltration, insider threats, and more with the full product demo.
Start Demo