One of the many benefits of cloud computing is the ability to offload management and administration tasks to your cloud service provider, or CSP. For example, many AWS customers choose to run Amazon Relational Database Service (RDS) instances rather than creating a database as an Amazon Elastic Cloud Computing (EC2) instance. Although RDS frees AWS customers from administrative and management duties, until recently there were visibility gaps that prevented a full understanding of the traffic flowing in and out of RDS instances. By adding RDS to Amazon supported services, AWS now enables RDS users to gain packet-level visibility with VPC Traffic Monitoring.
Before we dive deeper into what RDS monitoring via traffic mirroring means for security in AWS—including use cases—let's briefly touch on the major components involved.
What Is a Relational Database Service (RDS)?
RDS instances deploy in platform-as-a-service (PaaS) environments, which host database management systems, development tools, and much more. As noted earlier, AWS customers who use RDS can avoid configuration, management, and maintenance of their database. Those databases include MySQL, PostgreSQL, MariaDB, Oracle BYOL, and SQL Server. RDS users can also build web and mobile apps or migrate apps to the cloud without the need to re-architect.
What is Amazon VPC Traffic Mirroring?
VPC Traffic Mirroring is the AWS equivalent of a port mirror or SPAN in that it copies network traffic for monitoring and inspection. It's an essential component for allowing network-based security tools to sit out of band and passively collect copies of packets from any asset with a network interface. Before AWS released their traffic mirroring service in 2019, you would need to deploy lightweight agents to gain access to network packets for threat detection, troubleshooting, investigation, forensics, and more.
How RDS Monitoring via Traffic Mirroring Works
Because RDS instances have a network interface, it's possible to mirror traffic from them and deliver that traffic to a sensor for analysis. For example, the image below shows a workflow in which mirrored traffic is sent from an RDS instance to an ExtraHop Reveal(x) 360 sensor.
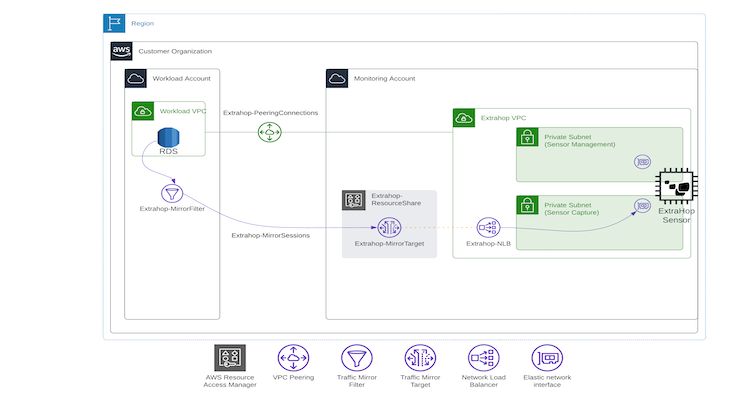
Workflow for using ExtraHop and Amazon VPC Traffic Mirroring for RDS visibility.
Benefits of Enhanced RDS Visibility
By providing coverage of RDS instances, packets can power cloud threat detection, whether via rules or behavioral modeling. Packets also provide insight into how much traffic passes through an RDS instance, how long those transactions take, and the content of that traffic, adding context to investigations. And unlike logs, which can be disabled or destroyed by savvy attackers, packets are an always-on data source. If your packet-based security tool offers decryption—an essential element of cloud and hybrid security—you can get all that information even if the traffic is SSL/TLS encrypted.
Why Packets Matter for RDS Security and Observability
Traditionally, security teams needed to rely on logs for visibility into RDS instances. While logs can provide surface-level insight, packets enable you to dig much deeper. The difference is easy to sum up with a simple analogy. Logs are like a phone bill—they tell you who your RDS instance talked to and for how long. Packets are like tapping a phone call. Not only do packets let you know who the RDS instance talked to and for how long, they also tell you what they said. And if your network-based security tool has the ability to ingest and analyze multiple sources of network telemetry such as packets and VPC Flow Logs, you gain broad coverage and deep visibility in a single UI. This unified approach to layered threat defense enables you to manage serverless security risk across environments.
Learn More About Layered Threat Defense for AWS
RDS Monitoring Use Case: Threat Detection
Let's dive into a real-world use case that should help clarify the value of packet-level visibility into RDS transactions. In this example, we're going to use ExtraHop Reveal(x) 360, our network-based hybrid and multicloud security solution.
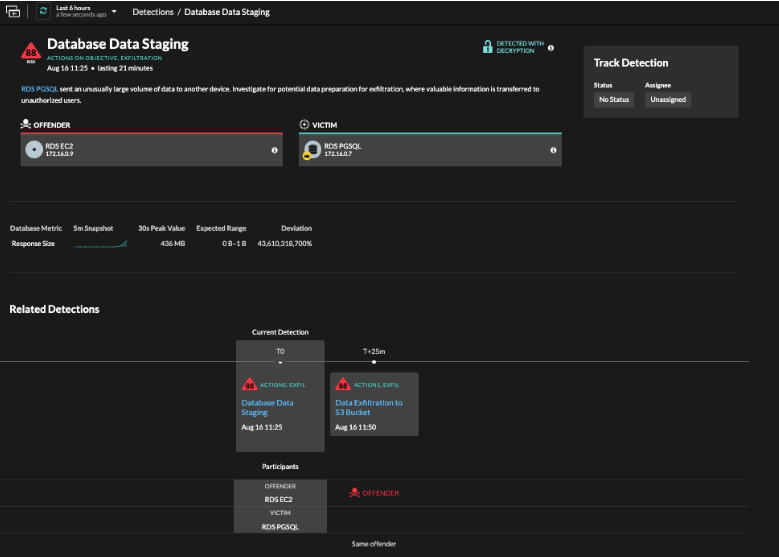 Example of a Database Data Staging detection featuring the offending EC2 instance and a PostgreSQL database in an RDS instance.
Example of a Database Data Staging detection featuring the offending EC2 instance and a PostgreSQL database in an RDS instance.
Reveal(x) 360 analyzes traffic from a PostgreSQL database on RDS to map relationships and establish baseline behaviors. While monitoring the database, the Reveal(x) 360 detects an unusual interaction between an EC2 instance and the PostgreSQL instance. Because Reveal(x) 360 analyzes traffic flowing in and out of the RDS instance with cloud-scale ML to establish behavioral baselines, it's able to detect anomalous behaviors and create an alert. You can then investigate and determine that the abnormal behavior occurred in a data staging attempt that's part of a larger data exfiltration attempt. With the ability to drill down into packets, you can also significantly reduce mean time to response (MTTR) with forensics.
Additional Packet-Based RDS Use Cases
Hybrid Cloud Visibility: If you have an on-premises application server communicating with an RDS instance in AWS, you can now monitor and analyze that traffic using packets. Previously, VPC Traffic Mirroring would not provide visibility into an on-prem app reaching across the internet.
Performance Monitoring: In addition to security use cases, packet visibility into RDS instances unlocks performance monitoring and diagnostics to quickly identify performance issues. You can keep your CSP honest regarding RDS performance by measuring the performance of every database and receiving process time metrics for every call.
Analyst Report: Pandemic Eleven: Top Threats to Cloud Computing
