Cloud Threat Detection and Response
Advanced attacks are extremely
difficult to detect.
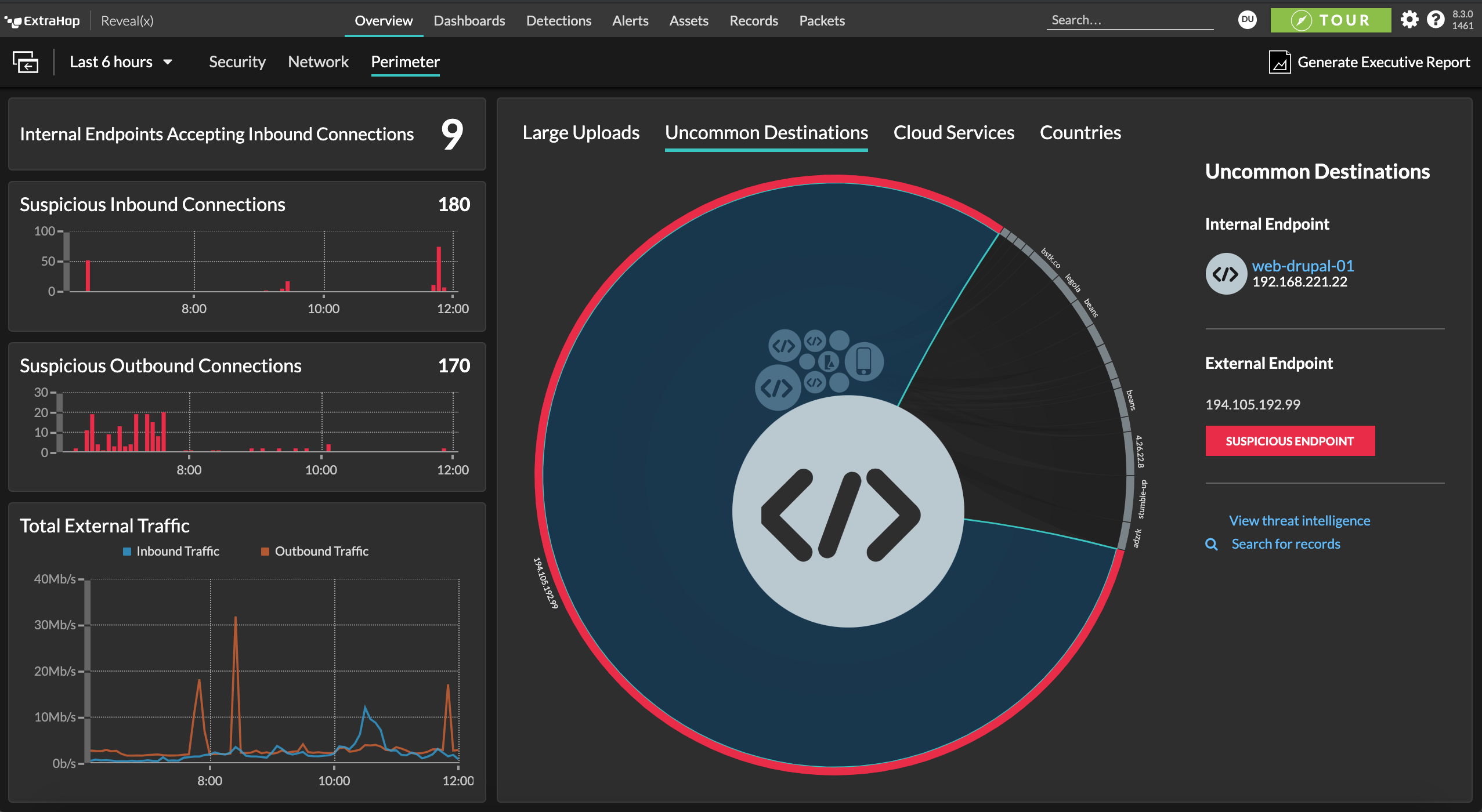
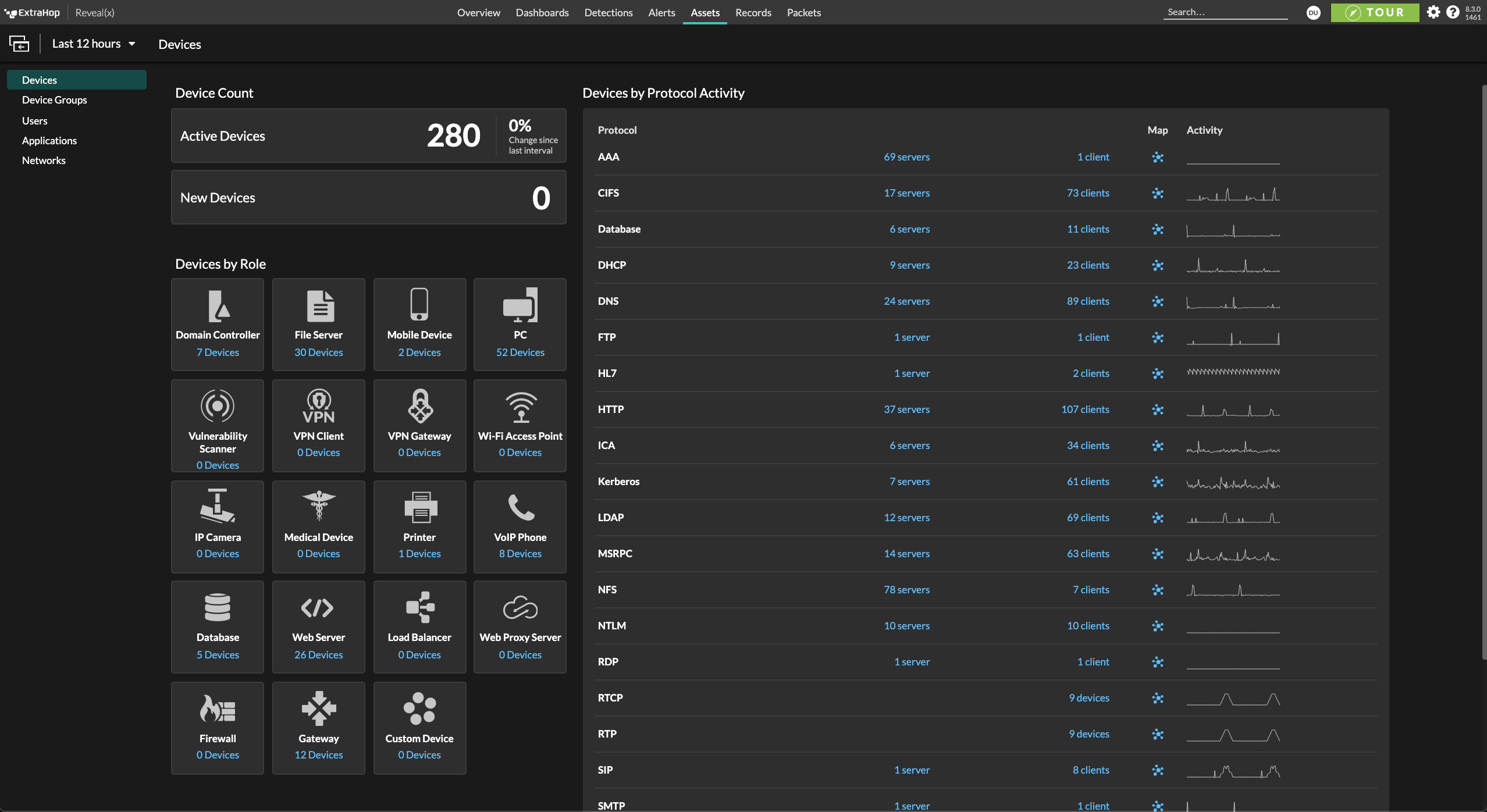
Once attackers compromise a cloud workload and steal credentials, most cloud security tools can't detect their lateral movement in the east-west corridor. Most cloud security tools only detect and apply threat intelligence for activity going forward, and not to past compromise activity. That blindness to post-compromise activity leads to longer dwell time, providing adversaries the days, weeks, or months they need to breach critical assets.
With ExtraHop Reveal(x)
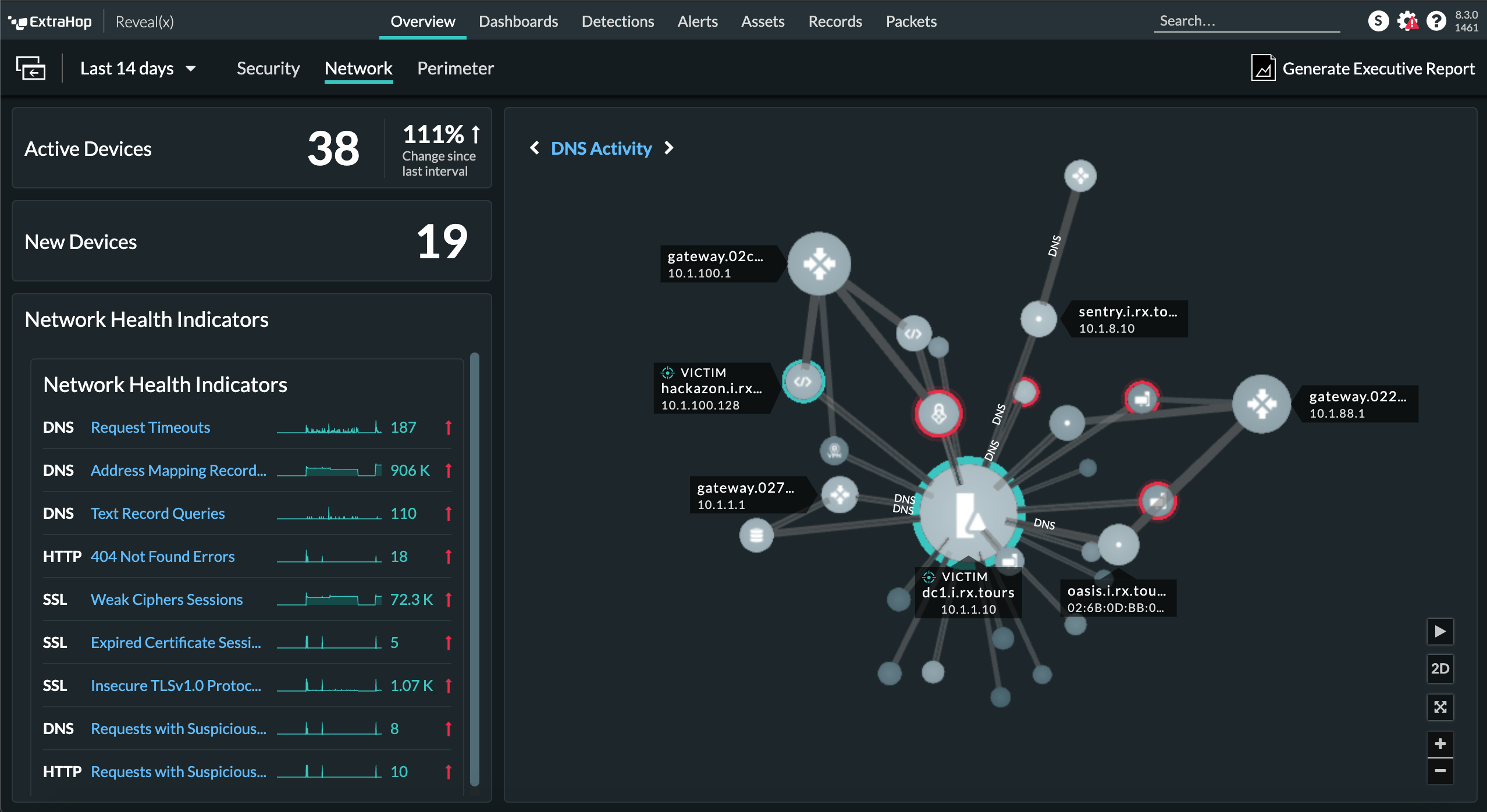
Detect lateral movement between cloud workloads
Reveal(x) 360 detects lateral movement between cloud workloads to uncover malicious behavior such as SSRF and CSRF payload attacks, credential enumeration, and data staging and exfiltration. Our intuitive UI adds context that streamlines investigations and enables productive threat hunting for analysts working at every level. And access to flow logs and packets provides broad coverage and deep visibility.