Cloud-Native Security
Shared Responsibility Model Assurance
Ensure Security of Your Public Cloud Deployments
What Is Your Responsibility for Cloud Security?
Taking advantage of the speed, scale, and elasticity of infrastructure-as-a-service (IaaS) cloud platforms is a double-edged sword for enterprises. Under the Shared Responsibility Model, cloud service providers (CSPs) manage and secure the hardware and software that comprise the infrastructure of the cloud, leading to lower capital overhead and increased flexibility for cloud customers. However, those same customers must typically take responsibility or securing everything above the hypervisor, including business and customer data, applications, the operating system, and identity access and management.
CSPs, with intimate knowledge of their hyperscale infrastructure platforms, deep security budgets, and rosters of talent, do an excellent job of securing their side of the Shared Responsibility Model. Many cloud customers struggle to uphold their half in fact, Gartner predicts 95% of the cloud security failures through 2022 will have occurred on the customer side of the Shared Responsibility Model and concerns about security can slow or stall cloud migration. It's time for a cloud-native approach to enterprise security.
ExtraHop Reveal(x) 360 is a SaaS-based network detection and response (NDR) product that helps organizations secure their investment in the cloud and uphold their side of the Shared Responsibility Model. Reveal(x) 360 provides your security, IT, and development teams with the complete visibility, real-time threat detection, and intelligent response capabilities across hybrid and multicloud environments they need to move safely at the speed and scale the enterprise demands.
Complete Visibility
Automatically discover and classify every asset in your cloud infrastructure, including rogue instances. Reveal(x) 360 provides deep, continuous visibility including into SSL/TLS encrypted traffic and situational intelligence across hybrid, multicloud, IoT, and remote work environments from a single management pane, accessible from anywhere.
Real-Time Detection
Harden your attack surface with immediate detection of anomalous behaviors and malicious activities that indicate unauthorized access and attempts to exploit misconfigurations and insecure APIs. Reveal(x) 360 uses cloud-based machine learning, leveraging more than 5,000 wire data features and 70+ protocols to accurately identify threats whenever they occur within or across cloud workloads.
Intelligent Response
Take a nuanced approach to incident response with Reveal(x) 360. Guided investigative workflows enable you to pivot from detection to forensic evidence in 3 or fewer clicks. Integrations with a wide range of CSP and vendor tools, including next-gen firewalls (NGFW), endpoint detection and response (EDR), and security orchestration, automation, and response (SOAR), as well as built-in Reveal(x) 360 capabilities, help you respond to incidents as soon as they happen.

[ExtraHop] really works natively with the packet level inspection of vulnerability scans. ...It allows us to remediate risk [and] gives us the ability to identify vulnerabilities in environments in real time.
Dan McDaniel
Chief Architect & Information Security Officer,
Wizards of the Coast
NDR and the Cloud SOC Visibility Triad
The SOC Visibility Triad combines data from endpoint detection and response (EDR) and security information and event management (SIEM) tools with network data to support stronger enterprise security in the cloud. But until recently, the missing piece of the triad was easy access to data from network traffic. Capturing network data used to require deploying agents, a complex process that was difficult to scale.
With the introduction of packet mirroring features in the cloud, SOCs can finally take advantage of network data to provide visibility across complex attack surfaces, detect threats in real time, and enable rapid incident response.
Network detection and response provides observed ground truth with context that can't be turned off or evaded by savvy attackers, unlike log and agent-based tools. Because of this resilience, cloud-native NDR is the best approach to helping organizations uphold their side of the shared responsibility model of cloud security.
Ready to Learn How It Works?
Explore Reveal(x) 360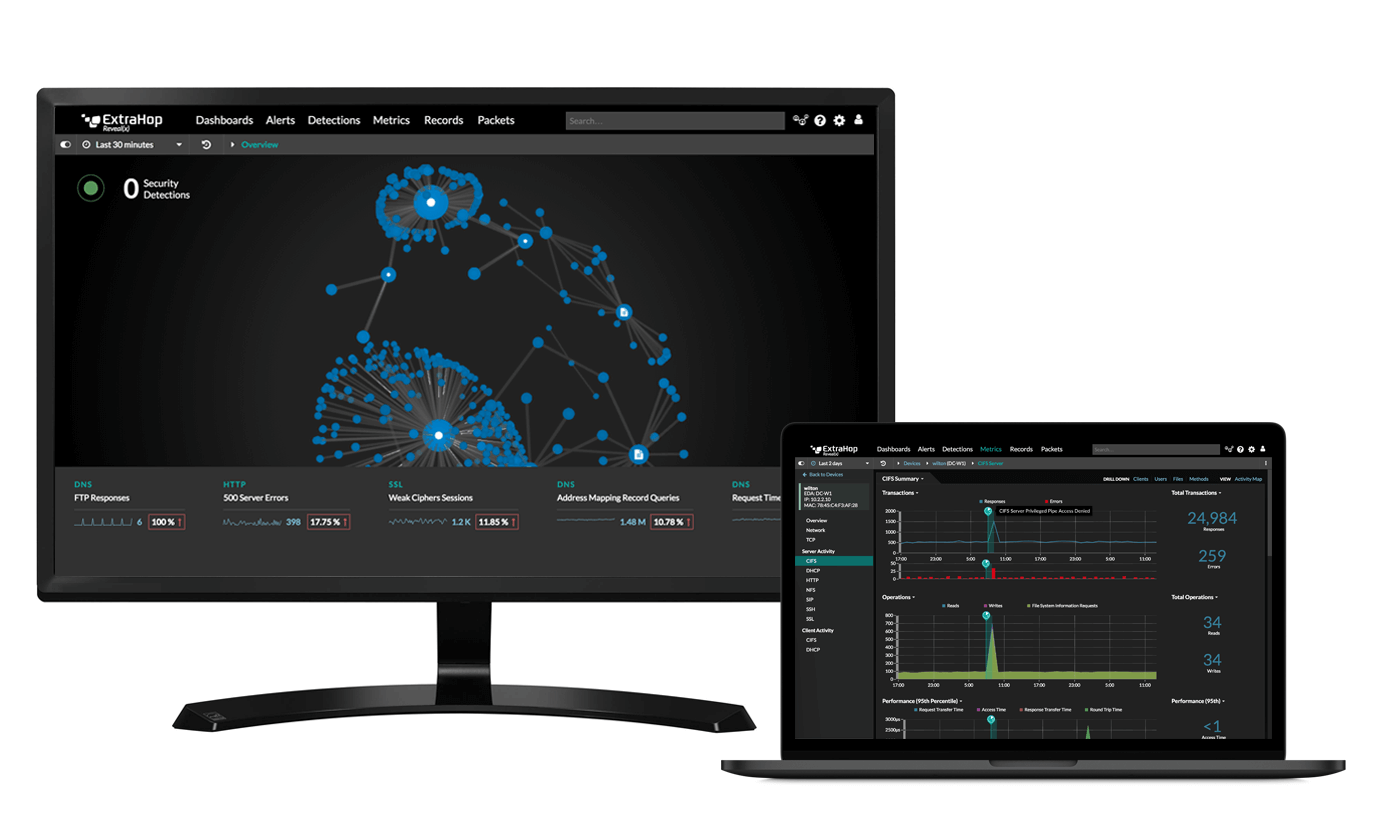
Start the Demo
Stop data exfiltration, insider threats, and more with the full product demo.
Start Demo