cybersecurity for defense
and intelligence agencies
modernize and protect the mission
Drive modernization to preserve the cyber advantage.
Defend mission outcomes against advanced threats.
Achieve
Cyber
Resiliency
U.S. defense and intelligence agencies depend on mission-ready IT infrastructure to support the modern warfighter and our national defense.
The impact of one successful cyberattack or broken user experience risks a loss of crucial cyber advantage. As cyber adversaries grow in sophistication, any setbacks jeopardize mission objectives and ultimately our national security.
eBook: Why the Time is Right for Network and Security Collaboration
The ExtraHop Advantage for
Defense and Intelligence Agencies
Preserve the
Cyber Advantage
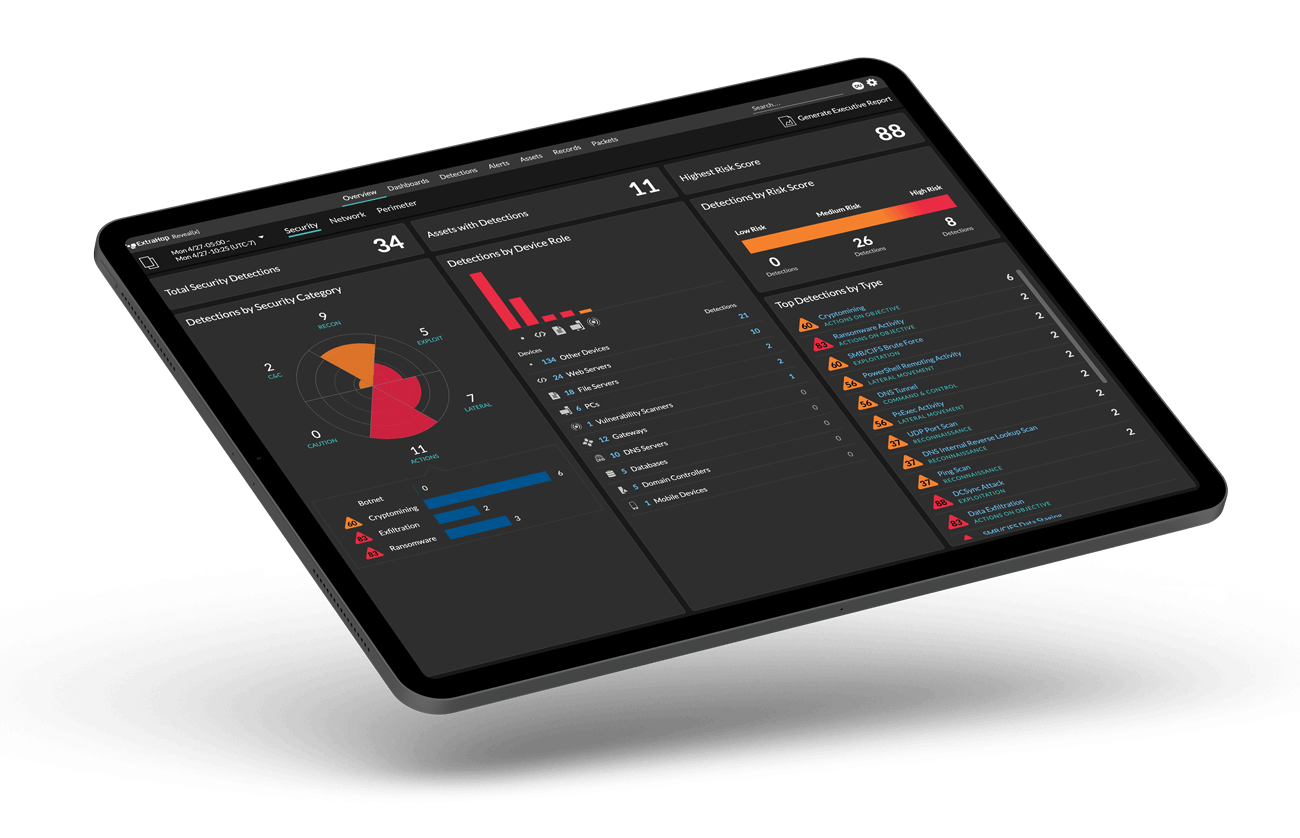
Strengthening and defending critical defense and intelligence IT infrastructure from advanced cyber threats and unplanned outages is no small task. With Reveal(x), your cyber protection and information network operations teams gain real-time network intelligence to detect and stop advanced threats.
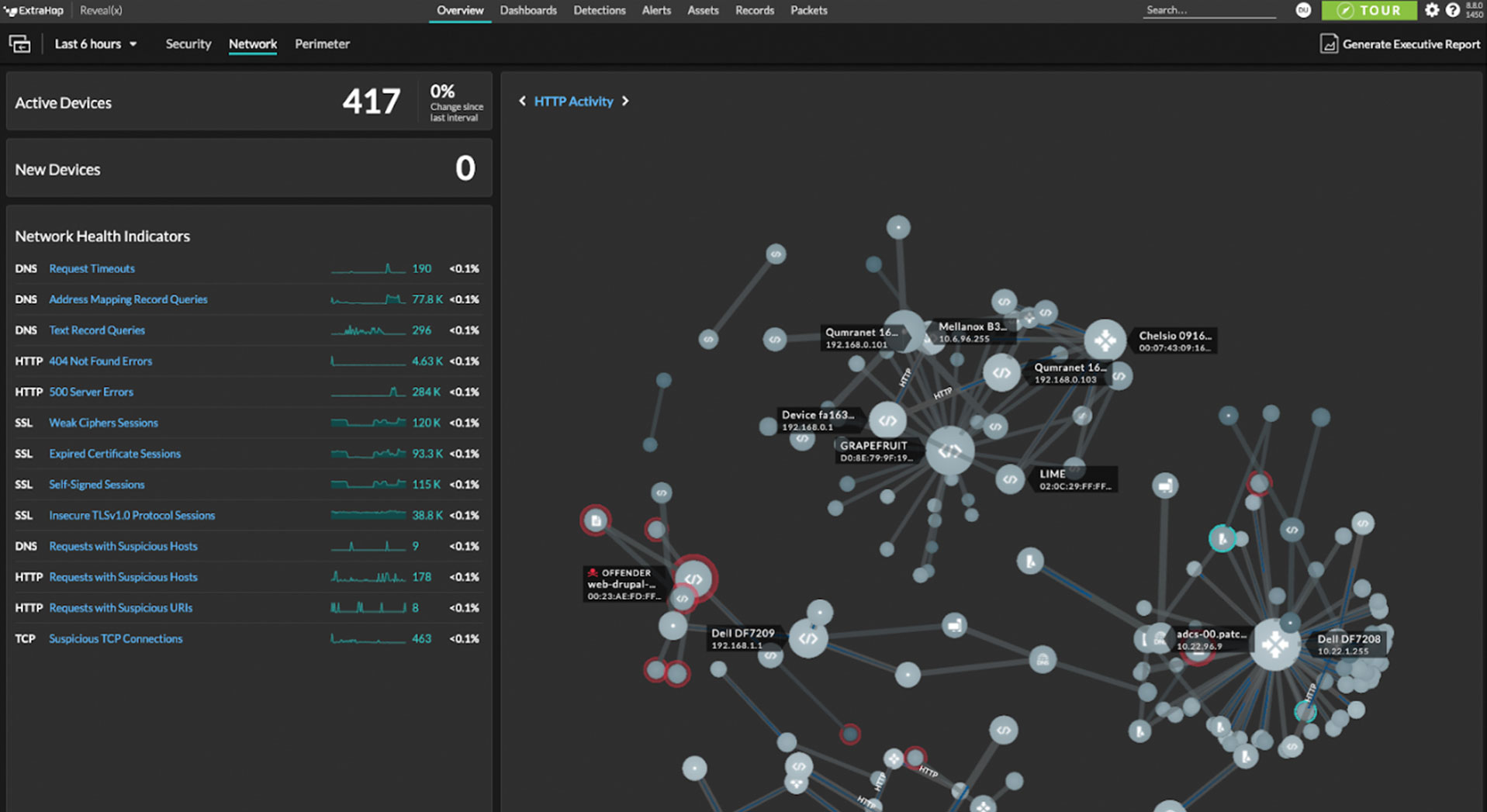
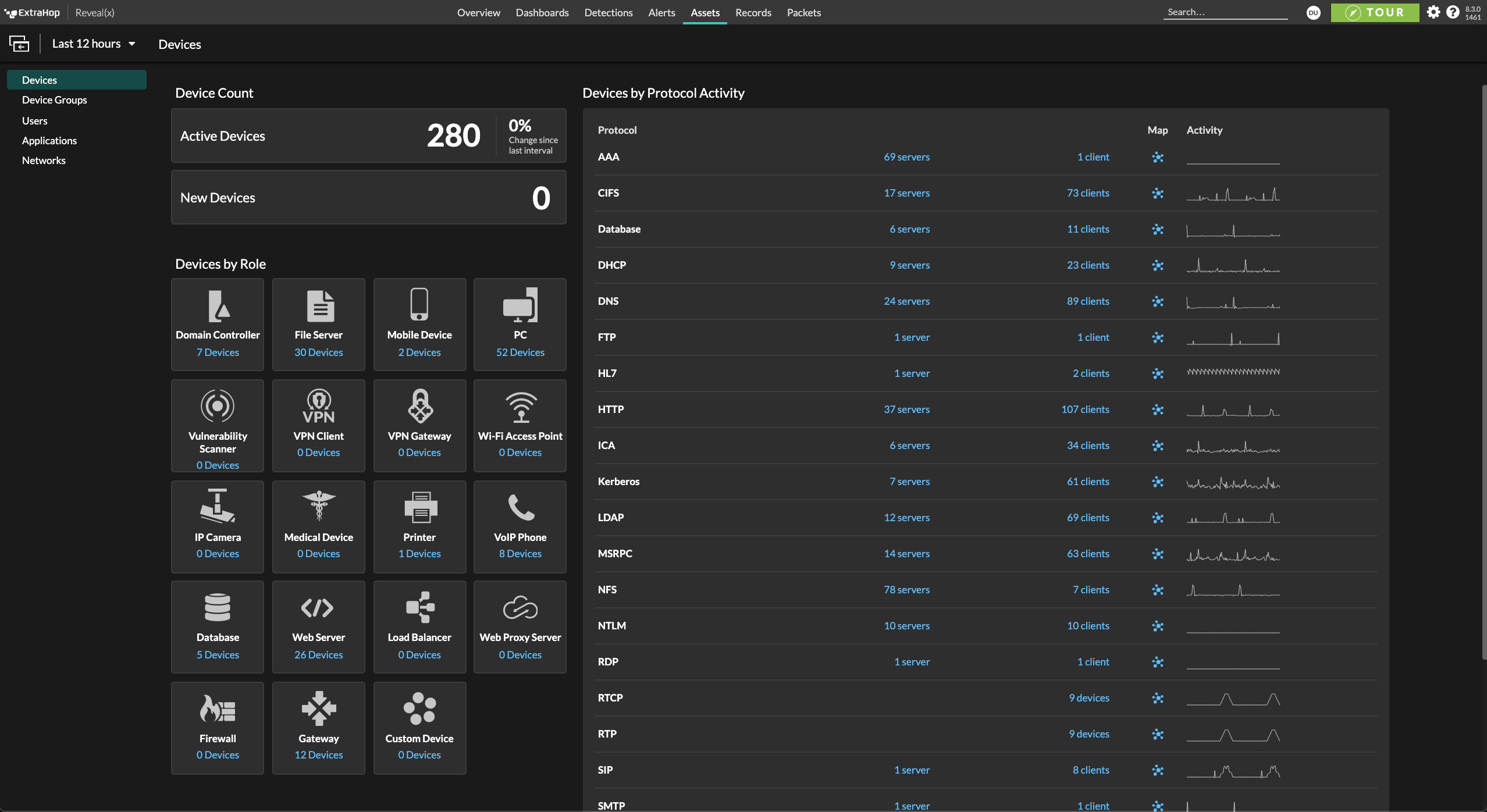
Reveal(x) passively monitors your entire IT environment—no matter how complex or distributed—to deliver complete visibility. As a trusted, single source of network situational awareness, Reveal(x) enables greater cooperation between cyber and network teams to accelerate incident response when every second counts.
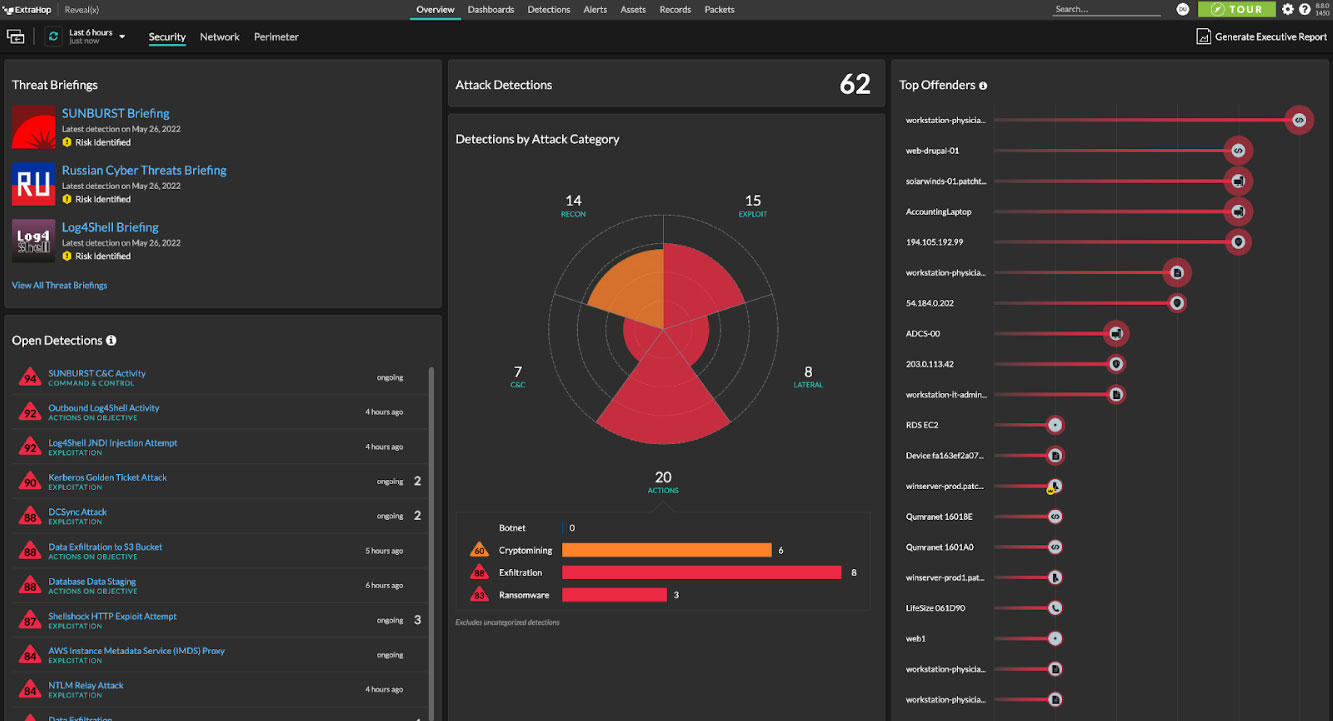
Once malicious cyber activity or a service interruption is detected, built-in workflows enable cyber defense incident responders to investigate alerts, respond fast, and share vital threat information in a few clicks.
Pick Your Poison, Get Your Antidote
Resources
White Paper
The Role of NDR in Public Sector Security Strategies
Solution Brief
Federal Cybersecurity Law Solution Brief | ExtraHop
Solution Brief
Stop Ransomware and Protect Vital Public Sector Services
Datasheet
Accelerate Zero Trust Adoption in the Public Sector with Reveal(x)
eBook
Why the Time is Right for Network and Security Collaboration
Solution Brief
ExtraHop Reveal(x) for U.S. Federal IT Networks
Be The Hunter.
Investigate a simulated attack unfolding in real time
using the full Reveal(x) product.