Implement Zero Trust
Your Zero Trust Architecture, Verified
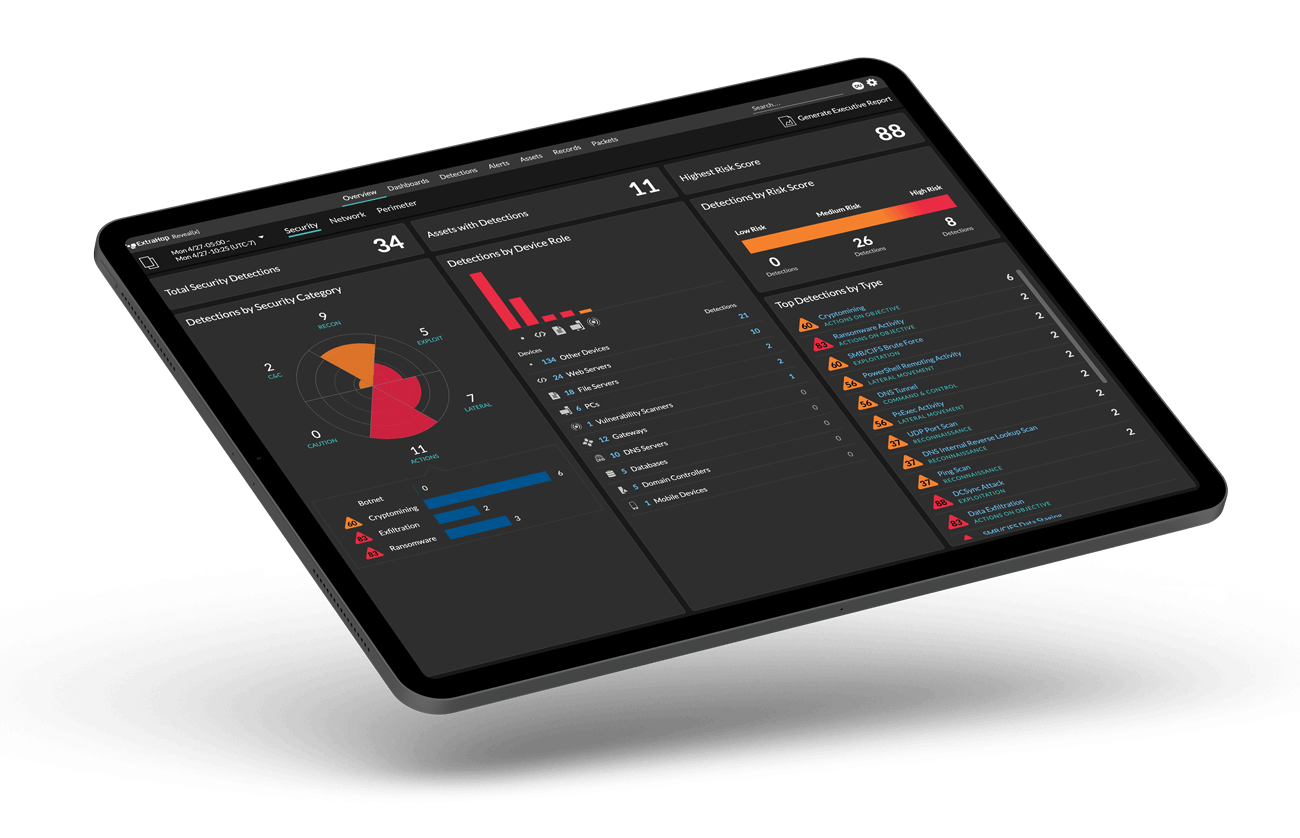
Creating a Zero Trust architecture requires in-depth knowledge of the network and what's connected to it.
Deep Dive: Zero Trust in the Public Sector
Consolidate.
Automate.
Orchestrate.
Win.
The concept of Zero Trust has been with us for over a decade. In a world where the network perimeter is no longer delineated nor secure, devices within the corporate network can no longer be blindly trusted. With increasingly advanced threats, a rapid transition to remote work, and the proliferation of cloud services and IoT devices, Zero Trust is now gaining traction worldwide. Users and devices must be dynamically and continuously authenticated and verified, with access to resources restricted according to least privilege principles.
But since Zero Trust is all about verification, how can you verify that all of your users, devices, and systems are following the framework? How do you know whether one of these controls is compromised? Network detection and response (NDR) can accelerate adoption of an effective Zero Trust framework by enhancing the IT visibility organizations need to get going. They can continually monitor and safeguard network traffic, validate policy enforcement, and support enhanced collaboration between traditionally siloed teams.
Eliminate
Blind Spots
Detect threats in real time with high-fidelity advanced machine learning and behavioral analysis. Validate policy enforcement by monitoring and safeguarding network traffic—including encrypted TLS traffic—at up to 100 Gbps.
Get 360
Degree Visibility
Gain complete visibility across hybrid networks, cloud transactions, and device types. Automatically discover every asset on the network and profile every managed and unmanaged device, including IoT endpoints.
Enhance
Collaboration
Improve analyst productivity and IT collaboration with a single integrated workflow that allows SecOps, NetOps, cloud, and DevSecOps teams to work together to quickly investigate and automate response.
With ExtraHop, we can easily search and identify unsecured connections, which lets us mitigate that threat before it ever becomes a problem.
MARVIN CHRISTENSEN
CIO,
NATIONAL IGNITION FACILITY
Want to See
For Yourself?
Stop data exfiltration, insider threats, and more
with the full product demo.