Monitor Third-Party Security Risk
Open source & third-party software increases organizational risk.
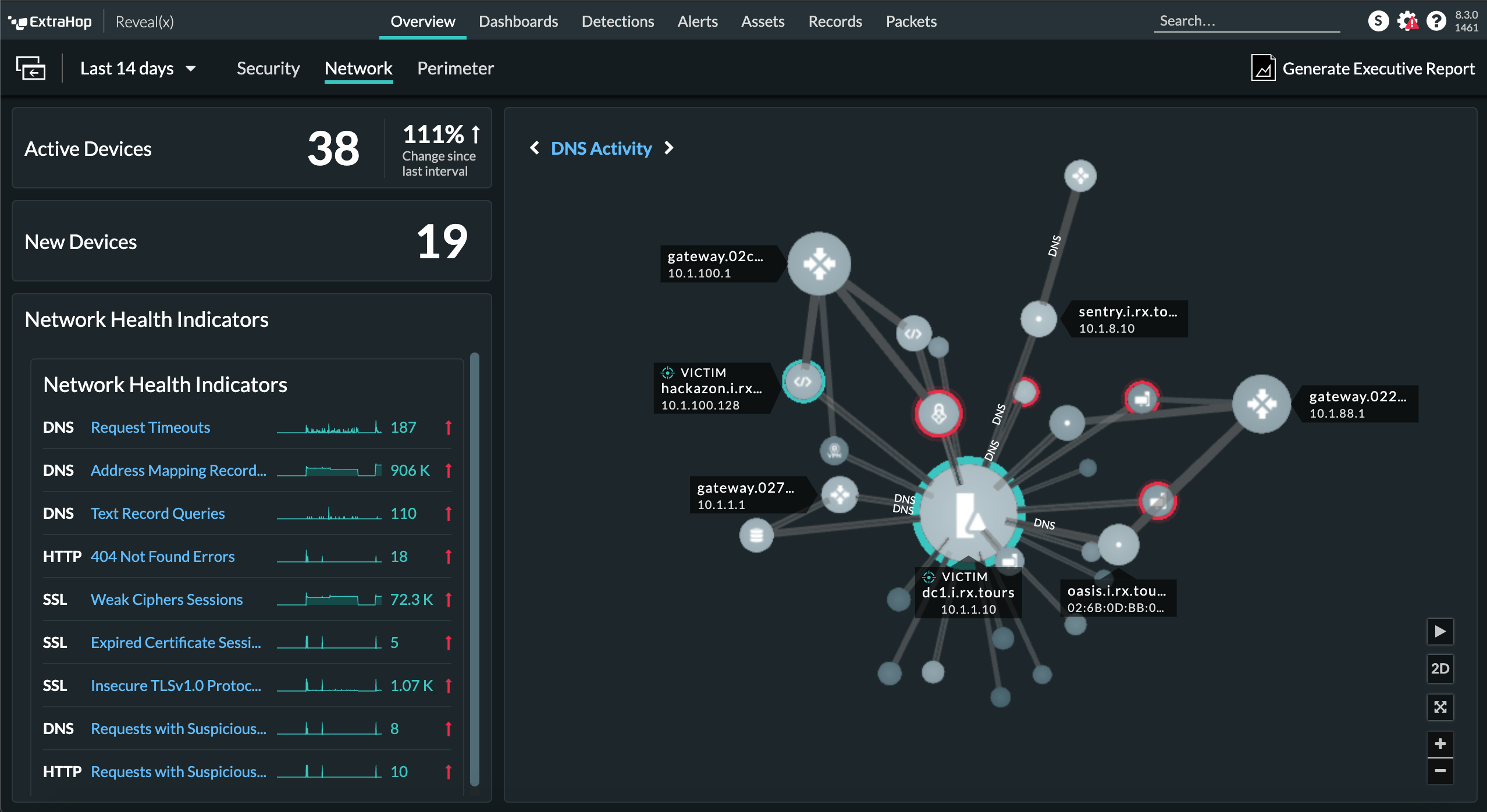
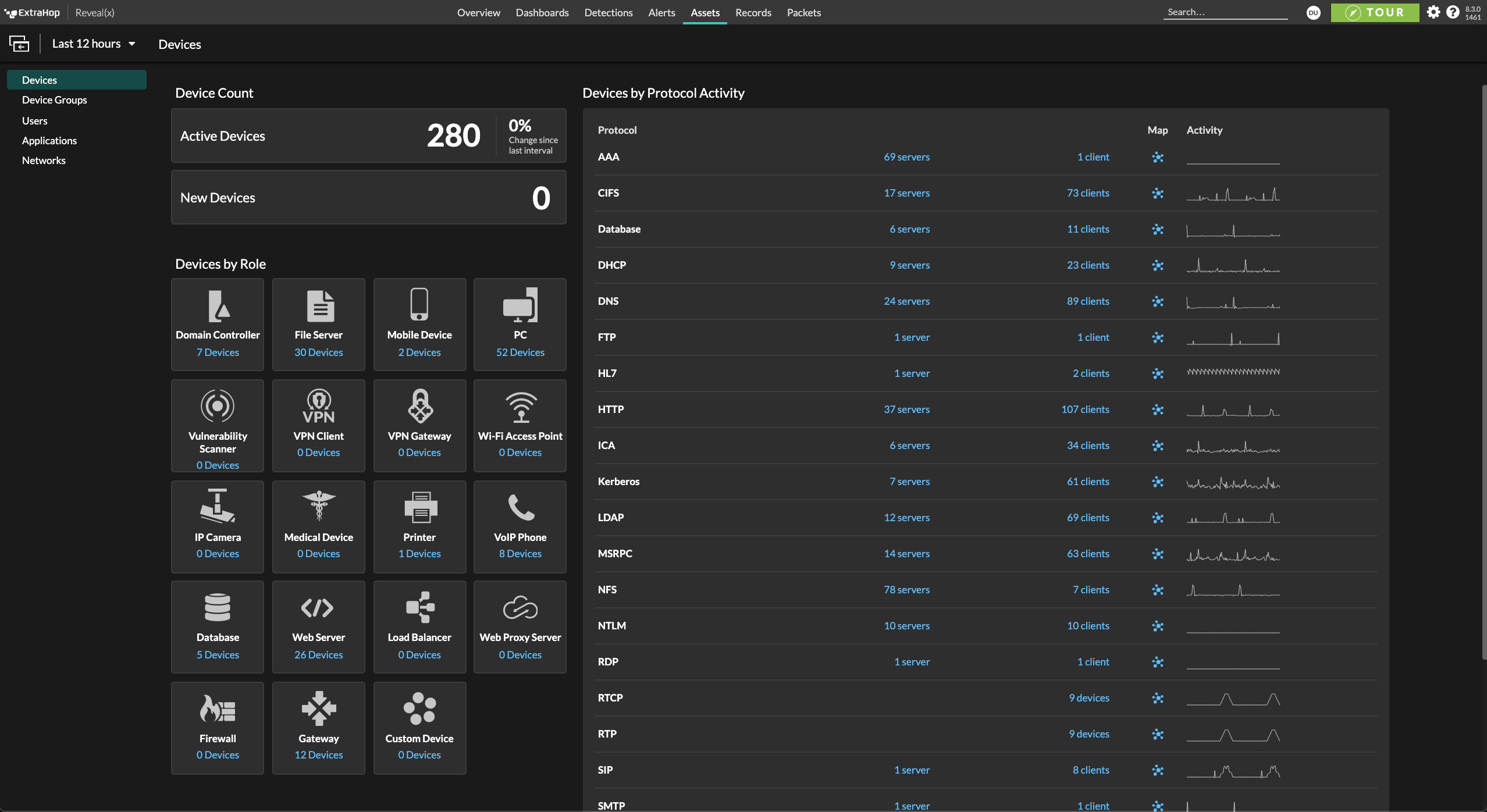
The shift to infrastructure-as-code for cloud deployment increases the risk of supply chain attacks. Reliance on open source and third-party software to build and deploy cloud workloads can expose you to serious vulnerabilities. It's impossible to keep every threat out of your cloud environment, and the odds of a successful breach increase with each new addition to your attack surface. Organizations need east-west visibility and AI-powered behavioral detections to identify the post-compromise activities used in almost every successful attack.
With ExtraHop Reveal(x)
Detect Unknown and Unexpected Communications
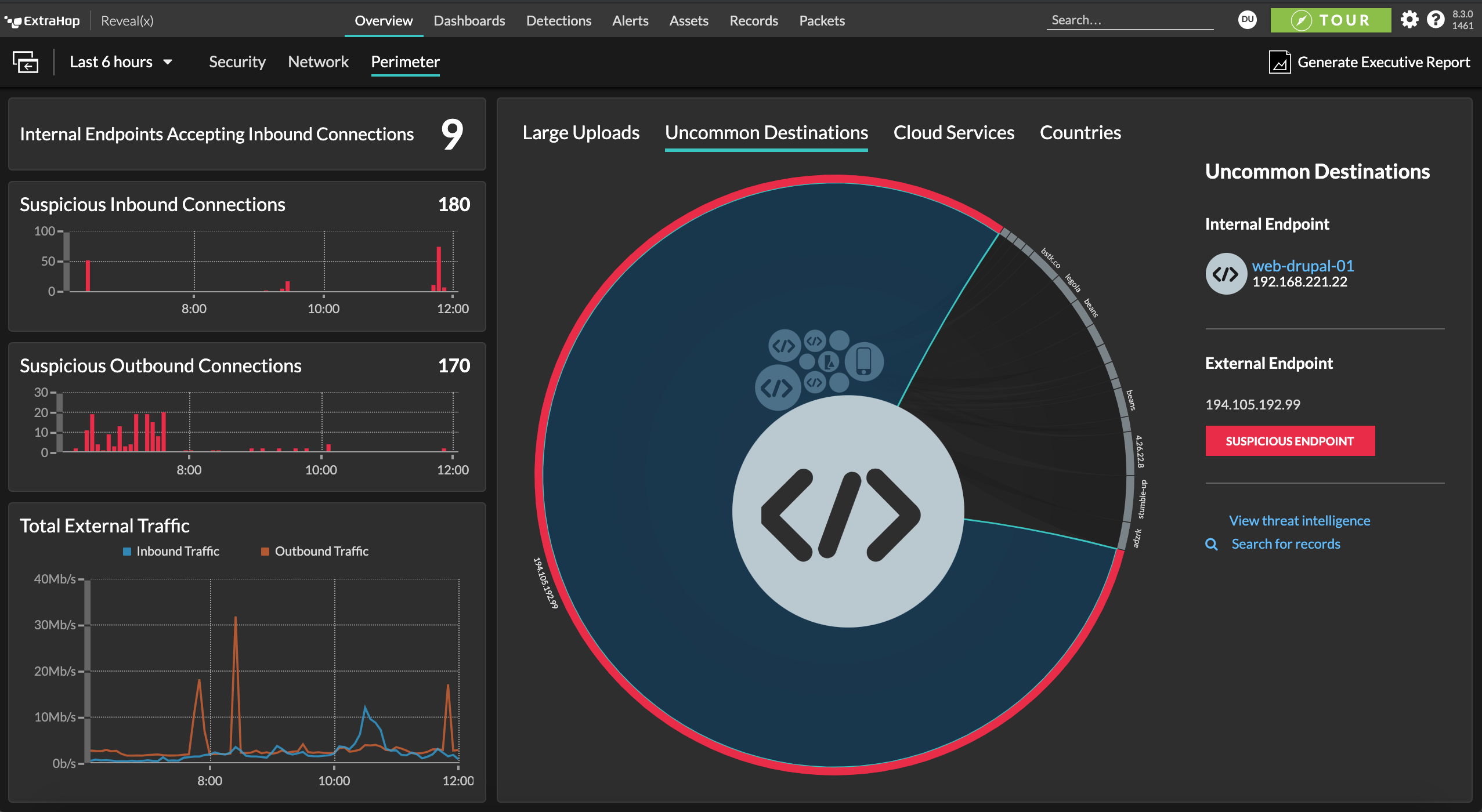
Reveal(x) 360 detects whether your production workloads are pulling updates when they shouldn't and examines unknown or unexpected communications. ExtraHop enables you to detect unusual activity and stop evasive and sophisticated attacks before they become breaches.
Get Answers to the Tough Questions
Assessments Provide
Time-Limited Protection
Every organization understands the value of due diligence and completing thorough third-party risk assessments at onboarding. And yet, only 40% of organizations say they have a thorough understanding of the risk of data breaches through third parties, according to PricewaterhouseCoopers. Those initial risk blindspots are compounded as time goes by. Risk is dynamic, making continuous third-party risk monitoring a critical element of your TPRM (third-party risk management) strategy. Reveal(x) 360 provides up-to-date insights on both the security hygiene of your third-party connections and on attacks actively leveraging third-party vectors.