ExtraHop Packet Forensics
Speed Up Investigations and Forensic Evidence Collection
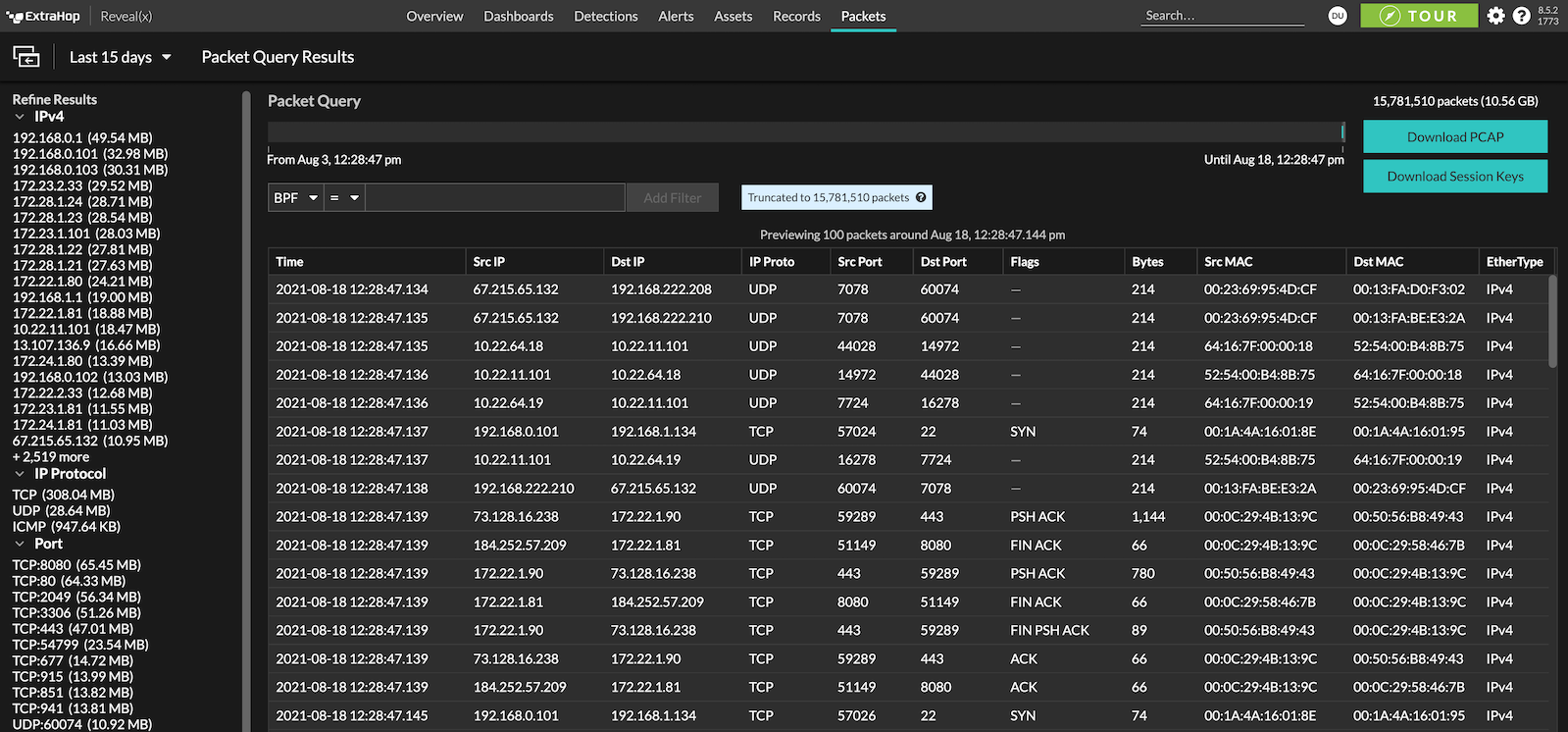
Packet capture plays a vital role in incident response, forensic investigation, and threat hunting, but it hasn't been easy, especially in cloud environments. Historically, collecting and analyzing packets was a complex, time-consuming, manual process that often involved multiple tools.
With ExtraHop Reveal(x)
Experienced Responders Depend on the Network for the Cyber Truth
Attacker obfuscation tactics have taught seasoned incident responders to be suspicious of server and endpoint logs when an intruder is in the midst. That's why experienced responders recognize that packets provide you with the unalterable ground truth.
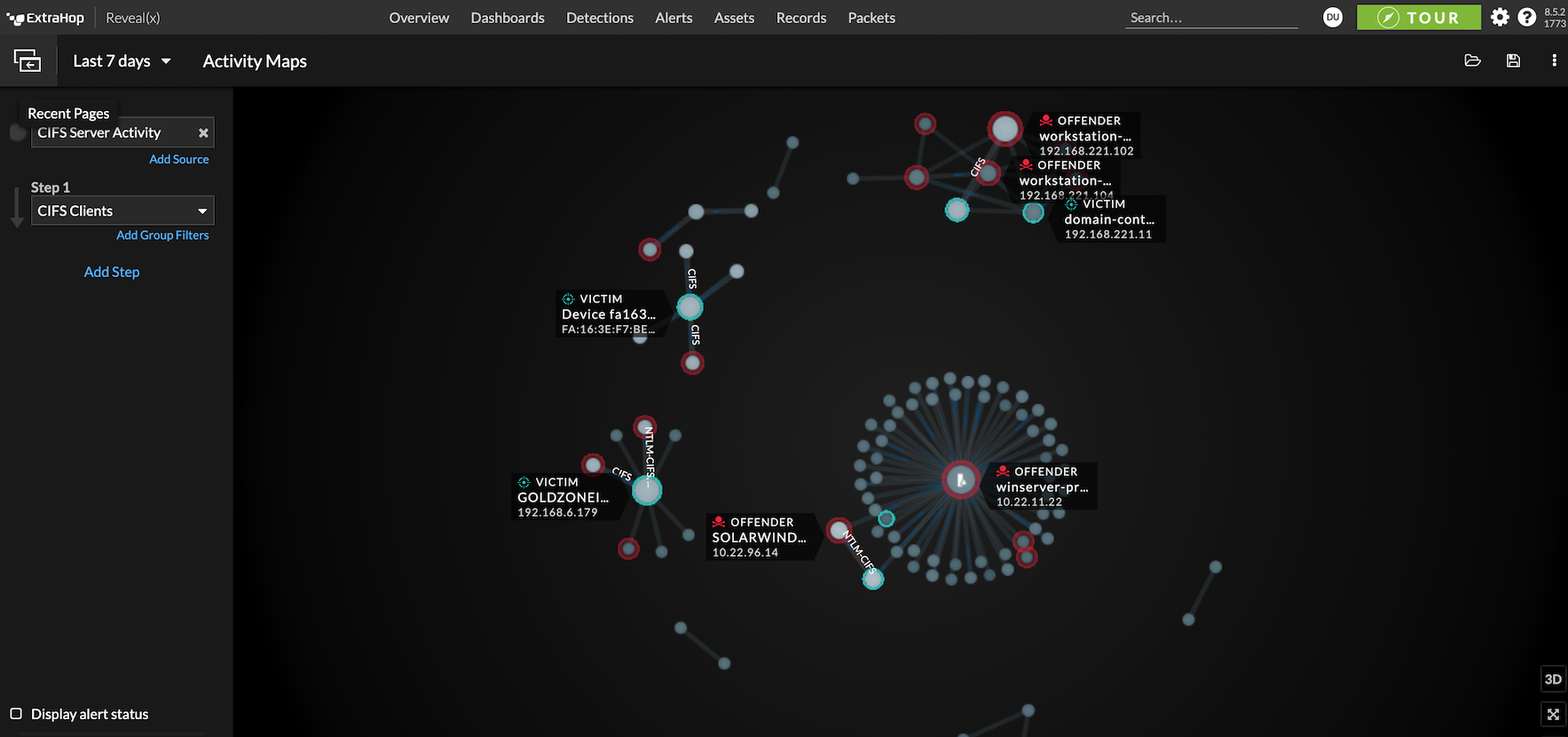
With ExtraHop Packet Forensics integrated with Reveal(x) NDR, incident responders jump into action with machine-learning powered, context-enriched alerts that attackers can't evade. Working with the scalable PCAP repository, responders take the guesswork out of impact scoping exploited assets and compromised data. This level of network packet visibility speeds up intruder eradication, business recovery and streamlines legal disclosures if needed.
Get Answers to the Tough Questions
Integrated Workflow
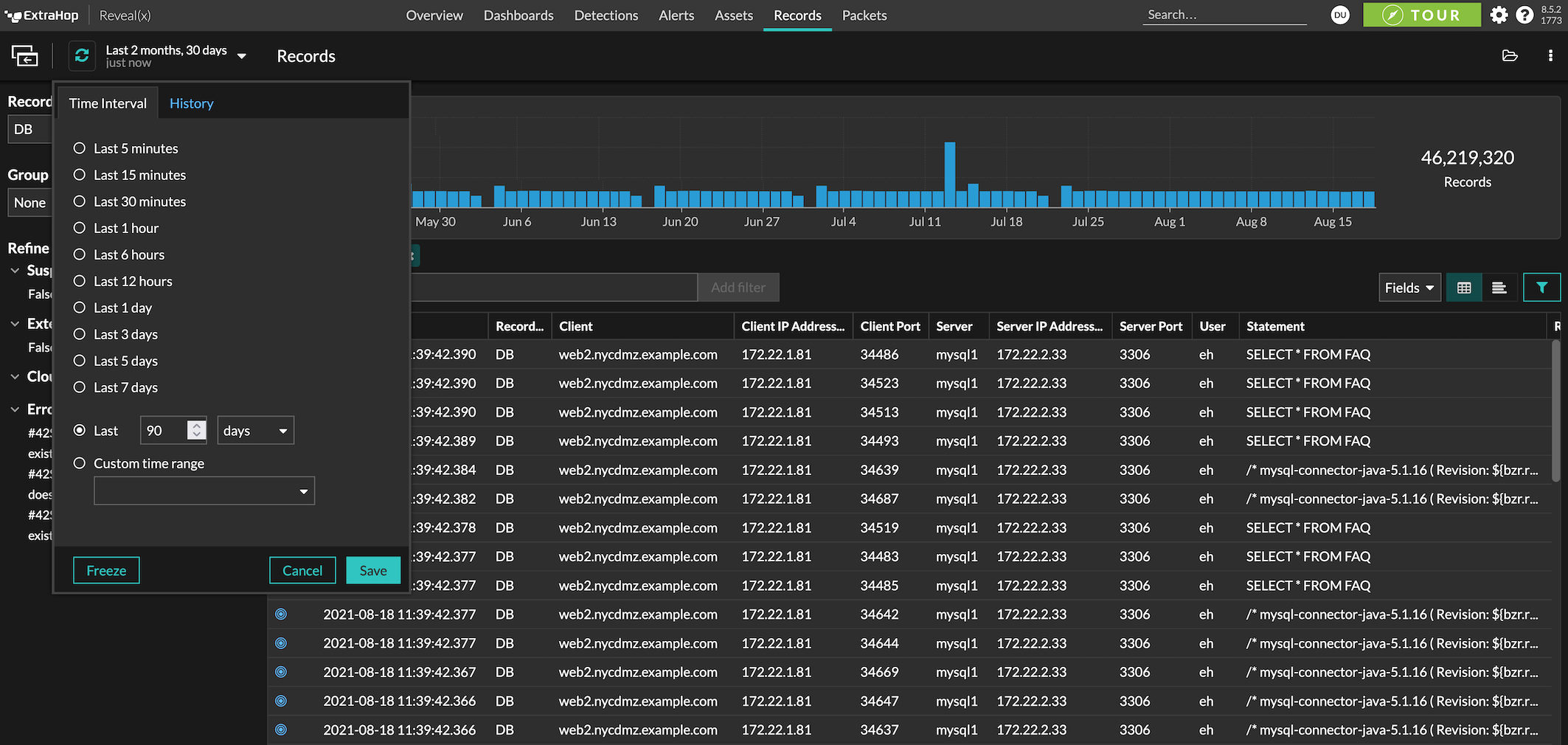
With detections, transaction records, and packets all indexed and searchable, analysts can expedite speed to resolution.
Decryption Capabilities
Uncover damaging attacker’s actions hiding in encrypted traffic, including TLS 1.3 PFS.
Maximize Resources
Fast queries and global search with an easy-to-use interface get answers without needing to be an expert.
Hybrid Cloud Environments
Capture packets across hybrid environments and provide definitive evidence and immediate answers for cloud security teams.
Chain-of-Custody Collection
Remove manual processes and the need for multiple products for root-cause analysis and fulfill evidence collection requirements.
Horizontally Scalable Solution
Modularly extend your PCAP archive as your requirements grow, up to petabytes of storage.
Use Cases
Accelerate zero trust initiatives
Effectively gather critical evidence for insider threat investigations.
Exceed compliance requirements
Stay ahead of the latest compliance requirements for full packet capture including NIST, PCI DSS, and more.
Application Troubleshooting
Reduce the MTTI (Mean Time To Innocence) and troubleshoot application issues faster.
Accelerate zero trust initiatives
Effectively gather critical evidence for insider threat investigations.
Exceed compliance requirements
Stay ahead of the latest compliance requirements for full packet capture including NIST, PCI DSS, and more.
Application Troubleshooting
Reduce the MTTI (Mean Time To Innocence) and troubleshoot application issues faster.